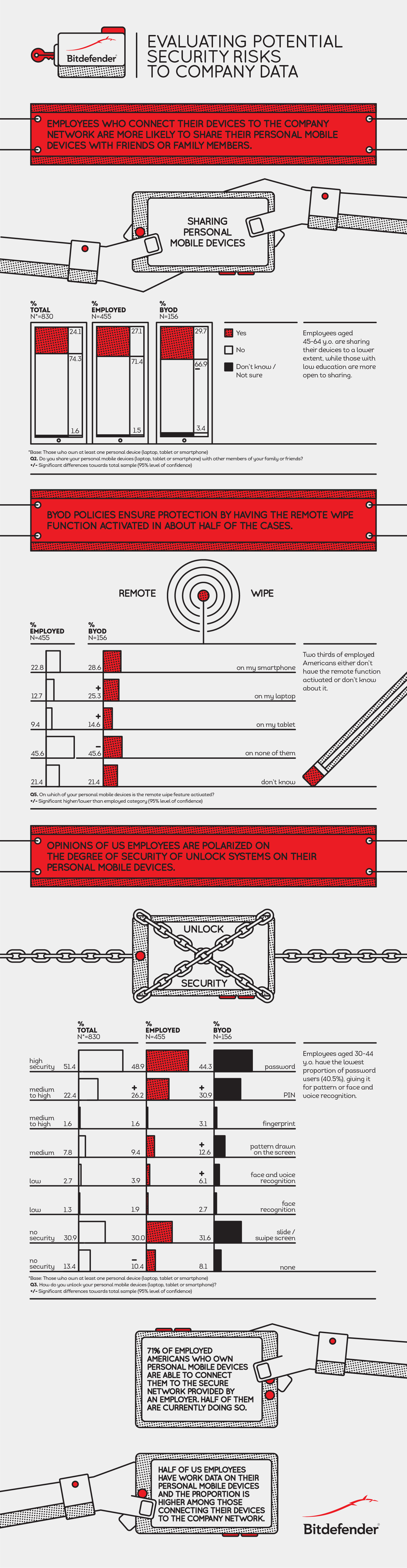
By 2017, half of employers will require employees to provide their own mobile devices for work use, Gartner reports. There are many benefits to BYOD policies, from greater productivity on devices users are more comfortable with to lower corporate costs when businesses do not have to purchase mobile equipment or service plans. But securing these devices poses tremendous risk that may not be worth the reward.
According to data security firm Bitdefender, 33% of U.S. employees who use their own devices for work do not meet minimum security standards for protecting company data. In fact, 40% do not even activate the most basic layer of protection: activating lock-screen features. Further, while the majority of workers could access their employer’s secure network connection, only half do so.
Bitdefender reports that there are 5 core security functionalities a strong BYOD policy should check:
- Data encryption, for data residing on the employee’s device and for data transiting different channels.
- Application access control, using port knocking, whitelists and intrusion prevention systems, for enterprise apps communicating with company servers.
- Mobile malware detection and removal, to ensure clean devices enter the company and to keep them malware-free throughout their use.
buy rifadin online www.scottsdaleweightloss.com/wp-content/uploads/2023/10/jpg/rifadin.html no prescription pharmacy
- Real-time app and website scanning, to make sure the device does not get infected by malicious apps or websites when the employee wants to download/access them.
buy augmentin online www.scottsdaleweightloss.com/wp-content/uploads/2023/10/jpg/augmentin.html no prescription pharmacy
- App permission management, to allow employees to see exactly what types of information does an application require permission to access and share with the application vendor.
Check out more of the study’s findings below: