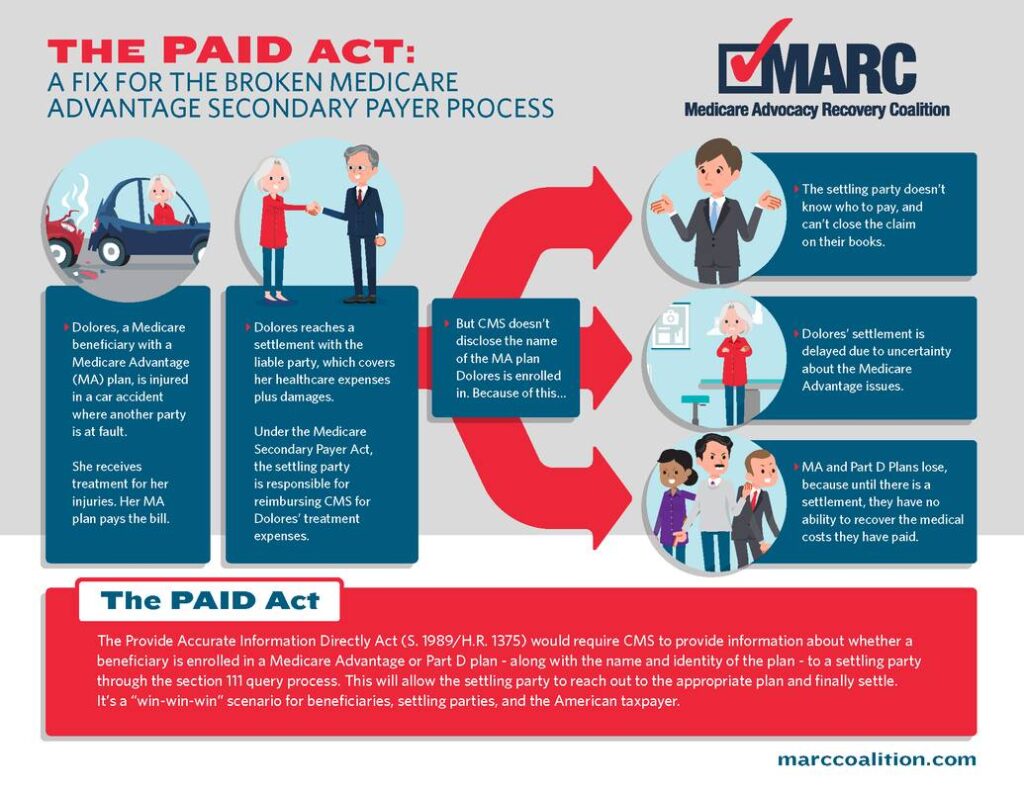
On December 11, the Provide Accurate Information Directly (PAID) Act was signed into law as a part of the funding bill to keep the government running. A top priority of RIMS Advocacy since it was introduced in 2019, the PAID Act will fix a current flaw in Medicare Secondary Payer (MSP) compliance. Specifically, the PAID Act amends 42 U.S.C. § 1395y(b)(8)(G) to require that the Centers for Medicare and Medicaid Services (CMS) expand its Section 111 Query Process to identify whether a claimant is currently entitled to, or during the preceding 3-year period has been entitled to, Medicare Part C (Medicare Advantage) and/or Medicare Part D (prescription drug) benefits. If so, CMS is then required to provide the names and addresses of any such Medicare plans through the Section 111 Query Process. Included in the bill is a one-year implementation provision that requires the fix to go live by December 11, 2021.
The bipartisan bill was introduced in 2019 by Republican Senator Tim Scott of South Carolina and Democratic Congressman Ron Kind of Missouri in the House of Representatives. “Today, the PAID Act has taken a pivotal step closer to becoming law, filling in Medicare-related potholes that have cost seniors, Main Street job creators, and the American taxpayer millions of dollars over the years,” Sen. Scott said when the bill passed. “Decades-old regulations and bureaucratic red tape have caused confusion and avoidable litigation in the MSP for far too long, and by eliminating those problems we can help seniors and families across the country.”
The fix in the PAID Act will essentially settle the increased number of lawsuits that have been filed by Medicare Advantage Plans asserting recovery rights against insurers, including claims for “double damages” under Medicare’s private cause of action provision. If CMS provides settling parties with the name and identity of the plan and the dates of coverage, they can better resolve and repay MSP liabilities associated with settlements, judgments or awards. With these changes, there will be a more efficient solution for beneficiaries, taxpayers and employers.
Proponents of the PAID Act assert, in part, that this legislation will now help insurers better identify and address potential Part C and/or Part D recovery claims by allowing them to obtain entitlement and plan information in a more programmatic manner using Section 111’s Query Process.
Currently, there is no such centralized process or system for insurers to obtain this information. When an applicable plan submits the required query process data elements to CMS, if the queried individual is identified as a Medicare beneficiary, the query response only confirms that they are enrolled in Medicare. It does not provide any information as to the “type” of Medicare program in which the individual is enrolled. The PAID Act will change this to better identify whether a claimant is enrolled in Medicare Advantage and/or Part D.
The text of the PAID Act states that CMS must provide the following information to the applicable plan through the Section 111 Query Process:
(I) whether a claimant subject to the query is, or during the preceding 3-year period has been, entitled to benefits under the program under this title on any basis; and (II) to the extent applicable, the plan name and address of any Medicare Advantage plan under part C and any prescription drug plan under part D in which the claimant is enrolled or has been enrolled during such period.
With the PAID Act now law, RIMS will monitor the CMS implementation process and provide feedback as needed. RIMS worked closely with the Medicare Advocacy Recovery Coalition (MARC) to support their efforts to get this bill passed. Check out their infographic on the Medicare issue the PAID Act should fix: