As employees can be key perpetrators of fraud, creating and implementing best practices with regard to insiders is a key part of an enterprise’s everyday risk management procedures. For example, developing internal controls that involve multiple layers of review for financial transactions, and arranging independent reviews of the company’s financial records can prevent malfeasance, detect ongoing fraud and prevent it from continuing.
In fact, according to Kroll’s 2019 Global Fraud and Risk Report, businesses discovered insider fraud by conducting internal audits 38% of the time, through external audits 20% of the time and from whistleblowers 11% of the time.
Technology solutions provider Column Case Investigative recently examined five common types of fraud that businesses face, including employees falsifying their timesheets to steal money from the company, taking intellectual property or passing off counterfeit items as genuine, funneling money away from vendors to themselves, or soliciting favors or compensation from clients or vendors for preferential treatment. These tactics can impact a company’s profits and expose it to possible litigation, but also pose risk to its reputation with customers and partners, as well as its competitiveness.
To best mitigate these risks, the provider recommended that companies do their due diligence in the hiring process to detect any warning signs that applicants may have a motive to commit fraud. To limit intellectual property theft and misuse, they should limit access to important information and materials.
Enterprises can also create clear ethical standards for employee conduct and a positive culture in which workers are happier, more committed to the company and more comfortable reporting fraud when they see or suspect it happening.
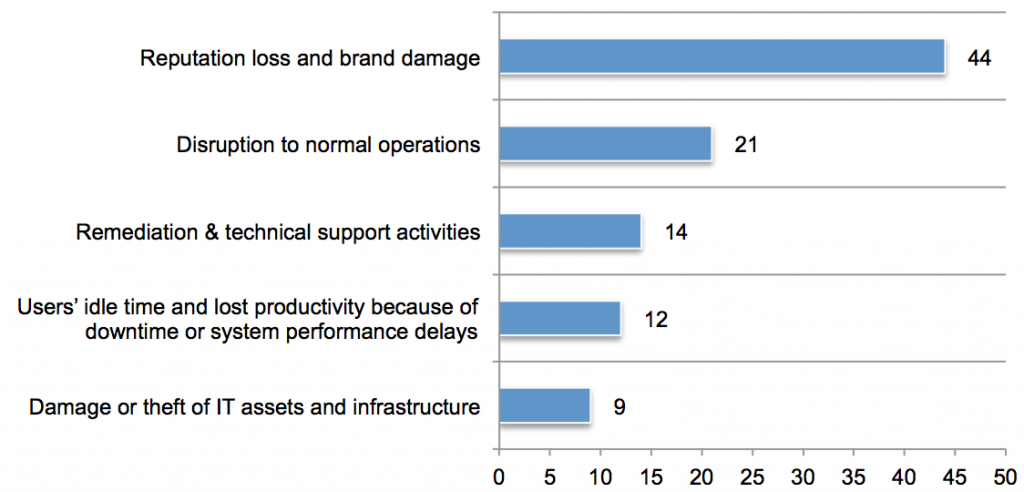
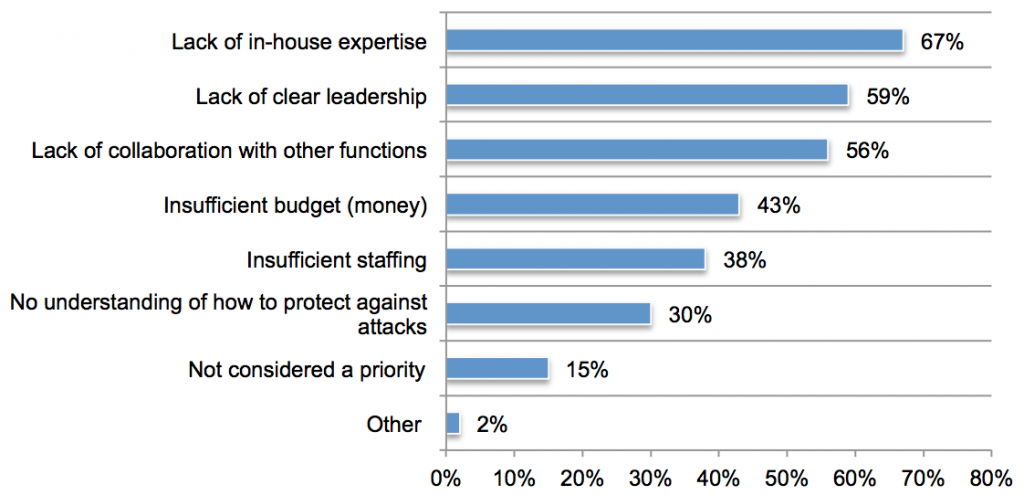
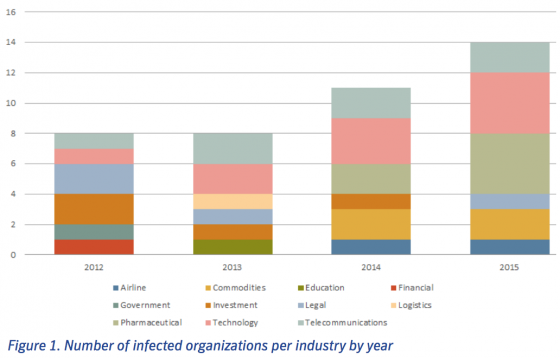
Check out the infographic below for more best practices to mitigate employee fraud risks:


![Copy(right) Cats: How Intellectual Property Theft Affects Everyone, Including You [INFOGRAPHIC]](http://cdn.i-sight.com/uploads/intellectual-property-theft-infographic.jpg)