In 2015, cybercriminals will increasingly be non-state actors who monitor and collect data through extended, targeted attack campaigns, McAfee Labs predicts. In the group’s 2015 Threats Predictions, Intel Security identified internet trust exploits, mobile, internet of things and cyber espionage as the key vulnerabilities on next year’s threat landscape.
“The year 2014 will be remembered as ‘the Year of Shaken Trust,’” said Vincent Weafer, senior vice president of McAfee Labs. “This unprecedented series of events shook industry confidence in long-standing Internet trust models, consumer confidence in organizations’ abilities to protect their data, and organizations’ confidence in their ability to detect and deflect targeted attacks in a timely manner. Restoring trust in 2015 will require stronger industry collaboration, new standards for a new threat landscape, and new security postures that shrink time-to-detection through the superior use of threat data. Ultimately, we need to get to a security model that’s built-in by design, seamlessly integrated into every device at every layer of the compute stack.”
McAfee Labs predicts the top cybersecurity threats in 2015 will be:
1. Increased use of cyber warfare and espionage tactics. Cyber espionage attacks will continue to increase in frequency as long-term players will become stealthier information gatherers, while newcomers to cyber-attack capabilities will look for ways to steal sensitive information and disrupt their adversaries.
- Established nation-state actors will work to enhance their ability to remain hidden on victim systems and networks.
- Cybercriminals will continue to act more like nation-state cyber espionage actors, focusing on monitoring systems and gathering high-value intelligence on individuals, intellectual property, and operational intelligence.
- McAfee Labs predicts that more small nation states and terror groups will use cyber warfare.
2. Greater Internet of Things attack frequency, profitability, and severity. Unless security controls are built-in to their architectures from the beginning, the rush to deploy IoT devices at scale will outpace the priorities of security and privacy. This rush and the increasing value of data gathered, processed, and shared by these devices will draw the first notable IoT paradigm attacks in 2015.
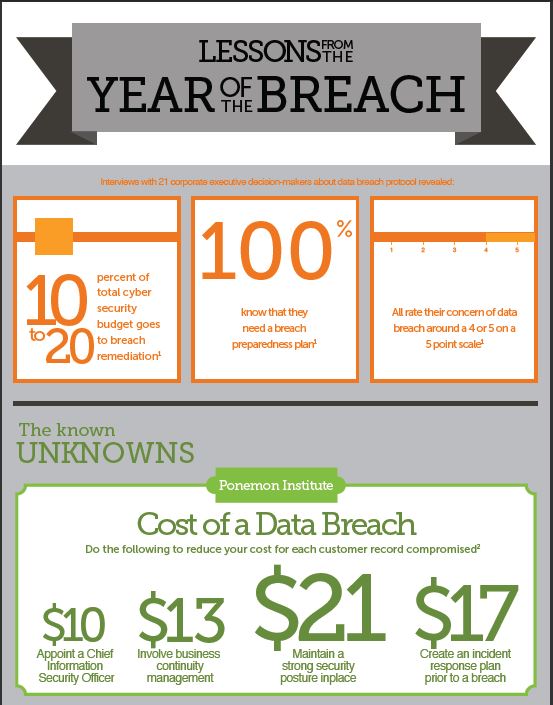
- The increasing proliferation of IoT devices in environments such as health care could provide malicious parties access to personal data even more valuable than credit card data. For instance, according to the McAfee Labs report entitled Cybercrime Exposed: Cybercrime-as-a-Service, the cybercrime community currently values stolen health credentials at around $10 each, which is about 10 to 20 times the value of a stolen U.S. credit card number.
3. Privacy debates intensify. Data privacy will continue to be a hot topic as governments and businesses continue to grapple with what is fair and authorized access to inconsistently defined “personal information.”
- In 2015 we will see continued discussion and lack of clarity around what constitutes “personal information” and to what extent that information may be accessed and shared by state or private actors.
- We will see a continued evolution in scope and content of data privacy rules and regulations, we may even see laws begin to regulate the use of previously anonymous data sets.
buy isotroin online blackmenheal.org/wp-content/uploads/2023/10/jpg/isotroin.html no prescription pharmacy- The European Union, countries in Latin America, as well as Australia, Japan, South Korea, Canada, and many others may enact more stringent data privacy laws and regulations.
4. Ransomware evolves into the cloud. Ransomware will evolve its methods of propagation, encryption, and the targets it seeks. More mobile devices are likely to suffer attacks.
- We predict ransomware variants that manage to evade security software installed on a system will specifically target endpoints that subscribe to cloud-based storage solutions.
buy prograf online blackmenheal.org/wp-content/uploads/2023/10/jpg/prograf.html no prescription pharmacy- Once the endpoint has been infected, the ransomware will attempt to exploit the logged-on user’s stored credentials to also infect backed-up cloud storage data.
- We expect the technique of ransomware targeting cloud-backed-up data to be repeated in the mobile space.
- We expect a continued rise in mobile ransomware using virtual currency as the ransom payment method.
5. New mobile attack surfaces and capabilities. Mobile attacks will continue to grow rapidly as new mobile technologies expand the attack surface.
- The growing availability of malware-generation kits and malware source code for mobile devices will lower the barrier to entry for cybercriminals targeting these devices.
- Untrusted app stores will continue to be a major source of mobile malware. Traffic to these stores will be driven by “malvertising,” which has grown quickly on mobile platforms.
6. POS attacks increase and evolve with digital payments. Point of sale (POS) attacks will remain lucrative, and a significant upturn in consumer adoption of digital payment systems on mobile devices will provide new attack surfaces that cybercriminals will exploit.
- Despite current efforts by retailers to deploy more chip-and-pin cards and card readers, McAfee Labs sees continued growth in POS system breaches in 2015 based on the sheer numbers of POS devices that will need to be upgraded in North America.
- Near field communications (NFC) digital payment technology will become an entirely new attack surface to exploit, unless user education can successfully guide users in taking control of NFC features on their mobile devices.
7. Shellshock sparks Unix, Linux attacks. Non-Windows malware attacks will increase as a result of the Shellshock vulnerability.
- McAfee Labs predicts that the aftershocks of Shellshock with be felt for many years given the number of potentially vulnerable Unix or Linux devices, from routers to TVs, industrial controllers, flight systems, and critical infrastructure.
- In 2015, this will drive a significant increase in non-Windows malware as attackers look to exploit the vulnerability.
8. Growing exploitation of software flaws. The exploitation of vulnerabilities is likely to increase as new flaws are discovered in popular software products.
- McAfee Labs predicts that exploitation techniques such as stack pivoting, return- and jump-oriented programming, and a deeper understanding of 64-bit software will continue to drive the growth in the number of newly discovered vulnerabilities, as will the volume of malware that exploits those newly discovered vulnerabilities.
9. New evasion tactics for sandboxing. Escaping the sandbox will become a significant IT security battlefield.
- Vulnerabilities have been identified in the sandboxing technologies implemented with critical and popular applications. McAfee Labs predicts a growth in the number of techniques to exploit those vulnerabilities and escape application sandboxes.
buy xifaxan online blackmenheal.org/wp-content/uploads/2023/10/jpg/xifaxan.html no prescription pharmacy- Beyond application sandboxing, McAfee Labs predicts that 2015 will bring malware that can successfully exploit hypervisor vulnerabilities to break out of some security vendors’ standalone sandbox systems.