For many organizations, risk management spans four distinct categories – physical, financial, human and intellectual. When thought about in context, it’s easy to see how one risk area might impact another. An earthquake that takes down an office building, for example, has clear financial implications in the form of productivity downtime and the cost of building repairs. Given these seemingly easy correlations, it is baffling that so many businesses remain siloed when it comes to managing each area, especially given how it puts them at a higher risk as a result.
Unsurprisingly, these siloes create a lack of communication throughout an organization. Physical security, for example, can often be dealt with by facilities management teams, whereas financial risk is handled by the finance team.
Technology hackers are no strangers to this common, organization-wide breakdown – they prey on communication lapses when strategizing an attack.
The solution is simple: break down these siloes to minimize risk gaps. But, as with most pieces of advice, the steps required to achieve this are much easier said than done, especially when it comes to silo-busting in business. The trick is for an organization to use its employees to its advantage. With collaboration between departments and strengthening universal security training across every department, IT teams can make it much harder for hackers to execute coordinated attacks across the business.
Avoid Letting a Hyperlink Be Your Downfall
Email is the primary communication tool in business, and is also the platform that reinforces employees’ position as being both the biggest threat and biggest asset to risk management. Email also happens to be a commonly chosen route for hackers to take when infiltrating an organization.
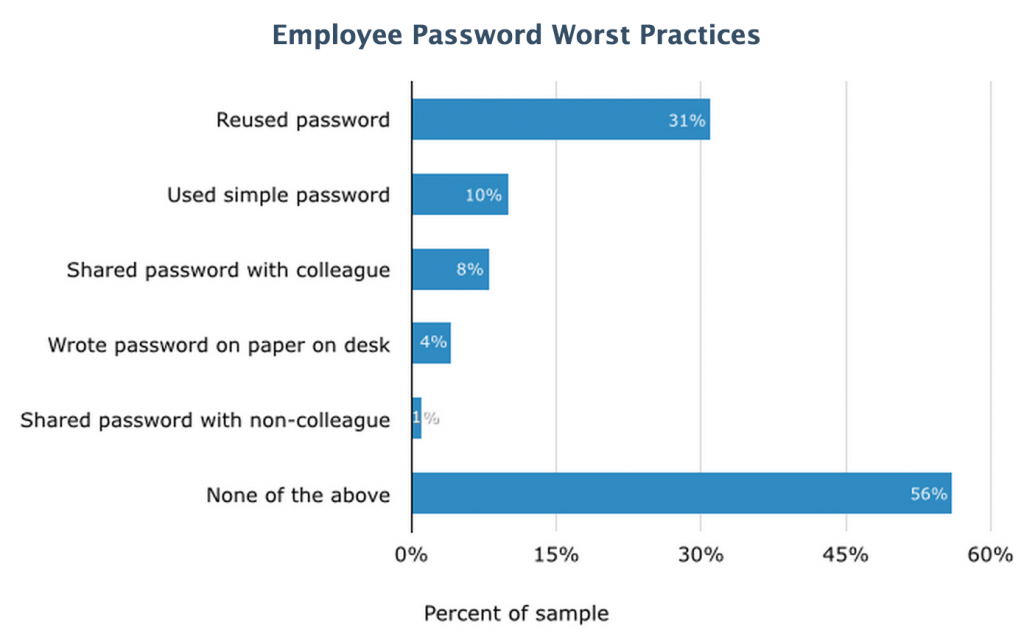
Phishing attacks via email, for example, are underpinned by social engineering and can be targeted to specific employees and job functions. According to the August 2014 HP TippingPoint survey, State of Network Security, they are dealt with by nearly 70 percent of IT professionals at least once a week, and involve a hacker disguising a malicious link as one from a “trusted” sender. When clicked by the employee, the link can give hackers the ability to pivot within their target’s network and gain unprecedented access to an organization’s network and beyond. Once attackers breach a system like email, or trick the humans reading those emails into clicking a link, it’s easy for them to exploit the organization’s financial, intellectual and physical assets further.
For example, infrastructure attacks on building control systems, although not new, can now be perpetrated remotely over the Internet.
Malware attacks such as Flame, Duqu and Regin highlight how threat attacks are specifically targeted to control systems more and more often. As such, employing a security guard to take watch over an organization’s physical control system is no longer enough to keep outside attacks at bay.
Current IT Security Training is Failing
So, what’s an organization to do? Current training and prevention methods are lackluster, and many organizations still embody the “set it and forget it” method. It’s often assumed that once employees have been trained on IT security once, that’s all it takes. Or worse, IT security training is coupled with other training, thereby diminishing its value. For example, training on an organization’s fire evacuation procedure might be thrown in with IT security training during an employee’s induction sessions.
Organizations that do this are setting themselves up for failure. The IT department has implemented training in a way that works best for them, such as a webinar, PowerPoint or squeezed in with another training for time-saving purposes. This takes the place of training that is tailored to make the most sense for the employees.
How to Revitalize IT Security Training
The key to getting past common training slumps is by not only finding unique ways to train employees to help prevent breaches, but also by having them understand the impact a breach can have on other areas of the business, and even their own job.
Organizations must think outside the box and adopt the mindsets of both the employees and hackers to start making a behavioral change in their users. This includes tactics such as making training apply to specific job titles and departments, suggesting a job swap for a day so one department can learn another’s issues, or leveraging creative ways to remind employees not to click on suspicious links. This could include Christmas cards, SMSs or private social media groups and forums.
buy lipitor online https://royalcitydrugs.com/lipitor.html no prescription
But, IT security can be taken even a step further, being made an organization-wide campaign. How about taking after Facebook and making a game of it? As reported by a director on the Facebook security team in November 2012, Facebook decided to put an end to dull employee cyber-security training with the launch of Hacktober in 2012. October is National Cyber Security Awareness Month, and throughout the month, Facebook’s cyber security team created a series of simulated security incidents that are targeted at specific internal departments, based upon the types of threats they are most likely to see. Employees that spot a Hacktober attack are rewarded with a prize, thus achieving the goal of being both educational and interesting.
Beginning with IT security to eradicate risk throughout the organization is only possible by approaching it from a human-interest angle. Humans are both the perpetrators and victims, and it’s time IT starts designing training that reflects that. Above all else, mitigating risk requires organization-wide support, including from the C-suite. Organizations can make quite an impact on prevention—not by spending a large budget on training, but by taking it back to their employees and helping them understand the ripple effect just one malicious email or link can have.