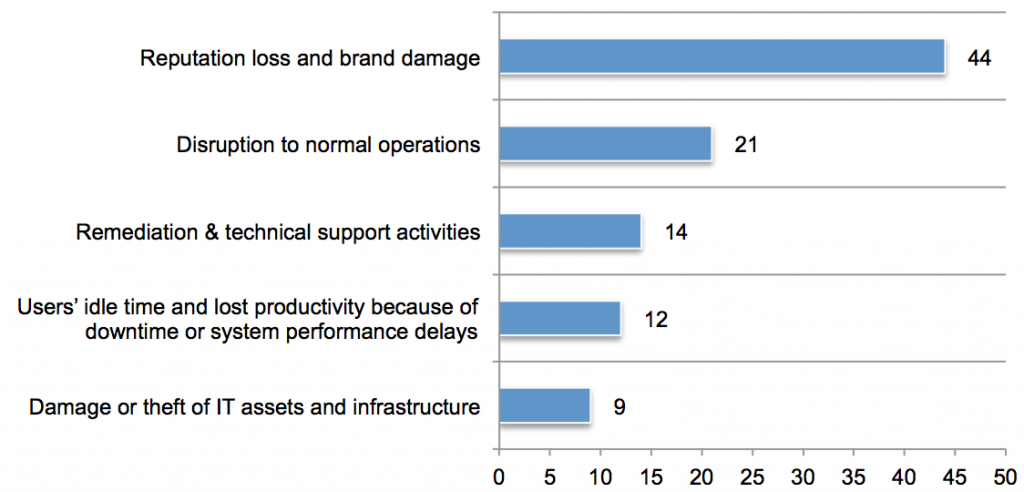
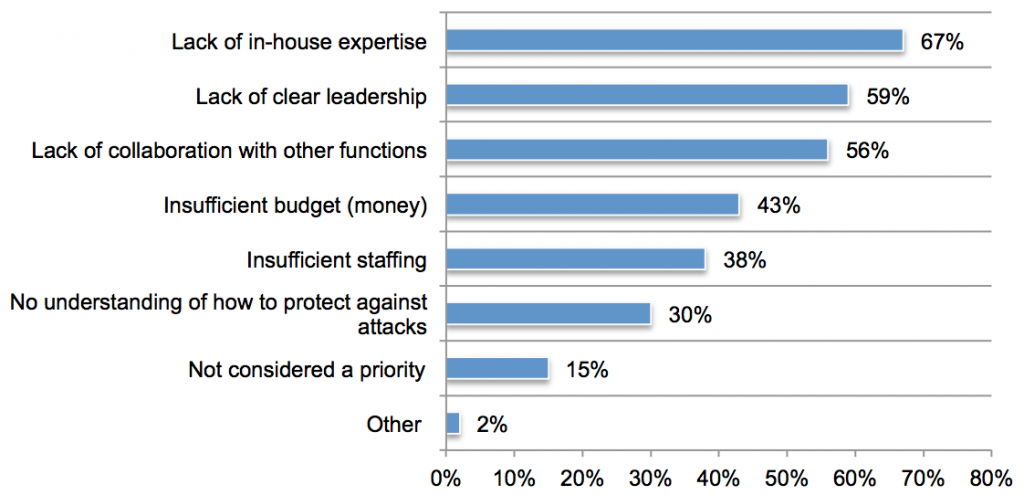
As ransomware continues to spread and payment costs increase, cyber insurance rates have gone up exponentially. As a result, it is more important than ever for companies to understand their cyber vulnerabilities and exposures so they can ensure they are properly covered. One way to do this is through analytics.
In a presentation at the RIMS TechRisk/RiskTech virtual event, Scott Stransky, managing director and head of the Cyber Risk Analytics Center at Marsh McLennan, outlined some of the key data that can help companies get a full view of their risk.
According to Stransky, there are five categories of data that are most important to determining your risk profile. Much of this data is in publicly available datasets that insurers already consult, so it is important that you have a handle on this information as well so you know how underwriters and other outsiders are viewing you:
- Firmographics: company demographics like revenue, employee count, industry, location, and company hierarchy
- Historical incidents: past breaches and insurance claims
- Technographics: a company’s external cybersecurity posture including the presence of firewalls, open ports, frequency of system patching, as well as internal cybersecurity practices like password management and data encryption
- Scoring: combines firmographics, historical incidents and technographics into a single number that designates the level of vulnerability
- Loss modeling: brings all elements together to predict the likelihood and cost of an event
Armed with this data, companies can take steps to make it easier to access optimal cyber insurance coverage and better insurance pricing. These could include improving your security and claims posture by addressing potential cybersecurity gaps, updating incident response plans, and identifying vendor partners to help improve security posture or respond to incidents. Companies can also explore policy structure options in terms of different program components (limits, attachment, coverage, risk retention, etc.
) and consider alternative terms and conditions.
Finally, it is important to provide robust underwriting data by using assessment tools to minimize the need for supplemental applications, preparing for additional questions from underwriters, and highlighting significant cybersecurity updates and improvements over the past year.
In particular, companies should focus on what Stansky called the top 12 cybersecurity controls for risk mitigation, resilience and insurability:
- Multifactor authentication (MFA)
- Endpoint detection and response
- Secured, encrypted and tested backups
- Privileged access management
- Email filtering and web security
- Patch and vulnerability management
- Cyber incident response planning and testing
- Cybersecurity awareness training
- Hardening techniques, including remote desktop protocol mitigation
- Logging and monitoring/network protection
- End-of-life system replacement
- Vendor/digital supply chain risk management
For those that missed RIMS TechRisk/RiskTech, you can register and access the virtual event here. Sessions will be available on-demand for the next 60 days.