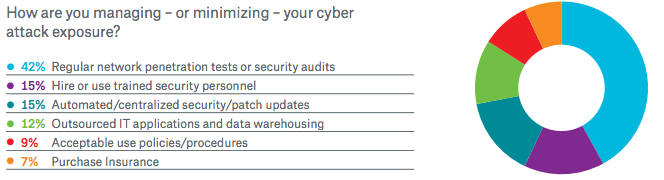
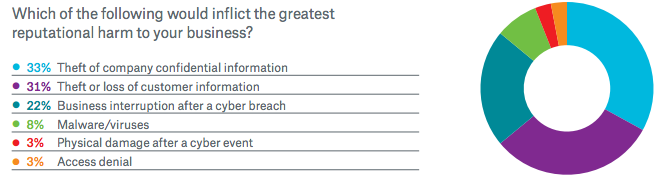
More Americans worry about being hacked than they are of mugging, burglary, sexual assault, murder, or physical harm of a child, according to a new Gallup poll. While hacking concerns did increase with household income, they impacted a majority of Americans in every income and age bracket, while no other form of violent crime surpassed 45% of those polled.
A new survey from Advisen and Zurich found that this fear is nearly universal for companies as well. Across industries, 88% of businesses view cyber as at least a moderate risk – up to 93% among larger businesses and 81% among small. Despite this widespread recognition, however, fewer businesses have a breach response in place than just a year ago. In 2014, only 62% have a response place – a 10% decrease from 2013. Yet 66% now use cloud services, presenting a 20% jump from last year.
“Clearly, security concerns are being outweighed by the benefits of technology,” said Erica Davis, Zurich vice president and assistant national manager for E&O, while presenting the findings on Tuesday at Advisen’s Cyber Risk Insights Conference.
Throughout the conference, consensus was clear: the 69% of Americans and 88% of businesses are on the right track, as their fears are well-founded. “There are two types of banks today: those that have been breached, and those that will,” Roc Starks, senior vice president and director of corporate insurance at Citizens Bank, said at one of the day’s panels. “First response is the critical difference in how banks and customers will fare.”
Keynote speaker and former Director of Homeland Security Tom Ridge (now of Ridge Insurance Solutions) shared this outlook on cybersecurity across industries. “There are going to be breaches,” he said. “Resilient companies are the ones that are prepared to respond.”
Yet breach response without risk management and an eye toward mitigation is no longer sufficient. “Those prepared to organize around risk and resilience are those that will withstand and lead,” he added. “By the time we get here next year, the risks will be different – the digital sun will never set.”
The landscape of cyberrisk and hacking schemes is constantly evolving, and changing at a scale and speed unlike anything seen before, Ridge said. For attendees, there was little doubt about this insight, as panelists throughout the day detailed new phishing schemes seen, top areas of emerging vulnerability, and the myriad breaches they or their industry colleagues have navigated. More companies are investigating the most useful forms of coverage for their unique exposures and exploring what management structures and risk owners are most effective to monitor and mitigate cyber. The recognition is there, and so are some of the solutions, but the insurance landscape must still evolve, as must the strategies. “We’ve seen a mind-shift,” Ridge said. “CEOs get it, but they do not know what to do and who the threats come from.”
To that end, there is more the industry can do to help. Ridge lauded the idea of “intelligent insurance,” arguing that, in addition to devoting greater resources to investigating cyber threats, the insurance industry should turn its attention to incentivizing companies to manage cyberrisk more effectively.
Much as in insurance disciplines like kidnap and ransom, some of the greatest benefits of insuring cyberrisk may come from the processes of evaluation and contingency planning. According to Ridge and other conference speakers, finding out how to oversee and incentivize those processes may be the next adaptation for cybersecurity insurers.