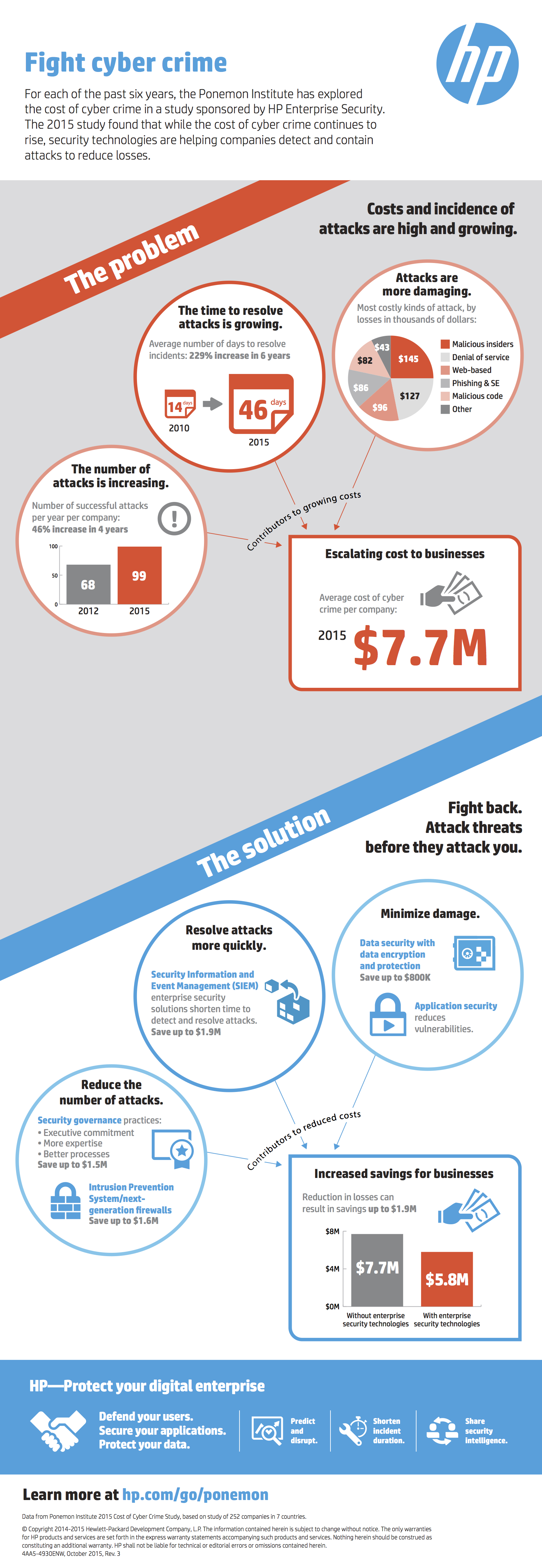
Organizations of all sizes, across all industries have become data breach victims as cyber crooks become more sophisticated in identifying vulnerable targets.
Attackers can compromise an organization within scant minutes in 60% of breaches, reports the latest Verizon Data Breach Investigations Report. Still, insiders persist as one of the biggest fraud perpetrators, costing organizations globally about $3.7 trillion annually in 2014, estimates the Association of Certified Fraud Examiners. The puzzling question is this: With the advances in technology, why aren’t organizations preventing these incidents and why aren’t the offenders being nabbed earlier?
The answer to the insider fraud dilemma lies in a lag in robust risk-management technologies that help organizations identify and prevent insider fraud, especially in such industries as banking. With this type of breach, tracking behavior becomes a key component of managing risks and threats proactively. While basic data tracking isn’t new, what is fresh is grasping the internal behavior of employees in a real time, comprehensive view across multiple platforms and applications.
Unfortunately, disparate legacy systems that don’t share information easily create larger problems by limiting an organization’s ability to monitor across all systems. And siloed information makes it impossible to find “normal” employee behavior that should serve as a benchmark for day-to-day activity.
For example, banks must be on the lookout continually for employees who exhibit illegal behavior when, say, handling a dormant bank account, who are manipulating customer information or who collude with colleagues.
By benchmarking regular employee activity and leveraging link analysis to spot relationships across accounts or employees, banks also can monitor for and spot instances of employee negligence that can offer cyber crooks easy access to customer data.
Sophisticated surveillance technology exists that lets organizations monitor and detect suspicious behavior in real time, then analyze and develop an evidence trail. Organizations can use the following activities to help identify and prevent an internal threat before it escalates and triggers substantial monetary and brand damage.
Enable searchability: Organizations can deploy a user-friendly monitoring system with Google-like searchability features with highly specific behavioral criteria. Moving beyond clunky legacy systems to technology that is intuitive eliminates user error and enables more advanced rule-based monitoring.
- Record screen activity: Gaining visual evidence of illegal activity while it occurs is critical for use during an investigation. Technology that records screen-by-screen activity at the application level creates the comprehensive data trail needed for courtroom presentation.
A combination of these activities can assist organizations in identifying anomalies in employee behavior, track digital activities and contrast them with an employee’s normal routine or that of a peer group’s pattern. If incongruities appear, advanced risk-management technology develops a data trail and a case strong enough to stand up in court. Leveraging these measures, insider fraud can be discovered at an earlier stage to prevent customer data breaches and malicious attacks.