One of most effective risk management philosophies is to work smarter, not harder, implementing holistic tools, such as predictive analytics to ensure it is minimized. More often than not, companies implement blanketed management programs, applying the same strategies to all employees regardless of performance. With this approach, employers waste time and effort focusing on employees who are not at risk, leaving room for at-risk employees to go unnoticed. On an opposing front, many companies use the “squeaky wheel” approach, diverting all of their attention to employees that actively demonstrate troublesome behaviors. While this approach targets a greater amount of at-risk employees, it still leaves room for some to go undetected.
Alternatively, a strategic employee-specific management program allows employers to identify at-risk employees regardless of how “squeaky” they are. The theory behind an employee-specific management program is simple – monitor your employees for changes that indicative risky behavior.
More often than not, these changes are subtle and undetectable to employers. Even with a team of risk management professionals, the necessary attention to detail is near impossible for companies with thousands of employees. So, how can we efficiently monitor for and detect these subtle changes?
Enter predictive modeling
Predictive modeling is an effective tool that addresses the needs of many industries – turning hundreds of thousands of data points into tangible data that can predict anything from consumer demands to credit scoring and anything in between. Challenging traditional personnel management practices, predictive modeling shines a light on the psychology behind today’s work force.
Predictive modeling has become an essential tool for companies across the globe, playing a role in nearly every industry, from marketing to finance, trucking, and the risk management sector. It provides employers with a unique look into the subtle, yet profound, fluctuations in employees’ behaviors that often go undetected. Examining thousands of data points and trends from past events, predictive modeling possesses the power to identify changes in behavioral patterns and predict the outcomes of future events, arming managers with the knowledge needed to proactively intervene with the right employee, on the right subject, at the right time to avoid events such as workers’ compensation claims and voluntary employee turnover.
With this information on hand, employers are able to replace their blanketed risk management program with a streamlined, employee-specific program, saving time and money—and most importantly, lowering risk. To understand the value offered through predictive modeling, one must understand that most employees would not be classified as “at-risk” at the time of employment. It’s the events that occur after the onboarding that mold the employee’s work behavior and create liabilities.
Notably, it is not just work-related problems that can put employees in the “at-risk” category. Often, medical or personal issues can cause changes in an employee’s work habits and behaviors. Tapping into historical data, predictive modeling is able to detect subtle changes and bring at-risk employees forward for remediation. With this information on-hand, managers can proactively connect with their employees to address an issue before it snowballs into a costly incident.
As one of the most risk-prone industries, the transportation space leverages predictive modeling to monitor employees for unsafe driving behaviors which can result in hefty violation fines and accidents. For example, if a driver is dealing with an ill grandmother, he or she may be paying less attention to the road and spending more time on the phone scheduling doctor appointments and responding to calls. Based on past performance, his or her manager will be alerted that the employee is hard-braking more than usual and spending more time in idle. By opening the channels of communication between the driver and manager, they can work together to identify a solution, whether it be an adjusted work schedule or a reduced workload.
Additionally, predictive modeling can help managers focus on causation rather than correlation. When an incident occurs, many managers tend to put emphasis on what happened, not why it happened. As a result, they often work to fix the correlating issue rather than addressing the root cause.
By analyzing the data gathered through predictive modeling, managers can reflect on the changes in employee behaviors, corporate management or workload leading up to the incident. Recognizing the fluctuation leading up to the accident, managers can proactively monitor for similar incidents and intervene.
An example of this is a risk all managers dread – workers compensation claims. Many companies have accepted workers comp claims as a cost of doing business, failing to understand the factors leading up to the claim. Prior to filing a claim, an employee may be feeling under-motivated and overworked, often putting in the bare minimum and cutting corners with little attention to detail. The reduced attention span lands him or her in trouble when there is a resulting injury on the job and puts the company at risk for a costly claim. With predictive modeling, the manager is able to identify the changes in the employee’s work performance and identify the root cause. Further down the line, the manager can also monitor for similar situations and proactively work with the employee to make his or her work experience more positive.
As managers continue to look beyond traditional methods to better manage their employees and overall company operations, they will be able to capitalize on innovative technologies, such as predictive analytics, to help retain top talent, reduce risk, and build better, longer-lasting relationships with their employees. With growing adoption of proactive risk management solutions, today’s workplace will continue to become a safer, stress-free environment for all.
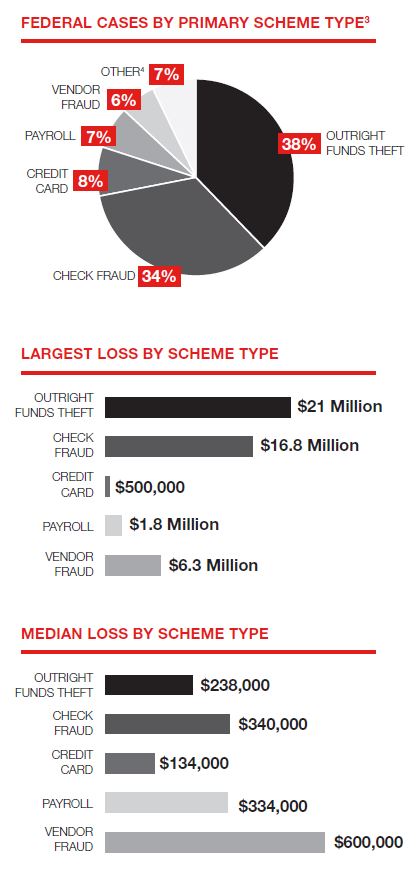
 four out of five had less than 100 employees and more than half had fewer than 25 employees. Smaller organizations also had the largest losses, according to the survey. Financial services companies were most at risk (21%), followed by non-profits, labor unions and municipalities.
four out of five had less than 100 employees and more than half had fewer than 25 employees. Smaller organizations also had the largest losses, according to the survey. Financial services companies were most at risk (21%), followed by non-profits, labor unions and municipalities.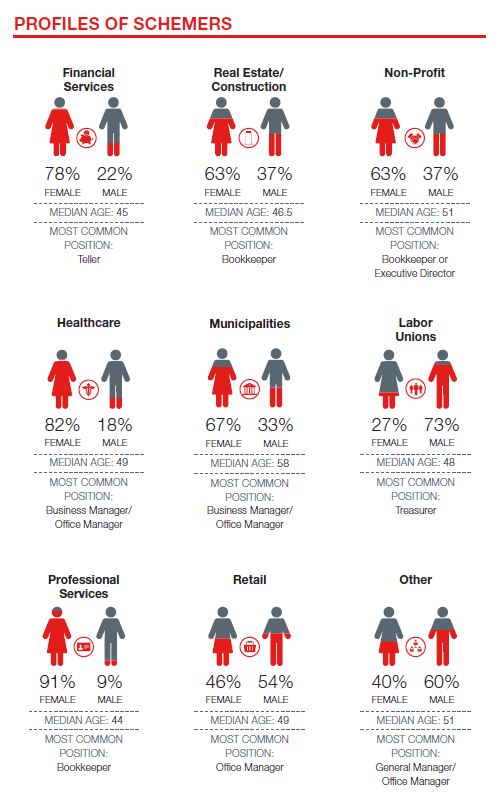 In fact, the survey found that 58% showed no recovery of their losses.
In fact, the survey found that 58% showed no recovery of their losses.