Three recent studies provide a great reminder of the threats of data breach—and the role workers and IT departments play in either maintaining a company’s defense or letting malware storm the gates.
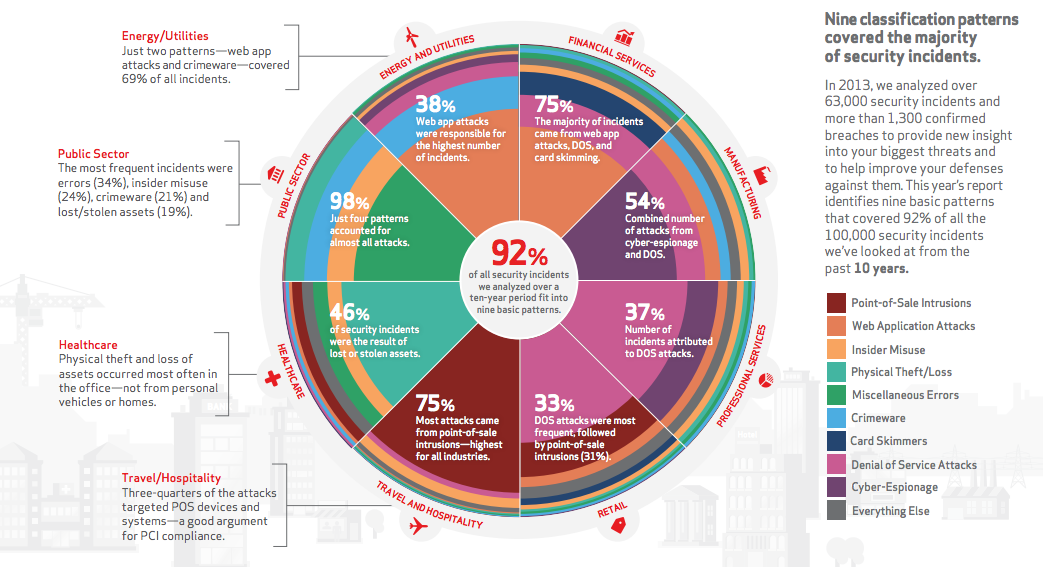
In its 2014 Data Breach Investigations Report, Verizon identified nine patterns that were responsible for 92% of the confirmed data breaches in 2013. These include: point of sale intrusions, web application attacks, insider misuse, physical theft/loss, miscellaneous errors, crimeware, card skimmers, denial of service attacks, and cyber-espionage. They have also identified the breakdown of these patterns in various industries, highlighting some of the greatest sources of cyber risk for your business:
Verizon’s report also offers specific information about the patterns and advice on how to respond to them.
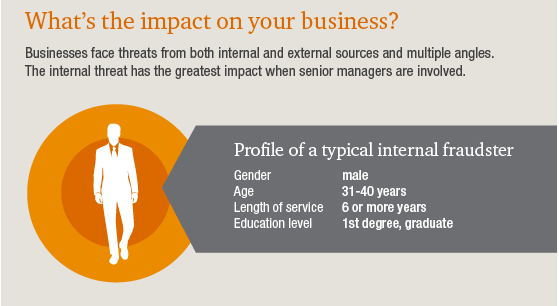
Many sources of vulnerability come from within, and there is less variation than you might expect in terms of who the riskiest workers may be.
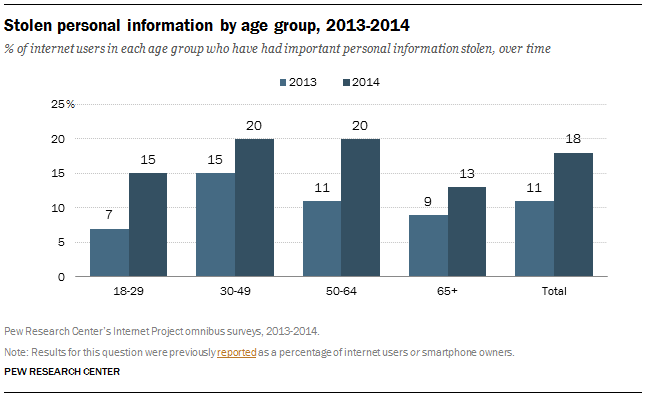
A survey by the Pew Research Center found that 18% of adults have had important personal information stolen online, including Social Security number, credit card, or bank account information—an 8% increase from just six months ago. Further, 21% of adults who use the internet have had an email or social networking account compromised. Two groups that make up a large part of the workforce were hit particularly hard during this period: young adults and baby boomers. The percentage of individuals in these groups who had personal information stolen online doubled between July 2013 and January 2014.
But as this chart shows, all age ranges have experienced a significant amount of data theft as of the beginning of the year.
Indeed, according to meetings-software company TeamViewer, 92% of IT administrators have seen troublesome habits among office workers using company computers. These risky behaviors are frequently known to open the work system to viruses or other malware, including:
- Browsing social media websites (reported by 82% of IT admins)
- Opening inappropriate email attachments (57%)
- Downloading games (52%)
- Plugging in unauthorized USB devices (51%)
- Plugging in unauthorized personal devices (50%)
- Illegal downloads, such as pirated movies, music or software (45%)
- Looking for other jobs (39%)
Further, nine out of 10 IT administrators reported witnessing problems to company equipment because of these actions, including viruses (77%), slow computers (74%), crashed computers (55%), mass popups (48%) and inability to open email (33%). Not only do these behaviors leave corporate infrastructure at risk, but they may endanger the overall HR program, as a vast proportion of IT workers report feeling frustrated, angry and discouraged.
Up to 12% even said that they were considering quitting over these bad behaviors and increased strain on the IT department.
So what can you do? Administrators agreed that better security software, using remote access to fix problems, installing disk cleanup software, integrating automatic backup solutions, and offering the ability to telecommute would all help mitigate these issues and make their jobs easier.