Hack Wilson was an MLB star in the 1920’s, but he had a drinking problem. Realizing his potential, Hack’s manager pulled him into the dugout and said, “If I drop a worm into a glass of water, it swims around fine. If I drop it into a glass of whiskey, it immediately dies. What does this prove?”
Hack responded, “If you drink whiskey, you’ll never get worms.”
Hack’s observation, while misguided, provides a lesson in the difficulty of training and educating employees. Over the next several weeks, I hope to provide a step by step walk through of the RIMS Risk Maturity Model (RMM) for enterprise risk management (ERM), and while doing so provide a framework that can be used to educate, implement, and enhance the ERM program at your own organization.
Recently the target of a third party study of ERM programs, enterprise risk management maturity as measured by the RIMS Risk Maturity Model, is proven to add 25% to a corporation’s bottom line value, but how is that value achieved? What is it about ERM that makes these organizations more efficient, better operating, and ultimately more successful?
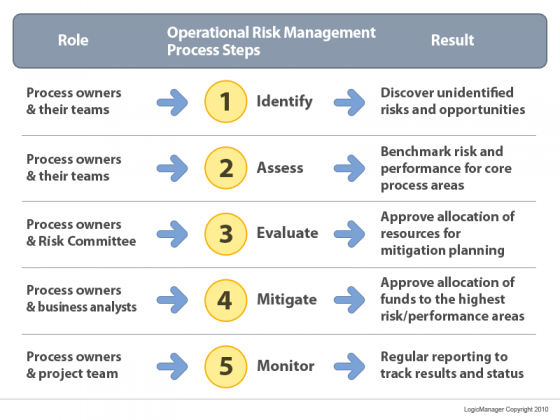
The answer is that the RIMS RMM is a step-by-step guide on how to implement, improve and measure the adoption of the best practices of ERM defined by ISO, COSO and other ERM standards. The RMM is broken down into seven attributes, and the resulting culture, processes, tools, and structure that allow organizations to realize potential opportunities while managing adverse events and surprises. As outlined by the RMM, enterprise risk management is particularly effective in addressing cross functional or silo specific challenges and gaps by providing a common framework.
That’s a loaded response, and as shown above, educating process owners, risk managers and even executives about the value of ERM can be tricky.
That’s the value of the RMM—it breaks down ERM into practical requirements, allowing organizations to assess their current capabilities, while providing concrete guidance for a pathway forward.
The seven core attributes are:
ORM-based approach—Executive support within the corporate culture
Risk appetite management—Accountability within leadership and policy to guide decision-making.
Root cause discipline—Binding events with their process sources.
Uncovering risks—Risk assessments to document risks and opportunities.
Performance management—Executing vision and strategy utilizing balanced scorecard.
Business resiliency and sustainability—Integration into operational planning.
In a few upcoming posts, we’ll cover more fully what a mature ERM program looks like from the perspective of one of our seven attributes. The goal is to improve your organization’s ability to manage risk, while exploring the correlation between business value and ERM maturity.
For an introduction to the RIMS approach to ERM, click here to watch LogicManager’s video on Getting Started with ERM.