Being aware of your company’s new and changing risks is critical for sound risk management. As the year progresses, we have identified growing risks facing
companies, and their directors and officers, that are likely to impact policyholders. These risks include cybersecurity, Telephone Consumer Protection Act (TCPA) lawsuits, drones, wage and hour lawsuits and food recalls. The risks and issues to watch out for are expanded below:
Cybersecurity
Cyberattacks against businesses doubled in 2015 and are expected to continue to increase as attackers become even more sophisticated. Watch out for:
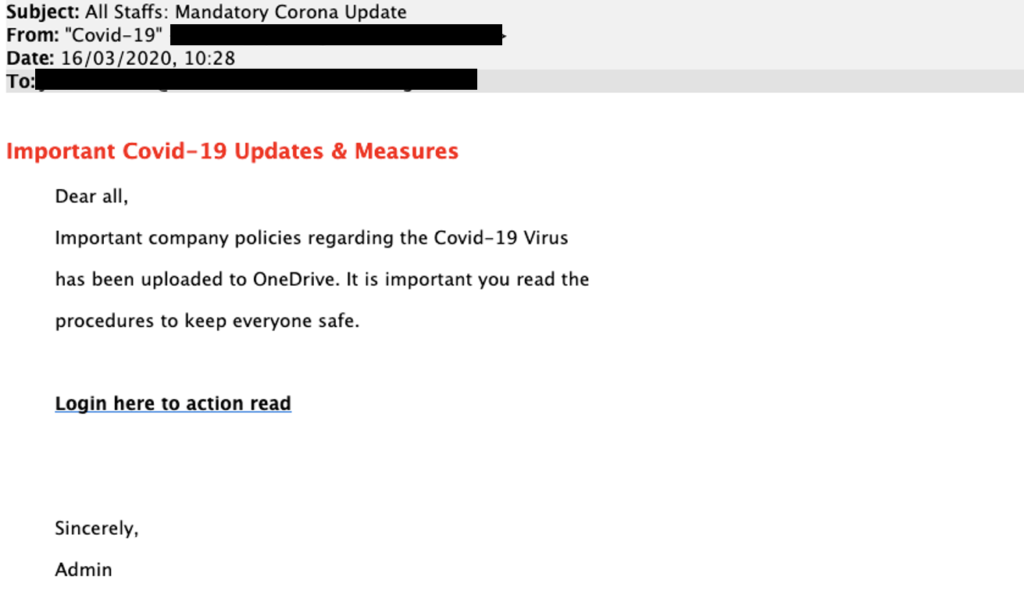
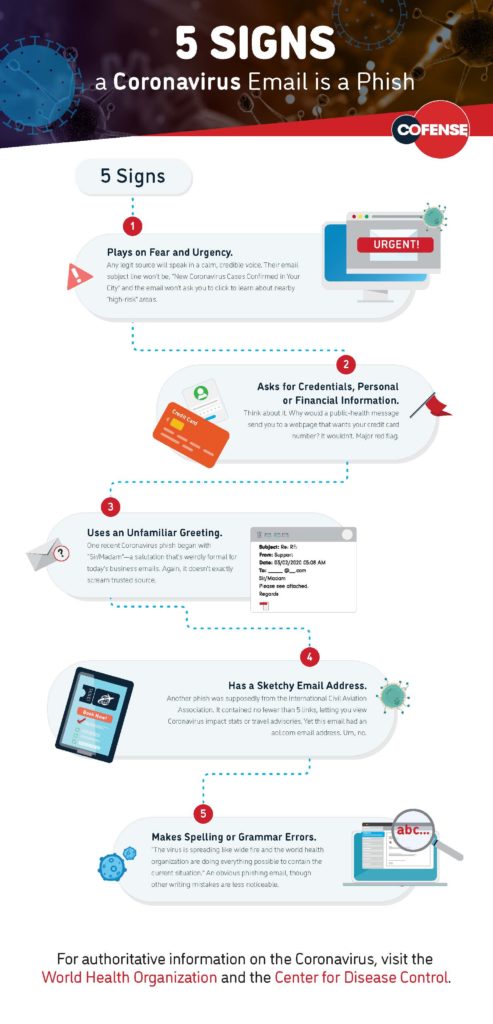
Phishing scams and social engineering fraud. In social engineering scams, hackers utilize phishing, purporting to be legitimate employees or third parties try to trick businesses into wiring funds or allow access to their systems. Although many businesses have crime insurance that covers “computer systems fraud,” ambiguous provisions or liability limits may restrict coverage. Som e courts have held that fraud coverage applies only when intrusions are unauthorized, but not when an unwitting employee falls prey to an online scam.
e courts have held that fraud coverage applies only when intrusions are unauthorized, but not when an unwitting employee falls prey to an online scam.
Data breaches. Companies should also be conscious about their coverage for data breaches, which increasingly present significant exposures. Insurers often contest whether data breaches constitute “publication” of private information, and, if so, whether an insurer’s duty to defend applies. This is particularly important as the storage of consumer data is a lynchpin of many businesses’ operations and marketing.
Businesses need to ensure that their commercial insurance policies adequately cover their business risks and consider purchasing dedicated cyber policies.
Coverage for TCPA claims
Certain efforts to engage with consumers may come at a steep cost. Under the Telephone Consumer Protection Act (TCPA), businesses that send unsolicited faxes, voice calls or text messages to consumers may be held liable for at least $500 per violation.
General liability coverage of TCPA claims. In recent years, commercial general liability (CGL) insurers have increasingly added broad exclusions to their policies for TCPA claims. Moreover, courts are split on whether “right to privacy” coverage in CGL policies cover these claims. Some courts uphold coverage only for losses from incidents that divulge confidential information (secrecy-related claims), whereas others uphold coverage for unsolicited communications, even if they do not republish confidential information.
While such coverage may be restricted under CGL policies, policyholders may have coverage under their directors’ and officers’ (D&O) insurance.
LA Lakers test case for D&O coverage. In 2016, the Ninth Circuit will likely address this issue in an appeal by the Los Angeles Lakers. The franchise’s marketing campaign included sending unsolicited text messages to fans. When sued under the TCPA, the franchise sought coverage for its defense costs under its D&O policy. In April 2015, a California federal court rejected coverage, finding that the policy’s “invasion of privacy” exclusion precluded coverage.
As businesses seek to engage consumers directly through various media, they should consider whether their insurance protects against TCPA claims.
UAVs and Insurance in 2016
Unmanned aerial vehicles (UAVs), or drones, promise to revolutionize not just commerce but insurance as well. The United States Federal Aviation Administration (FAA) estimates that, by 2023, annual global spending on UAVs will total $11.5 billion, and by 2020, about 30,000 commercial and civil drones will dot the skies.
Drone property loss and liability. The rise of drones raises several risks. The most obvious of these risks are loss of property and third-party liability. Use of drones for package or cargo delivery raises the risk of damage to the UAV itself—or its payload, which is usually the bigger loss. As shown by recent news reports and the first lawsuit, Boggs v. Merideth (W.D. Ky.), operators face liability for costs of defense and settlements or judgments payable to third-party claimants when UAVs go astray. With drones’ ability to film and collect data, other risks include privacy-related claims and data breach and hacking.
New coverage provisions. In June 2015, the Insurance Services Office, Inc. (ISO), approved new coverage provisions addressing commercial use of drones. The new ISO provisions modify standard CGL and umbrella/excess liability policy forms and merit close consideration by policyholders.
Because these new provisions are untested, policyholders should review them carefully against their entire insurance program and consult with insurance advisors to ensure that new provisions or policies provide the protection needed. Companies using UAVs should consider the aviation insurance market and also assess the need for cyber insurance coverage for privacy and data-breach exposures.
Wage-and-Hour Lawsuits
Cases alleging violations of the Fair Labor Standards Act (FLSA) have shot up in recent years. In 2015, almost 9,000 FLSA cases were filed in federal court, up more than 10% from 2014, and 30% from 2011. State courts have also experienced high volumes of wage-and-hour cases. California and New York recently enacted laws that allow directors, officers, and in New York, “top 10 shareholders” to be held personally liable for wage-and-hour violations.
Traditionally, companies have looked to their employment practices liability (EPL) and D&O insurance to protect against the defense and liability costs in wage-and-hour lawsuits. However, EPL insurance policies today regularly exclude coverage for such claims. Unlike EPL policies, D&O policies do not routinely exclude such coverage, but are including such exclusions with increasing frequency. As a result, policyholders must review D&O policies carefully to ensure that they protect against the threats posed by such claims.
Brokers and insurers have been developing new insurance products that specifically address these increasing wage-and-hour exposures. Policyholders, particularly those with significant operations in California and New York, should consider these newly emerging wage-and-hour specialty policies to ensure that they are adequately protected.
Food Contamination and Recall Coverage
The number of food product recalls for alleged contamination, undisclosed ingredients and other mislabeling issues also has risen dramatically. Although CGL and business property insurance policies provide some protection against liability for food contamination and recalls, savvy food companies should also consider specialized recall and contamination coverage.
These specialized policies may cover the reasonable costs that a policyholder incurs, for example, to examine its products for contamination, announce and institute a product recall, safely destroy contaminated products, and reimburse distributors and retailers for down-stream recall costs. Such policies often include crisis management coverage to help the policyholder mitigate negative media reports.
Varying types of special coverage. Because recall and contamination policies are not standardized, individual insurers offer differing policy terms and levels of coverage. Companies contemplating the addition of such coverage, or pursuing coverage under an existing policy, should closely examine the policy to understand the scope and limitations of coverage.
Items to watch. When purchasing such coverage, food companies need to identify their primary risks and negotiate the broadest possible coverage. In addition, because such policies often include very strict notice requirements, policyholders should give notice as soon as a recall arises to avoid coverage denial on late notice grounds.
Christina Buschmann, Linda Powell and Adrian Torres, Perkins Coie Insurance Recovery attorneys, also contributed to this article.

 e courts have held that fraud coverage applies only when intrusions are unauthorized, but not when an unwitting employee falls prey to an online scam.
e courts have held that fraud coverage applies only when intrusions are unauthorized, but not when an unwitting employee falls prey to an online scam.