Impostor emails, dubbed “business email compromise” by the FBI, are increasing and targeting companies of every size, in every part of the world. Unfortunately, victims often do not realize they have been had until it’s too late. There are no security tool alarms and there is no ransom note. But because systems appear to be running as normal, everything seems like business as usual. And that is the point, according to Proofpoint’s study, “The Imposter in the Machine.”

From New Zealand to Belgium, companies from every industry have suffered losses, the study found. Here is a small sampling of recent impostor attacks during the last year:
- A Hong Kong subsidiary at Ubiquiti Networks Inc. discovered that it had made more than $45 million in payments over an extended period to attackers using impostor emails to pose as a supplier.
- Crelan, a Belgian bank recently lost more than $70 million due to impostor emails, discovering the fraud only after the company conducted an internal audit.
- In New Zealand, a higher education provider, TWoA, lost more than $100,000 when their CFO fell victim to an impostor email, believing the payment request came from the organization’s president.
- Luminant Corp., an electric utility company in Dallas, Texas sent a little over $98,000 in response to an email request that they thought was coming from a company executive. Later it was learned that attackers sent an impostor email from a domain name with just two letters transposed.
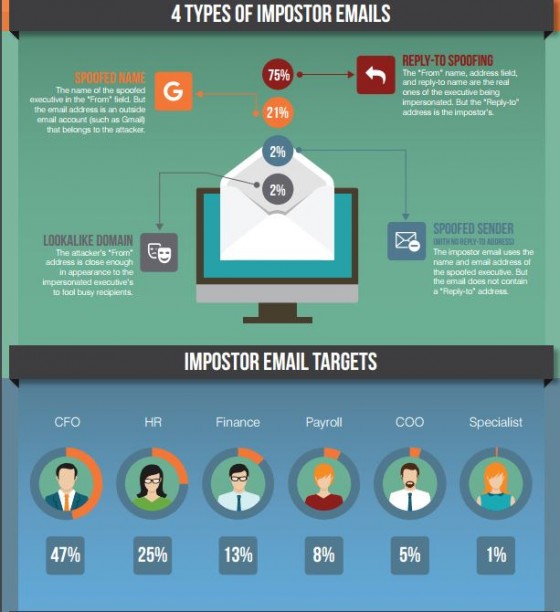
Most often, company executives are targeted, with two common angles. In one case, the always-traveling executive is studied by attackers, who use every resource available to understand the target’s schedule, familiar language, peers and direct reports. Because the executive is frequently on the road, direct reports who routinely process payments can easily be victimized.
Another ploy involves suppliers and how they invoice.
For example, the supplier’s language, forms and procedures are used to change bank account information for an upcoming payment. If the attackers are successful, a company may find that they have been making payments to them for months without knowing it.

For more about the risks of phishing, check out “The Devil in the Details” and “6 Tips to Reduce the Risk of Social Engineering Fraud” from Risk Management.
