Last night, President Obama delivered the annual State of the Union. Unsurprisingly, the speech covered a variety of topics ranging from foreign affairs to civil rights to climate change. While these issues may ultimately have little impact on the insurance industry or risk management, there were two topics raised that could be of significant interest.
The first relates to tax reform:
“As Americans, we don’t mind paying our fair share of taxes, as long as everybody else does, too. But for far too long, lobbyists have rigged the tax code with loopholes that let some corporations pay nothing while others pay full freight. They’ve riddled it with giveaways the superrich don’t need, denying a break to middle class families who do,” Obama said.
For the past few years, the Obama administration’s annual budget proposal has included a measure that would deny a tax deduction for certain reinsurance premiums paid to foreign-based affiliates by domestic insurers. While the administration and some members of Congress deem this deduction a “loophole,” it is actually a commonly used and effective risk management tool.
Doing away with this particular “loophole” would force the industry as a whole to reduce the size and scope of its U.S. offerings. A previous economic impact study found that this proposal would reduce the net supply of reinsurance in the United States by 20%, thus increasing prices by to billion annually for the same coverage.
If Congress does take up comprehensive tax reform, this is certainly an initiative that many in the industry will need to keep an eye on.
The other issue is cybersecurity:
“And tonight, I urge this Congress to finally pass the legislation we need to better meet the evolving threat of cyberattacks, combat identity theft, and protect our children’s information. If we don’t act, we’ll leave our nation and our economy vulnerable. If we do, we can continue to protect the technologies that have unleashed untold opportunities for people around the globe,” the president said.
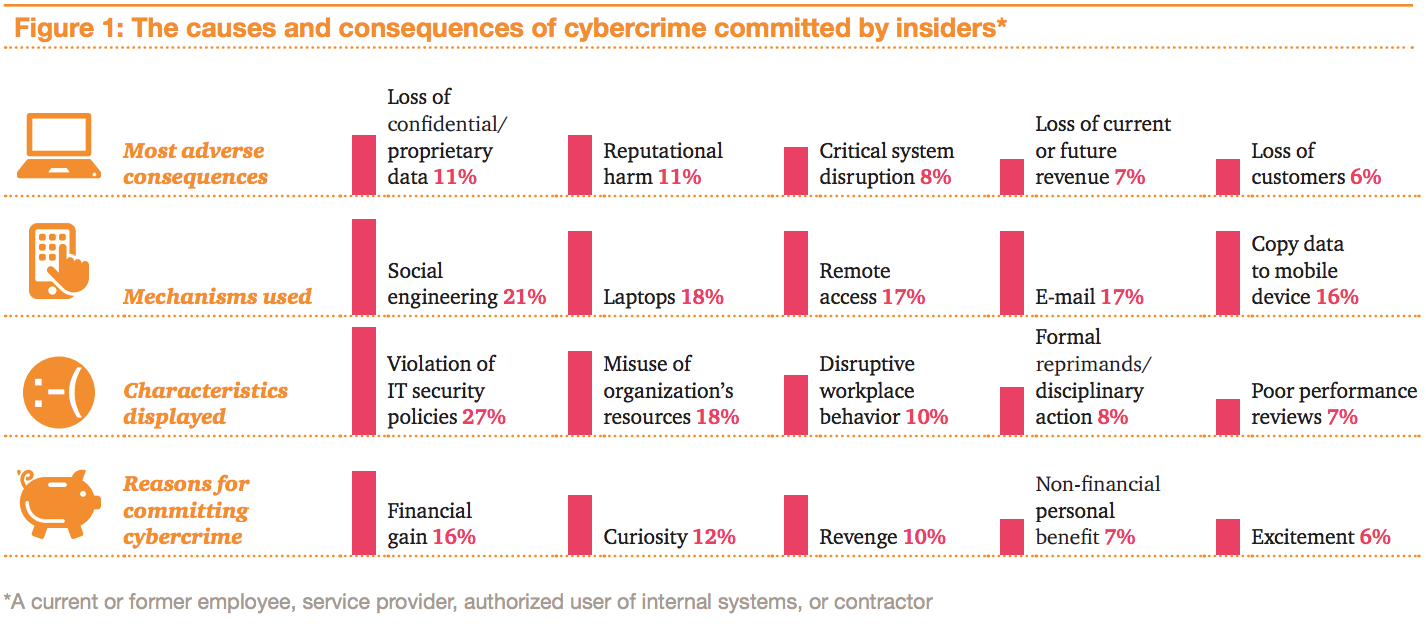
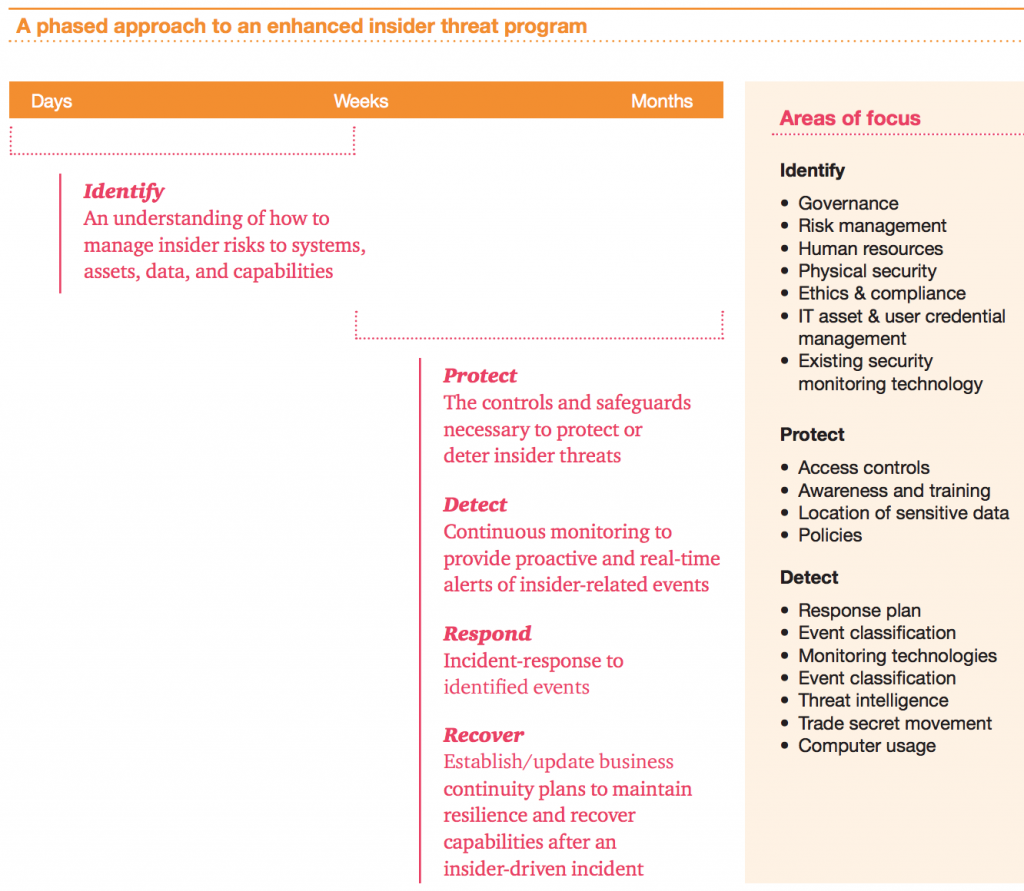
Cybersecurity and the management of cyberrisks is certainly one of the hottest topics in the industry. While it remains unclear what proposed legislation will look like, we will almost certainly see at least one major piece of cybersecurity legislation introduced in the next few months. Previous efforts have focused on information-sharing. With the number of attacks and damage inflicted only increasing, however, it is quite possible that new legislation may be even broader in scope.
It is also important to note that simply including something in a State of the Union address does not always translate into real action. It is quite possible that tax reform will get tabled again as various factions are unable to agree. It’s also possible that Congress will be unable to come up with a cybersecurity bill that achieves many of its goals without undermining the privacy or personal security of individuals. It is, however, an overview of the administration’s priorities for the coming year, and that does still carry some weight.