As technology becomes more critical to company success, the number of cyberattacks has climbed.
As a result, cyberrisk has become one of the top risks for companies around the world, according to the Marsh-Microsoft Global Cyber Risk Perception Survey. Almost two-thirds of survey respondents identified cyberrisk as one of their organization’s top-five risk management priorities—almost double the percentage who rated cyber as a top risk in a 2016 study, Marsh said, adding that respondents whose organizations had been successfully attacked were slightly more likely to prioritize cyberrisk than those who had not.
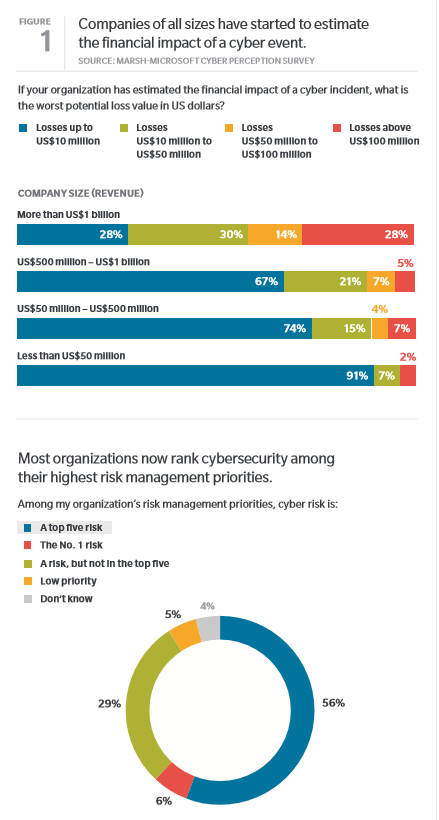
Despite these concerns, however, the study notes that just one in five respondents said they are “highly confident in their organization’s ability to manage and mitigate cyberrisk or respond and recover from an attack.” This was especially the case among corporate directors, who play an important role in protecting their organization from cyber threats. While about 70% of respondents who identified as board members said they ranked cyberrisk as a top-five concern, only 14% said they were “highly confident” in their organization’s ability to respond to an attack.
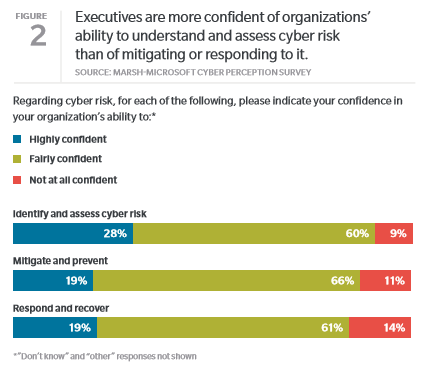
Board Disconnect
While organizations have traditionally relied on IT staff to manage cyberrisks, the structure of oversight is evolving in many companies as risks accelerate. Stakeholders from across the enterprise are looking beyond prevention to include risk assessment, mitigation and cyber resilience.
Asked about cybersecurity structure, however, 70% of respondents named their IT department as a primary owner and decision-maker of the risk.
This was more often true for smaller companies, as larger organizations tended to spread the responsibility for cyberrisk—from a low of 13% in the smallest organizations (many of which may not have a separate risk management function) to 58% in the largest organizations with more than $5 billion in revenue, the study found.
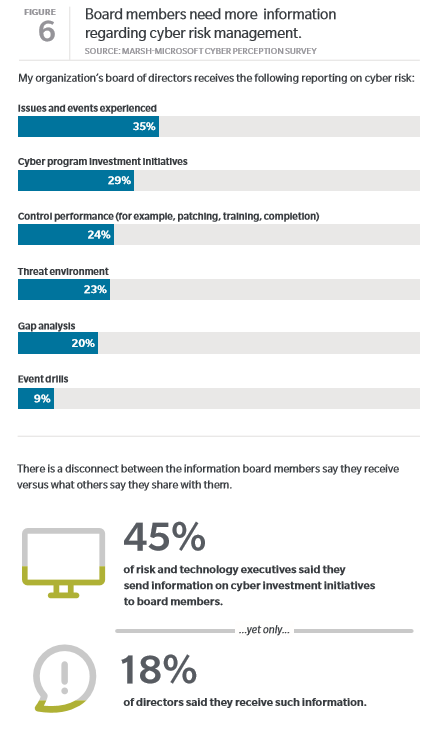
Ideally, boards should view cyberrisk management as part of their overall perspective on enterprise risk management. In organizations where the board is involved, however, the study found a disconnect:
Corporate directors often appear to either not understand the information on cyberrisk they receive, or to not be receiving it all. For example, 53% of chief information security officers, 47% of chief risk officers, and 38% of chief technology/information officers said they provide reports to board members on cyber investment initiatives. Yet only 18% of board members said they receive such information.
This information gap illustrates a need to develop cyberrisk economic/business models that facilitate shared dialogue including common language among IT, the board, and other corporate departments.
This disconnect also reinforces the need for a cross-functional approach to cyber risk governance, according to the study.

 DWR Photo: Lake Oroville on Jan. 19, 2018 with lake levels at 707 feet.
DWR Photo: Lake Oroville on Jan. 19, 2018 with lake levels at 707 feet.
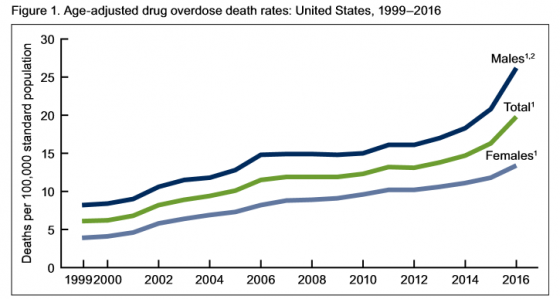
Authors of the report noted, “The pattern of drugs involved in drug overdose deaths has changed in recent years. The rate of drug overdose deaths involving synthetic opioids other than methadone (drugs such as fentanyl, fentanyl analogs, and tramadol) doubled in a single year from 3.1 per 100,000 in 2015 to 6.2 in 2016. Additionally, it’s important to note that many drug overdose deaths may involve multiple drugs.”
Of people age 15 and above:
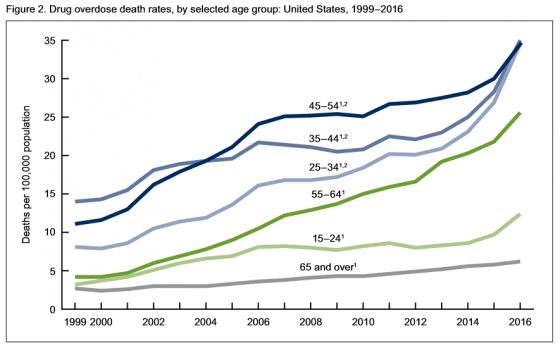
• Rates of drug overdose deaths increased from 1999 to 2016 for all groups studied.
• Rates in 2016 were highest for people between the ages of 25 and 54.
• From 2015 to 2016, the drug overdose death rates for adults age 45-54, 55-64 and 65 and above went up 15%, 17% and 7% respectively, the CDC said.
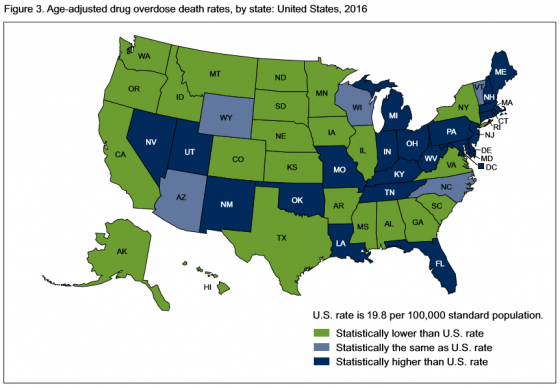
 In 2016, 22 states and the District of Columbia had overdose death rates that were statistically higher than the national rate. States with the highest number of overdose deaths were: West Virginia, with 52 per 100,000; Ohio with 39.1; New Hampshire with 39; District of Columbia with 38.8; and Pennsylvania, which had 37.9 deaths per 100,000.
In 2016, 22 states and the District of Columbia had overdose death rates that were statistically higher than the national rate. States with the highest number of overdose deaths were: West Virginia, with 52 per 100,000; Ohio with 39.1; New Hampshire with 39; District of Columbia with 38.8; and Pennsylvania, which had 37.9 deaths per 100,000.
States with the lowest age-adjusted drug overdose rates were: Iowa, which had 10.6 deaths; North Dakota, 10.6; Texas, 10; South Dakota, 8.4; and Nebraska, which had 6.4 deaths.
 In it’s most recent study, Quest Diagnostics found that workforce use of illicit drugs across the board—including cocaine, marijuana and methamphetamine—has climbed to the highest rate in 12 years.
In it’s most recent study, Quest Diagnostics found that workforce use of illicit drugs across the board—including cocaine, marijuana and methamphetamine—has climbed to the highest rate in 12 years.
Overall positivity in urine drug testing among the combined U.S. workforce in 2016 was 4.2%, a 5% relative increase over last year’s rate of 4%—the highest annual positivity rate since 2004 (4.
5%), according to an analysis of more than 10 million workforce drug test results.