NEW YORK—Yesterday, Travelers hosted “Hacked: The Implications of a Cyber Breach,” a panel of the insurer’s top experts and outside consultants drilling down into the realities of the cyber threat.
According to Travelers’ brand new 2015 Business Risk Index, cybersecurity rose from the #5 threat in 2014 to the #2 threat perceived by business leaders, with 55% most concerned about malicious and criminal attacks.
In an exercise to show just how valid that concern it is, panelists Kurt Oestreicher, a member of the cyber fraud investigative services team at Travelers, and Chris Hauser, former Silicon Valley FBI agent and current member of the cyber fraud investigative services team at Travelers, successfully carried out a live hack. Using a fake website created for this demonstration, the experts staged an SQL injection attack—the same kind of attack as Heartbleed, these are still responsible for 97% of breaches. Using an open-source penetration testing program that Hauser described as “point and click hacking,” they easily found a way to tunnel into the site’s SQL database. The process of scanning for vulnerabilities and acting on a known exploit—in other words, conducting the actual, successful “hack”—took about two minutes, including the time Hauser spent talking the audience through the process.
The program used to conduct this hack was free, and the number of resources readily available for free or very low cost means that more everyday businesses will become victims as malicious actors face very few obstacles to attempt a hack. “As tools and techniques like this become more common, it becomes far easier to target small- and medium-sized businesses and that exposure increases, especially because there are such low costs up front,” said Oestreicher.
Every day in the United States, 34,529 of these known computer security incidents take place. Yet many go undetected, and a lot are willfully unreported. While larger breaches impact more records, the preponderance of breaches strike Main Street businesses, not Wall Street corporations. In fact, of those that are identified and reported, 62% of breaches impact small and medium-sized businesses, Travelers found. Increased awareness among this group has yet to translate into increased coverage, however. According to a survey by Software Advice, insurance penetration among this group hovers at just over 2%, a trend Mullen has seen in the field as well. “Only about 10% of those who should have that coverage actually do,” he said.
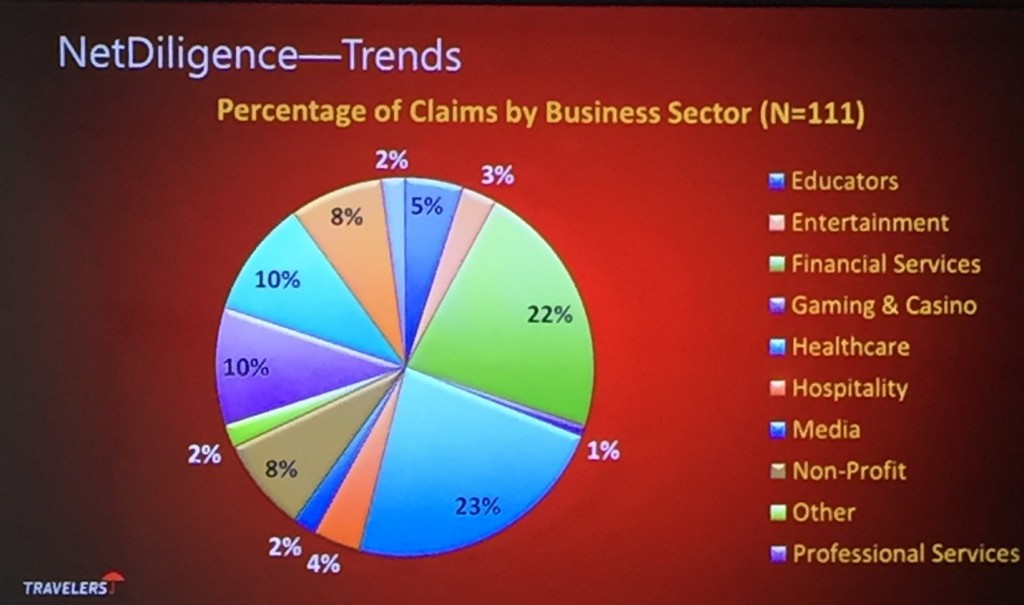
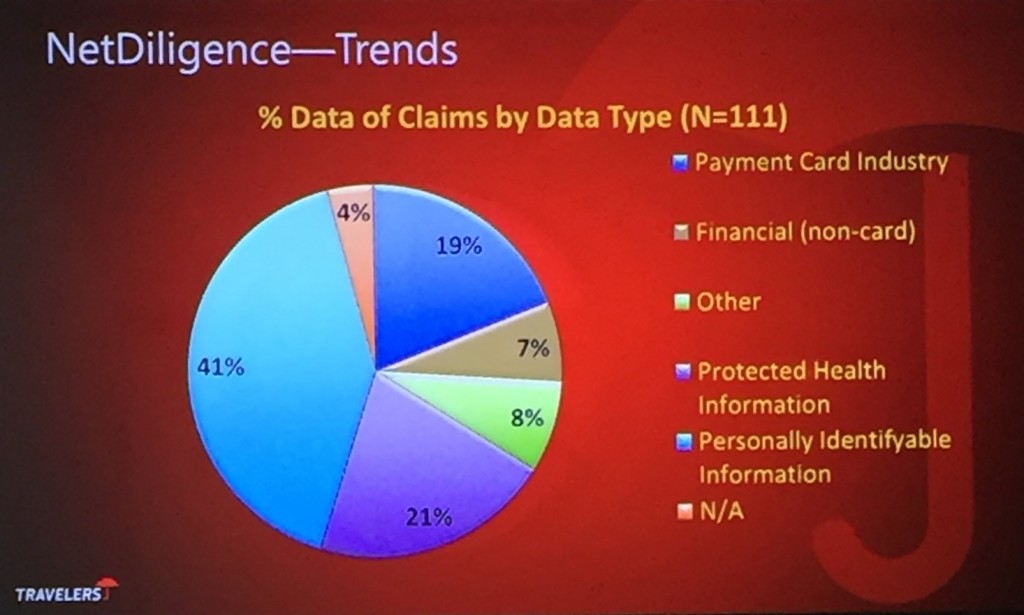
According to data from NetDiligence, those incidents that are covered by insurance break down as follows:
With hefty fines, costly investigation and notification requirements, and possible lawsuits and class actions, the true costs rapidly spiral. According to Mark Greisiger, president of data breach crisis services and security practices company NetDiligence, the average cost of a breach is $733,000 for SMBs—before any possible lawsuits or fines. Per record, the cost ranges from 1 cent to $1,000, based on the type of information contained. The average legal settlement after such breaches is currently about $550,000. Yet these numbers primarily reflect incidents where insurance was in place. Without the trusted vendor agreements, for example, the cost of retaining forensic investigation services in the midst of a crisis can be up to three times higher, he reported.
Recovering from these incidents varies wildly by the type of records exposed, and the resources available to aid in the effort. “It’s a wild pain in the butt with insurance,” said breach coach John Mullen, a managing partner of the Philadelphia Regional Office and chair of the U.S. Data Privacy and Network Security Group at Lewis Brisbois Brisgaad & Smith. “Without insurance, it’s a small- and medium-sized business killer. The Main Street story is a $2 million bill and no business.”
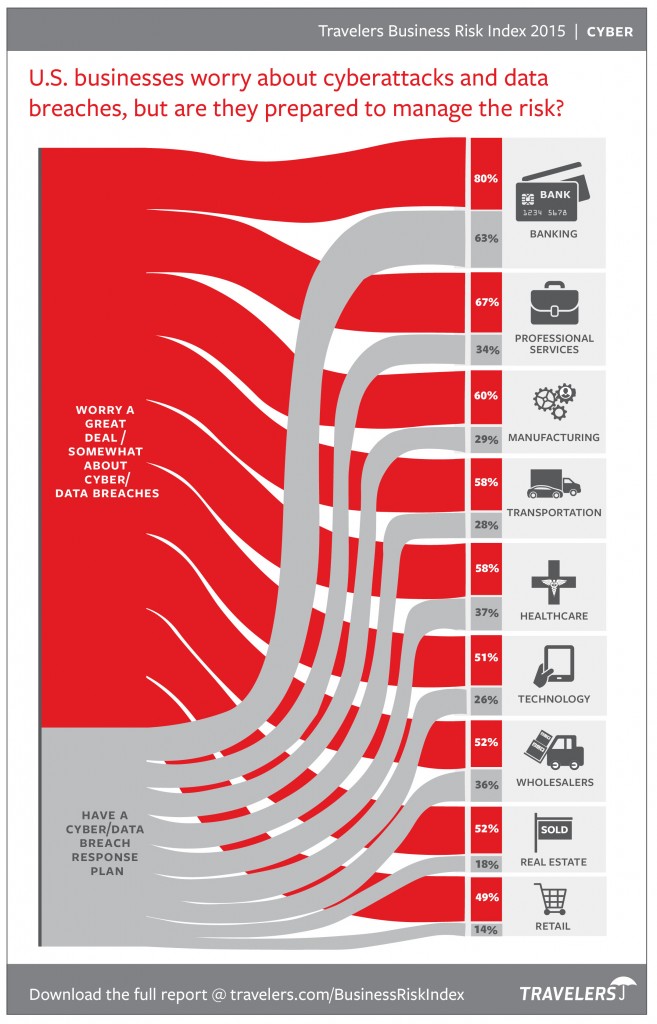
In the 2015 Business Risk Index, Travelers also shared a more detailed view of preparedness among specific industries: