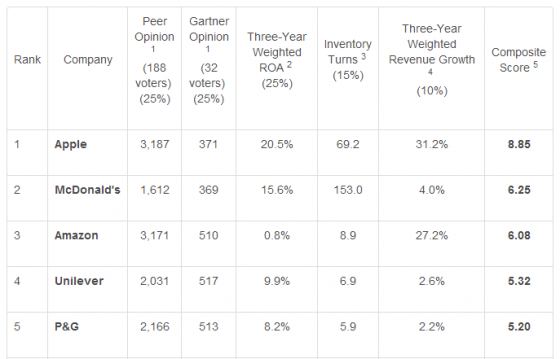
Gartner announced its top 25-ranked organizations for supply chain in 2014, which includes four in the top-5 that also topped last year’s list. They are: Apple, McDonald’s, Amazon and Unilever, with P&G at fifth place. Gartner analysts announced the findings from this year’s research at its Supply Chain Executive Conference last week.
Apple took the No. 1 spot for the seventh year, continuing to outpace the others by a wide margin on the composite of financial and opinion measures used. McDonald’s placed in second spot for the second year in a row, followed by Amazon.com.
Two new companies joined the Top 25 this year—Seagate Technology (No. 20) appeared for the first time and Kimberly-Clark (No. 21) re-emerged after a year’s hiatus.
A primary goal of the Supply Chain Top 25 research initiative is to raise awareness of the supply chain discipline and how it impacts business, Gartner said. The supply chain rankings comprise two main components: financial and opinion. Public financial data gives a view into how companies have performed in the past, while the opinion component provides an eye to potential and reflects future expected leadership. These two components are combined into a total composite score.
Gartner analysts develop a master list of companies from the Fortune Global 500 and the Forbes Global 2000, with a revenue cutoff of $10 billion. The company then breaks the combined list down to the manufacturing, retail and distribution sectors, eliminating certain industries, such as financial services and insurance.
Analysts highlighted three standout trends for supply chain leaders in 2014:
Supporting the “Fully Contextualized” Customer
A trait of leading companies is that customer needs and behaviors serve as the starting point for go-to-market and operational support strategies. Their cultures enable consistently high-quality customer experiences that are tailored, where important, to local tastes. Supply chain leaders are expanding this demand-driven concept in terms of how they relate to their customers. They are more deeply understanding customers and striving to blend seamlessly into their daily routines. Ultimately, this understanding of customers in their local environments is helping supply chain leaders capture more revenue for their businesses, improving operational effectiveness, Gartner said.
Converging Digital and Physical Supply Chains
Leading companies have moved past selling only discrete products or services to their customers and are focused on delivering solutions. Regardless of industry, these companies want their customers to be loyal subscribers to their solutions. Several of the leading consumer product companies on this year’s list offer e-commerce subscriptions for their products, in partnership with retailers. This approach offers convenience and privacy to those customers who would typically purchase products in a physical store—and might switch to another consumer brand at any time.
Progressive industrial companies have suggested order replenishment systems with their dealer networks, based on the manufacturer’s ability to forecast demand for their dealer. Some have gone further, acting as virtual consultants to their customers’ planning organizations. They recognize that helping improve customers’ internal capabilities is part of a total solution, which makes them more competitive suppliers.
“Another significant aspect of the total customer solutions we see deployed by leaders relates to the remote management of aftermarket services, leveraging Internet connectivity,” said Debra Hofman, research vice president at Gartner. “The Internet of Things allows for monitoring of performance across the value chain; in the field at customer sites, but also to collect and analyze the big data generated as part of upstream manufacturing and logistics flows. This additional connectivity has also elevated the importance of supply chain security to prevent theft, counterfeiting and other forms of fraud. One thing is clear — future supply chains must seamlessly integrate the digital and physical worlds of customers to be competitive.”
Supply Chain as Integrated Partner
Growth is a top priority for the C-suite in 2014, with 63% of senior executives picking growth as a top imperative in Gartner’s 2014 CEO Survey. Leading supply chains are enabling this growth both organically and through successful M&A integration. Supply chain leaders also are emerging as trusted and integrated partners to business groups. Their focus on profitable growth often leads to smarter, more conscious decision making, saving business groups from spiraling out of control in the drive to maximize revenue.
In their quest for growth, however, many companies are finding the business models they were famous for dominating are now under attack from competition. Supply chain has a large part to play in enabling the business to compete for the future, concurrent with protecting existing business. The most advanced companies in the ranking said they are not afraid to rethink the design of their global supply networks to be successful. In some cases, this has led to increased vertical integration where leaders become involved in their customers and their suppliers’ businesses in an attempt to dominate value chains, redrawing the lines of competition in the process.
More detailed analysis is available in the report “The Gartner Supply Chain Top 25 for 2014.”