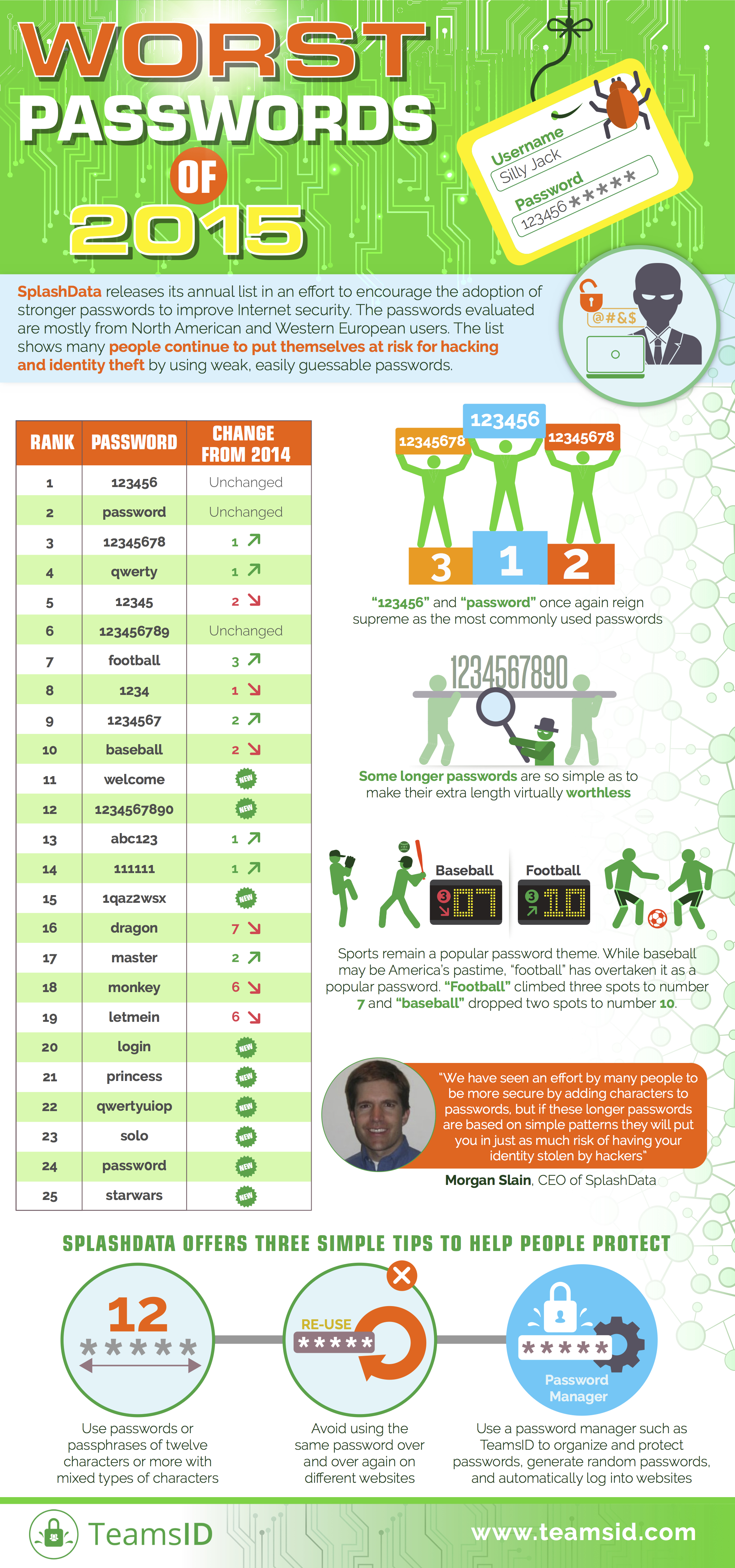
Many are having trouble maintaining the security of their employees’ log-in information, resulting in serious risks to their networks and private information. According to a recent LastPass and VansonBourne survey of 750 IT and security professionals in the United States, United Kingdom, France, Germany, Australia and Singapore, only 18% feel their company’s current access security is “fully secure and does not require improvement.” Risk management professionals have a significant role to play in determining how their organizations handle these risks and protect their data.
Some of the biggest ways that employees’ poor password management creates potential security threats to organizations’ data, according to the security professionals surveyed, are password reuse (according to 67%), weak passwords (65%), and not changing default passwords (36%), according to the security professionals surveyed. Nearly all respondents (95%) said that the risks that come along with using passwords create threats to the organization.
Given the importance of strong login information, companies often attempt to implement password rules to reduce security risks, such as requiring employees to choose complex passwords and change them frequently. However, these issues can lead to frustrations for both IT staff and employees. According to the LastPass/VansonBourne survey, the top frustrations for IT are employees reusing passwords for multiple applications, forgetting their passwords, and the time it takes to manage the company’s passwords. Employees are frustrated by having to regularly change their passwords, remember multiple passwords, and type long and complicated passwords.
The rapid increase in the number of employees working from home due to the COVID-19 pandemic has also exacerbated the risks, given a corresponding surge in cyberattacks on remote workers since March. Many employees are now working on home networks that may not have the protections that office networks offer, their passwords may not follow the stringent guidelines their companies would normally require, and they may store their passwords in less secure ways. In fact, Entrust Datacard released a survey showing that 42% of employees working from home kept passwords by physically writing them down, while 34% saved them in their phones and 27% kept them on their computers. The survey also found that almost 20% of employees reused passwords across multiple systems, which could make it easier for malicious actors to compromise those systems.
Maintaining Secure Logins
There are ways for risk professionals to help protect their companies’ systems and data. Experts recommend mandatory cybersecurity training for all employees, including instructions on how to choose adequate passwords, how often to change them and how to avoid cyber threats like phishing and malware.
There are also technological ways that risk managers can help secure their organizations’ passwords. As a first step, the National Institute for Standards and Technology (NIST) recommends that organizations ensure that employees’ passwords do not match those exposed in previous data breaches.
There are publicly available services online that allow users to check whether email addresses and passwords have been compromised in breaches.
Additionally, the NIST recommends that employers restrict passwords to those that are not dictionary words, are not made up of repeated or sequential characters (such as 11111 or 12345 or qwerty), and do not contain specifics like the company’s name or the user’s name. NIST also suggests using multi-factor authentication (MFA), which would require employees to provide their login and password as well as a second piece of information, biometric data, or a physical device like a security key to verify their identity and log in.
With so many passwords to remember, a password manager—a program that stores and creates multiple complex passwords—may also be a good choice for organizations to protect their systems.
Like all security precautions, password managers are not perfect. While still recommending their use, the Electronic Frontier Foundation warns that “using a password manager creates a single point of failure,” “password managers are an obvious target for adversaries” and “research suggests that many password managers have vulnerabilities.
”
While a password manager or single sign-on technology can have benefits like faster authentication and letting employees remember fewer passwords, they also have downsides. The IT professionals surveyed by LastPass cited “the initial financial investment required to migrate to such solution,” “the regulations around the storage of the data required,” and “the initial time required to migrate to new types of methods” as the biggest challenges about using this technology. Additionally, 74% surveyed said that they thought employees at their companies would likely prefer to continue using passwords over passwordless methods because it was more familiar.