The COVID-19 pandemic and subsequent shutdowns have meant perilous times for small businesses across the country, with many shutting down temporarily or even permanently. As part of the U.S. government’s efforts to forestall bankruptcies and layoffs, Congress allocated hundreds of billions of dollars for the Paycheck Protection Program (PPP). Small businesses can apply for loans from the U.S. Small Business Association (SBA), which the SBA will forgive if the receiving business meets certain criteria, like “if all of the company’s employees are kept on the payroll for eight weeks and the money from the loan is used to pay for rent, mortgage interest, utilities or payroll.”
The program has helped many businesses, but also left many stranded and desperate when they could not qualify for the loans. According to the Wall Street Journal, as of this week, the government has disbursed “4.6 million loans worth more than $513 billion.” But some businesses were forced to return the funds when they discovered they could not open soon enough to meet the eight-week deadline, and some did not even bother applying because they did not meet the criteria. The program has also faced criticism for not providing enough funds, and when larger and/or publicly traded companies (like restaurant chain Ruth’s Chris) received loans.
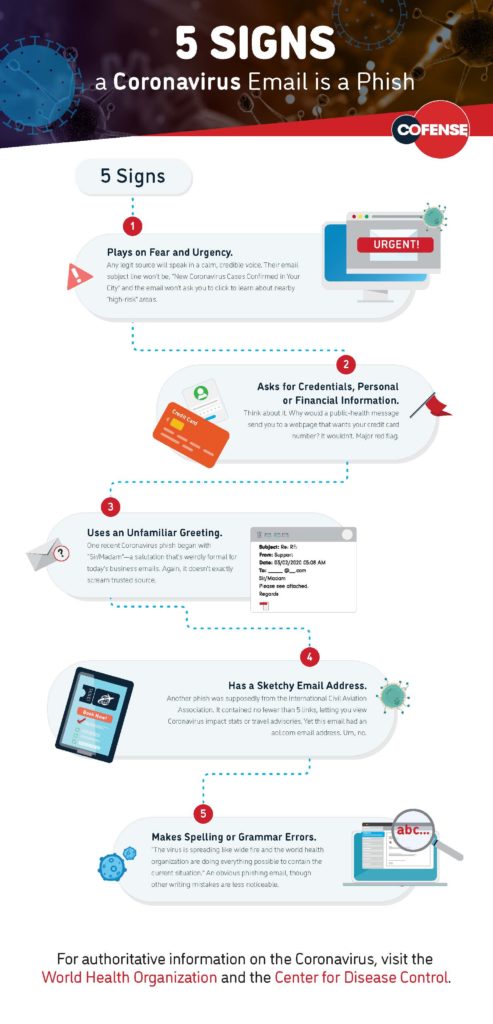
As with many other government programs that award payouts and may have confusing or labyrinthine application and approval processes (such as Social Security payments or tax refunds), scammers have targeted desperate businesses trying to access PPP funds. Online identity verification service Social Catfish recently published guidelines for avoiding PPP-related scams that small businesses are facing, including phishing and robocall scams.
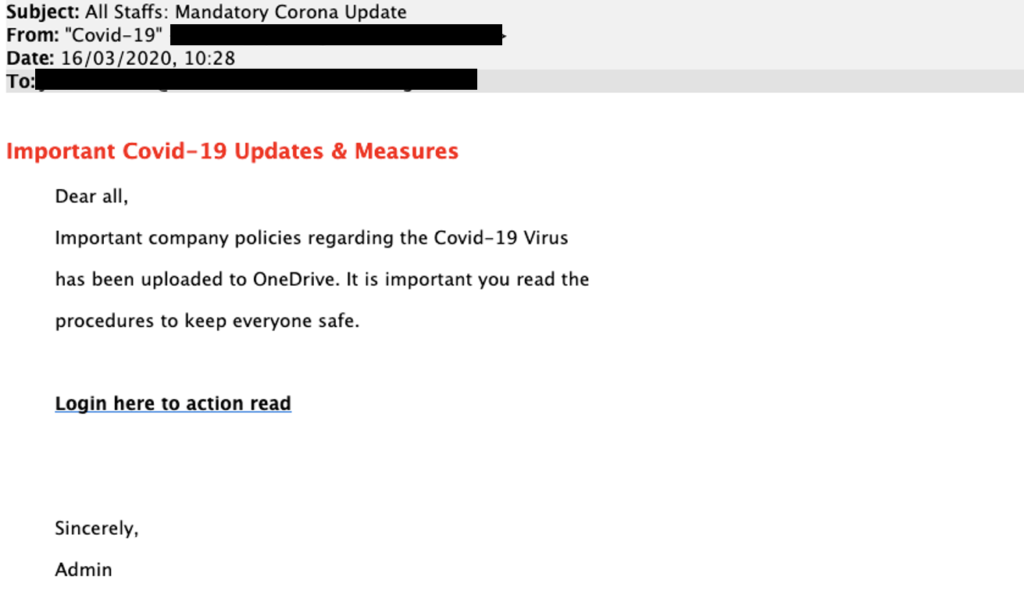
As Risk Management recently reported, phishing scams—in which criminals use fraudulent emails to trick users into clicking malicious links or divulging sensitive personal information—have proliferated since the start of the COVID-19 pandemic, often specifically targeting pandemic-related concerns. According to Social Catfish, online scammers have been using emails posing as the SBA inviting the recipient to apply for a PPP loan, then installing malware or stealing any information provided. With this information, scammers can then pose as a business to apply for loans or steal funds.
Scammers may also try to contact businesses by phone, either in person or by robocall, asking for confidential information or demanding a fee for their PPP application, even promising faster processing after the payment. Similar to the IRS, the SBA does not call PPP applicants for information, and there are no fees associated with PPP applications. Businesses applying for PPP loans may also encounter fake companies claiming that they facilitate applications, which scammers then use to steal the confidential information victims provide.
To avoid being scammed, Social Catfish recommended that businesses interested in applying for PPP loans do their due diligence by following the steps below:
- Don’t pay for a PPP Loan application. The SBA doesn’t require payment to fill out and submit a PPP Loan application. If someone is charging you to fill out an application, chances are its a scam.
- Don’t give your information in response to any suspicious email, text, or phone call. The SBA will not email you out of the blue to fill out a PPP Loan application. If someone is emailing you out of the blue to fill out an application and to give them your information, chances are they are trying to scam you.
- Verify the lender before applying for the loan. Only lenders approved by the SBA can administer PPP Loans. To find out if the lender you are applying with is approved to distribute PPP Loans, click here.
- Don’t click on links in emails. The links in the emails are often filled with viruses and malware that will infect your computer and steal your personal information. They also spoof the application so that you’ll have to give out your personal or business’ confidential information.
- Don’t reply back to any text or email you don’t know. Replying back to them with your personal or company’s confidential information may lead to you getting scammed. The SBA will not email you encouraging you to apply for the loan, you would have to look for the loan yourself.