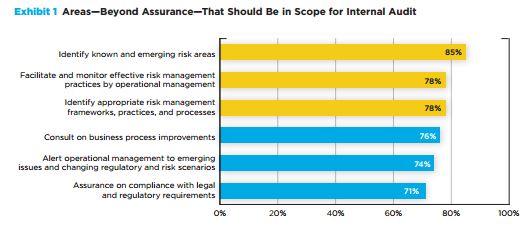
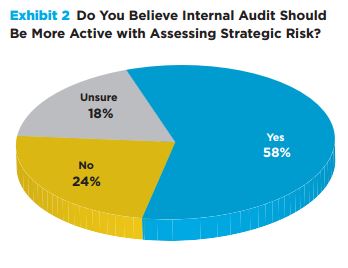
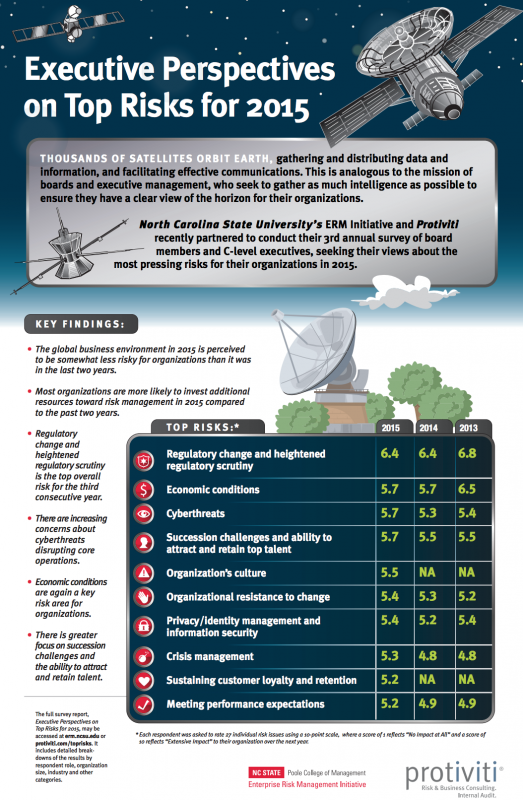
Preparing for and responding to negative events, from the mundane to the catastrophic, from the predictable to  the unforeseen, has become a fact of life for businesses and governments around the world. We don’t have to look any further than the seemingly daily reports of cyberattacks on governments, corporations and individuals to comprehend the severity of the problem.
the unforeseen, has become a fact of life for businesses and governments around the world. We don’t have to look any further than the seemingly daily reports of cyberattacks on governments, corporations and individuals to comprehend the severity of the problem.
Tackling these risks requires an integrated and holistic framework with the capability to identify, evaluate and adequately define responses to the circumstances. For more and more organizations, this means adapting an enterprise risk management (ERM) model. ERM seeks to identify all threats—including financial, strategic, personnel, market, technology, legal, compliance, geopolitical and environmental—that would adversely affect an organization. This holistic approach gives organizations a better framework for mitigating risk while advancing their goals and opportunities in the face of business threats. But in order to implement and continuously manage this enterprise-wide model there is a critical need for closer integration of two typically distinct roles within the organization—business continuity management (BCM) and risk management. Together, these two vital elements make up a robust ERM plan and have a tremendous impact on an organization’s ability to contend with interruptions to the execution of organizational activities.
Put in the simplest terms, risk management is concerned with minimizing the probability of and destruction caused by negative events. Operational risk management, as the name implies, must cope with interruptions at the operational level. Recognizing that there are inherent imperfections in systems, people, facilities and general operational functions, the essence of operational risk management is to negate or reduce the probability of an incident occurring. Focusing upon incident-specific, site-specific analysis of potential causes of interruptions, risk managers seek to preclude incidents from occurring. If elimination of the risk is not possible, the focus moves to minimizing the results of the negative event.
For example, suppression systems reduce the risk of operational disruption caused by fire damage. Redundant equipment decreases the possibility of operational interruption resulting from machine breakdown and redundant communications help maintain connectivity. By analyzing past events and examining known hazards (defined flood plains, hurricane-prone areas, construction sites, earthquake areas and terrorism-prone areas) operational risk management seeks to avoid the occurrence of negative destructive events.
 But creating strategies to minimize the probability that an event will impact an organization certainly will not prevent the incident from taking place. No degree of preparation can stop a tornado, tsunami or other massively destructive event.
But creating strategies to minimize the probability that an event will impact an organization certainly will not prevent the incident from taking place. No degree of preparation can stop a tornado, tsunami or other massively destructive event.
So understanding that every incident is not preventable, our other line of defense is to minimize the impact. That’s where BCM comes in. BCM is concerned with minimizing the impact upon the entity after an event occurs and restoring the organization to its normal operations and delivery of products and services as quickly and safely as possible. In short, BCM helps maintain the viability of an entity under duress.
Because it is event-neutral, BCM is able to categorize effects into four distinct categories:
- Effects on facilities, making them inaccessible or unusable
- Effects on operational capability, such as supply chain interruptions, processing errors or staff unavailability
- Effects on technology
- Effects on the organization itself, ranging from financial problems to intellectual property rights.
When an event inevitably does occur, the optimal goal is to make any business interruptions imperceptible to those outside the affected organization. Here’s an example of how risk management and business continuity management, working together, enabled an organization to achieve that goal:
One of the world’s most important foreign exchange dealers realized that, as an occupant of a high rise building, it could not control the consequences of all incidents that might impact its ability to service its customers, which were some of the largest financial institutions in the world. A review by the company’s risk manager determined that there was a likelihood of an interruption in service as a result of construction work in the surrounding area. To reduce the risk, it was recommended that they install redundant lines and route them through alternative conduits into the building. So they undertook building redundancy in their telecom network. In addition, the risk of server failure was similarly high and so mirroring was implemented to duplicate all transactions and ensure that no data would be lost in the event of a failure of the building’s infrastructure.
Despite all the precautions to reduce risk, what risk management couldn’t control was an East Coast blackout that terminated power to its operation.
Recognizing the impact that a loss of power could have, including the loss of use of the facility, the business continuity professional determined that a robust contingency plan was required.
The business continuity plan included a strategy that automatically forwarded incoming calls to another facility outside the U.S. and also provided connectivity to its back-up technology center. When the blackout hit, the business continuity plan worked exactly as tested. Phones were switched, systems were accessible and, best of all, customers never knew the difference. The company was actually more prepared than many of its customers who failed to provide similar capabilities and had to cease trading.
The combination of risk management and business continuity provides the level of resiliency that most organizations must achieve in light of the uncertainty that exists today. The blend will reduce uncertainty and promote a more stable operating environment.