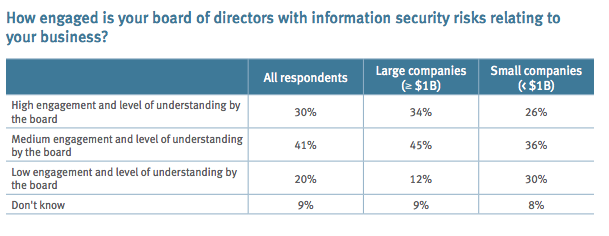
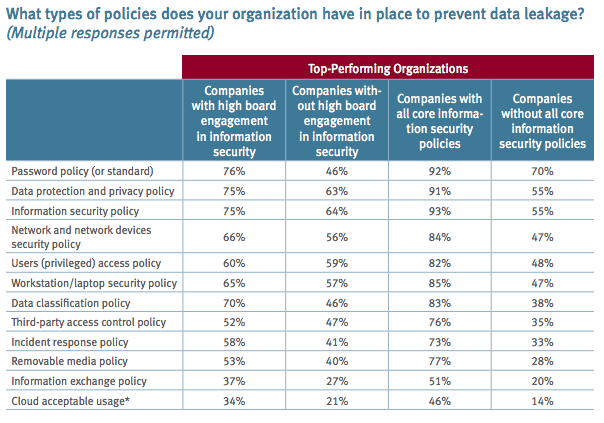
Risk management executives are charged with preparing companies for, and protecting them from, a broad array of emerging risks. Today, there is perhaps no threat that poses more danger than a cyberattack, which could result in a data breach or compromising sensitive information. Given the rapid increase in frequency and severity of high-profile cyberattacks in recent months, organizations must confront cybersecurity issues with greater focus, specificity and commitment.
Of note, an astounding 43% of U.S. companies experienced a data breach in the past year, according to the Ponemon Institute’s 2014 annual study on data breach preparedness, a 10% increase from 2013. These alarming trends are compelling companies to create programs centered on cyber risk awareness, education and preparedness. These programs are vital to the company’s performance and growth; the 2014 Cost of Data Breach Study by IBM and the Ponemon Institute reveals that the average cost to a company from a data breach was about $3.5 million per breach in 2014 – a 15% increase since last year. A company’s intellectual property and customer data may also be compromised in a cyberattack, expanding potential casualties beyond financial losses.
Risk management executives cannot confront this issue alone. Because the responsibilities of management and boards of directors are not limited to having a thorough understanding of cybersecurity issues, they must also be aligned on a clear-cut strategy for both preventing and responding to cyberattacks. This strategy includes efforts to improve education, implement preparation measures before an attack strikes and continued adherence to best practices in all board-related activities.
Awareness and Education
At the most fundamental level, boardrooms must increase the company’s resiliency in the face of cybersecurity threats by increasing awareness of the topic and the associated risks. Unfortunately, boardrooms are struggling to properly educate directors on the topic: a 2012 Carnegie Mellon poll of how U.S. boards are managing cyber risks found that 71% rarely or never review privacy and security budgets, 80% rarely or never review roles and responsibilities, and nearly two-thirds rarely or never review top-level policies. Additionally, more than half of directors surveyed rarely review security program assessments. Every director should make cybersecurity a topic on the board’s agenda and ask questions if there is any confusion or doubt.
Preparation
Directors who are properly aware and educated on the topic of cybersecurity are therefore more prepared and versed in the case of a crisis, not only as individuals but as a collective management team. Given the potential economic consequences of these attacks, it is essential that boardrooms are aligned on the company’s response strategy. It is critical that there be a clear understanding among all levels of a management team about who is responsible for managing this issue. Directors who are familiar with their company’s IT department are better able to determine if the team is equipped to effectively address cybersecurity. Cyber policies must remain updated and understood by all in order to decrease chances for exposure.
Best Practices
A critical part of boardroom preparedness is ensuring that directors are pursuing best practices to decrease changes for exposure and there increase resiliency. There are several practices companies can adopt to ensure this level of preparation:
- Education and preparation: Board members must be educated on cybersecurity and its risks so that they are prepared to manage any situation or crisis. Oftentimes, companies increase their vulnerability by failing to provide directors with the proper tools and information.
- Secure communication: Companies must provide board members with a secure way to share and communicate about critically sensitive information. In order to prevent careless oversharing, this information should never be sent via email. Board members must have a thorough understanding of cloud services. Although these solutions provide an easy way to upload and download files, many have been successfully hacked, compromising private files and email addresses.
- Collaborate and strategize: When directors have a clear understanding of cyber security and the associated risks, they are more equipped to collaborate and strategize around managing any issues related to cybersecurity. With increased board-level conversation about cybersecurity, directors are able to determine if managing cybersecurity is the purview of the audit committee, a separate committee, the company’s IT department or CIO.
Education, awareness and preparedness are critical components to help mitigate vulnerability and risks of cyberattacks. Boardrooms must be open to embracing new strategies and technologies in order to ensure their communication capabilities are secure while remaining fast and accessible. Organizations need to prioritize cybersecurity training to ensure that boardrooms are acting in the company’s best interest and are confident in its cyber crisis response strategy. Although risk has been an evolving factor impacting businesses of all types and sizes throughout history, cybersecurity presents a new challenge—and it is one that can be confronted successfully with the correct management strategy and tools.