As technology becomes more critical to company success, the number of cyberattacks has climbed.
As a result, cyberrisk has become one of the top risks for companies around the world, according to the Marsh-Microsoft Global Cyber Risk Perception Survey. Almost two-thirds of survey respondents identified cyberrisk as one of their organization’s top-five risk management priorities—almost double the percentage who rated cyber as a top risk in a 2016 study, Marsh said, adding that respondents whose organizations had been successfully attacked were slightly more likely to prioritize cyberrisk than those who had not.
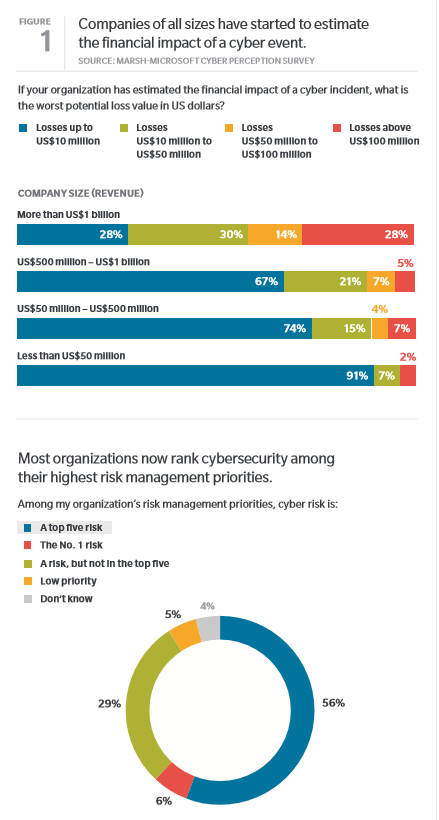
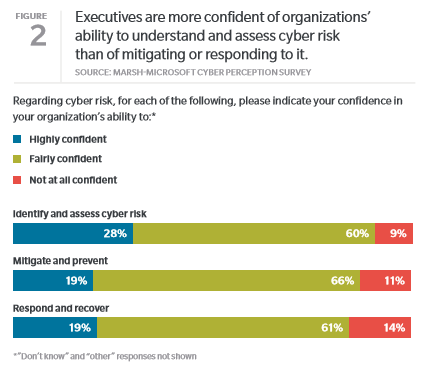
Despite these concerns, however, the study notes that just one in five respondents said they are “highly confident in their organization’s ability to manage and mitigate cyberrisk or respond and recover from an attack.” This was especially the case among corporate directors, who play an important role in protecting their organization from cyber threats. While about 70% of respondents who identified as board members said they ranked cyberrisk as a top-five concern, only 14% said they were “highly confident” in their organization’s ability to respond to an attack.
Board Disconnect
While organizations have traditionally relied on IT staff to manage cyberrisks, the structure of oversight is evolving in many companies as risks accelerate. Stakeholders from across the enterprise are looking beyond prevention to include risk assessment, mitigation and cyber resilience.
Asked about cybersecurity structure, however, 70% of respondents named their IT department as a primary owner and decision-maker of the risk.
This was more often true for smaller companies, as larger organizations tended to spread the responsibility for cyberrisk—from a low of 13% in the smallest organizations (many of which may not have a separate risk management function) to 58% in the largest organizations with more than $5 billion in revenue, the study found.
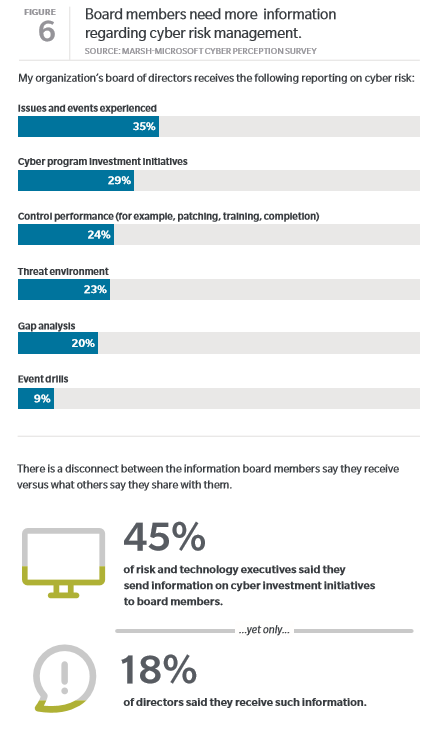
Ideally, boards should view cyberrisk management as part of their overall perspective on enterprise risk management. In organizations where the board is involved, however, the study found a disconnect:
Corporate directors often appear to either not understand the information on cyberrisk they receive, or to not be receiving it all. For example, 53% of chief information security officers, 47% of chief risk officers, and 38% of chief technology/information officers said they provide reports to board members on cyber investment initiatives. Yet only 18% of board members said they receive such information.
This information gap illustrates a need to develop cyberrisk economic/business models that facilitate shared dialogue including common language among IT, the board, and other corporate departments.
This disconnect also reinforces the need for a cross-functional approach to cyber risk governance, according to the study.