CFO just published an excellent article on emerging risks. It starts off talking about the day-to-day work of a CFO, Kevin Gordon, who says risk management is on his mind “every minute of the day.” It goes on to discuss the risk assessment work he did last year about how the European debt crisis could potentially harm his employer.
Most people, however, aren’t like Kevin Gordon.
Most people recognize that emerging risks, like Eurozone default, are out there.
Then they do nothing more.
The article explains.
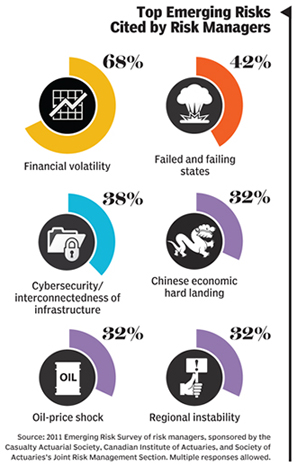
By their nature, emerging risks are difficult to anticipate.
buy atarax online www.artforhealingfoundation.org/wp-content/uploads/2023/10/jpg/atarax.html no prescription pharmacy“An emerging risk is either something we’ve never seen before or something we haven’t seen for a long time,” says Max Rudolph, owner of Rudolph Financial Consulting.
buy spiriva inhaler online www.artforhealingfoundation.org/wp-content/uploads/2023/10/jpg/spiriva-inhaler.html no prescription pharmacyThey can do extensive damage. The European debt crisis, the Japanese earthquake and tsunami, the Arab Spring uprisings — these once-emerging risks all had a ripple effect in 2011 on supply chains, commodity costs, and liquidity.
Experts say such risks are growing. “The interconnected nature of the global economy is increasing the speed at which emerging risks arise and cascade, as well as the magnitude of their impact,” says Alex Wittenberg, partner and head of global risk at management consultancy Oliver Wyman Group.
A new report from Oliver Wyman suggests that executives understand the threat. Seventy-eight percent of more than 200 executives surveyed in the report said they want to increase their capabilities when it comes to managing emerging risks. As it stands, the same executives said they devote just 28% of their risk-management efforts, on average, to emerging risks.
I recommend reading the rest of the piece. As for suggestions on how executives can better prepare, the author suggests keeping “close tabs on market trends, global economic developments, and regulatory activities, and be prepared to jump into action quickly.”