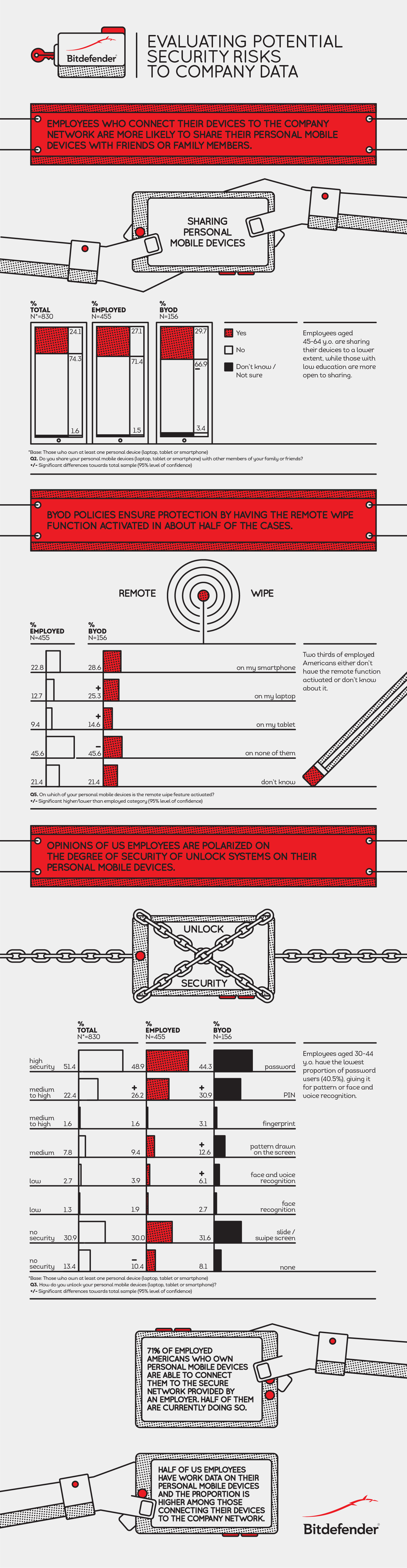
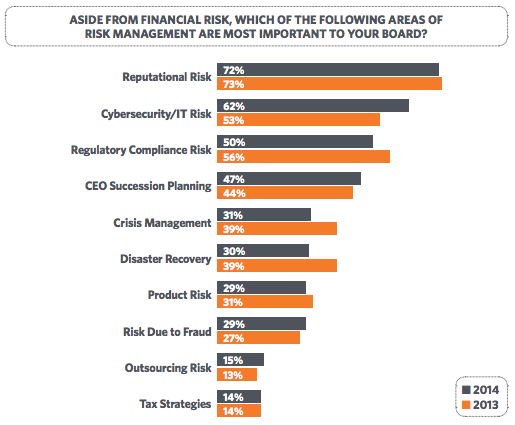
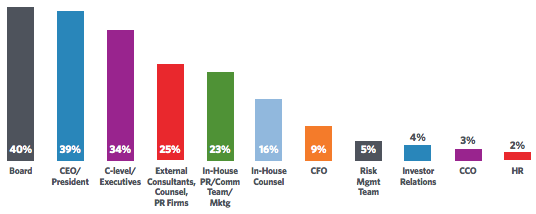
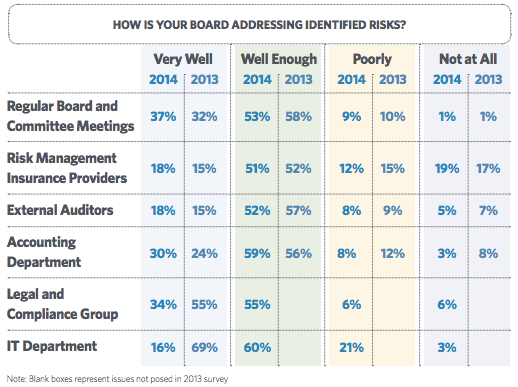
Many of the attacks launched against today’s brands are as covert as they are debilitating. In today’s connected age, savvy cyber criminals often blitz companies with a flurry of activity across an array of online channels.
To make matters worse, employees who are using the Internet casually or personally create a vulnerability for businesses: workers could click on a phishing link sent to their personal account and unknowingly be exploited by cyber criminals, or they could bring harm to the business via a social media post they thought to be harmless.
And, let’s not forget that brands can also inflict damage on themselves, such as through executive scandals, accounting errors or failing to protect customers and investors.
Even though these events may not involve a malevolent, third-party attacker, the resulting fallout can be just as severe as if they fell prey to one.
Given these circumstances, companies could face a barrage of both external and internal threats to their brand, customer loyalty and bottom line.
So, how can they defend themselves? The same crisis management procedures brands use following an external attack should also extend to self-inflicted events. Every reliable, robust brand defense strategy should begin with an Internet Reputation Management Council (IRMC).
The Power of Many
No one stakeholder within a company can be solely responsible for online brand reputation management. Instead, businesses need to bridge the gap between departments, creating an environment in which employees across the marketing, security/IT, finance and legal departments unite and share resources to defend the brand—and it all begins with an IRMC.
Council members representing departments throughout the organization will become Internet reputation champions who work collaboratively, from within their individual departments, to ensure that ownership and management of the brand is carried out across the enterprise.
As such, an IRMC has the range and visibility to combat the multitude of Internet-based threats. To borrow a term from the military, an enterprise that deploys an IRMC is essentially following a “defense-in-depth” strategy, by creating a redundant, layered web of defenders.
The Members of an IRMC
Once a company decides to launch a cross-departmental IRMC, who makes up its members? Executive-level sponsorship will provide the vision for an Internet reputation strategy, facilitate cross-functional and resource collaboration, and build a brand-aware organizational culture. A team leader is responsible for executing that vision on a day-to-day basis and marshaling the resources needed to protect the brand. Area leaders will protect the brand from various departments within a business, including marketing, legal, investor relations, compliance, e-business, human resources, public relations, security and fraud, and IT.
Although all IRMC roles are important, it’s these area leaders who can make or break a brand’s Internet reputation.
A successful response demands the full participation of every member of an IRMC. Even though response actions may be centered in one department, these crises are full-company situations.
After all, it’s not as though the public would only render judgment in isolation, for example, against “Target’s security team” or “Yahoo’s executive search committee”—the entire brand is put under a microscope following an incident.
A Defender at Every Position
With an effective IRMC, companies like these can use the “power of many” to combat such Internet-based threats to their brand, even when they’re self-inflicted. An IRMC operates by:
- Identifying key internal stakeholders and inviting them to collaboratively establish the guidelines of Internet reputation management within the company
- Meeting regularly to keep abreast of industry and technology changes, as well as emerging forms of Internet-based threats
- Establishing goals and targets, such as building a structure to set up a “Best of Breed Governance Policy,” and setting metrics to track performance
- Preparing emergency response protocols
- Implementing training policies and communication within each department
- Reviewing, measuring, evaluating and managing progress against objectives
Although a fairly new concept, there are already real-world examples of effective IRMCs. AstraZeneca’s reputation council, for example, comprises a diverse group of those with “stakeholder responsibilities,” including representatives from sales, marketing, finance, human resources and communications. It reports directly to the CEO, and because of this structure, long-term risk management and prevention are infused into the company’s corporate focus.
Ultimately, the true value of an IRMC like AstraZeneca’s isn’t in how many attacks it directly neutralizes, but that it creates an organizational culture of Internet reputation management excellence, starting with the heads of core departments and working its way throughout the rest of the enterprise.
By the time the IRMC is engaged responding to an incident, significant damage has already occurred. The best-protected brands are those that have identified brand protection as a central part of their mission statements. Their investment in a culture of excellence, led by their IMRC, mitigates risks before they become reality, improves profits and creates value for customers, employees and other stakeholders.