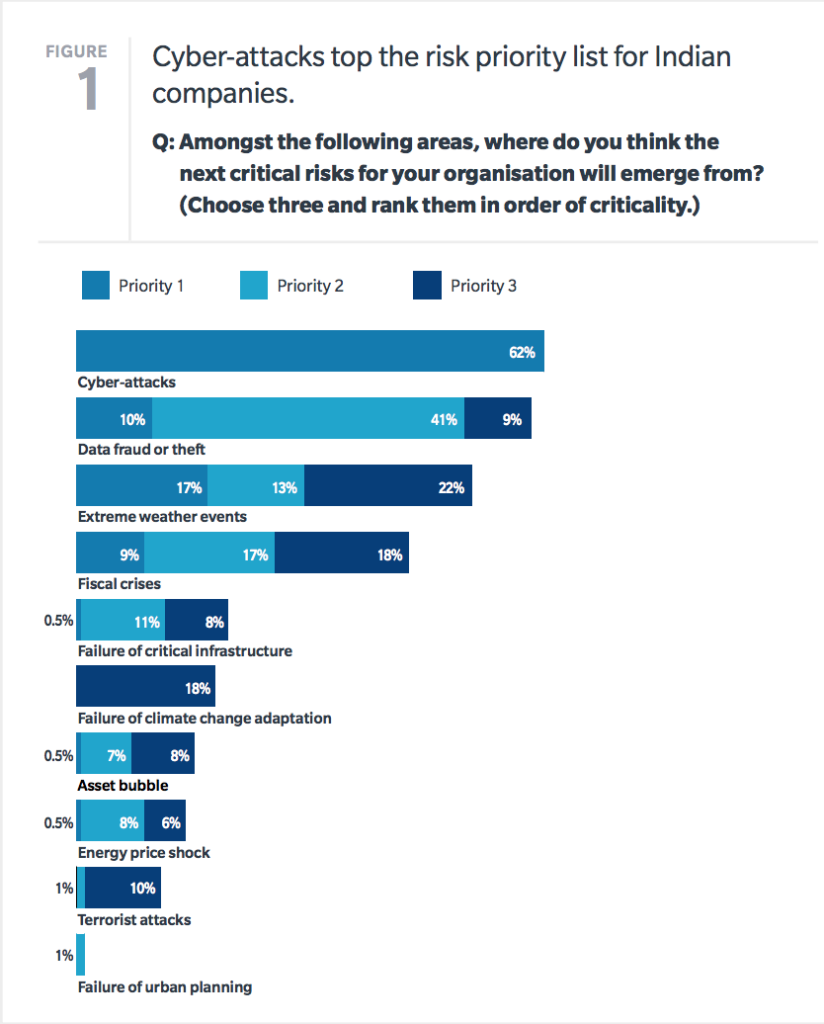
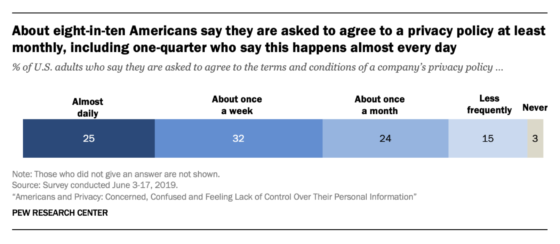
For businesses that thrive on person-to-person transactions, cash is quickly being replaced by cards, as well as tap-to-pay systems, mobile wallets and QR-based payment systems. These technologies will continue to dominate the market in the near future, but the long-term future of the payment card industry will likely be shaped by the impact of blockchain and artificial intelligence. These developments will eventually also impact risk management, marketing and financial planning, as they present opportunities for serious risks, including fraud. Hence, it is imperative for risk management professionals to plan for these short- and long-term changes in the industry.
Strong risk monitoring requires proactively assessing threats and planning mitigation measures to minimize risk impact on the company or organization. To help mitigate payment fraud risks, businesses can take the following steps:
Train your Employees Regularly
The more regularly you train your employees, the more likely are they to spot suspicious behavior, no matter what payment technology the business uses. Repeated and regular trainings are essential because employees tend to forget what they have learned with time. These training workshops should teach the workers to never accept damaged cards from customers, confirm customer identities, and never enter a card number manually.
Use Contactless and EMV-Enabled Terminals
As payment technology changes, businesses must evaluate what options are safest and least prone to fraud. Currently, businesses should use EMV (short for Europay, Mastercard and Visa), which involves chips embedded into payment cards—a significant step in making transactions safer. The introduction and adoption of EMV-enabled secure terminals, particularly when using PIN and EMV security together, has helped merchants and customers prevent fraudulent transactions.
Contactless smartcards such as chip and magnetic stripe cards use contactless payment, which can present another secure way to process transactions. Most EMV terminals are also enabled with contactless payment. At such terminals, a fast and secure transaction is possible using Near Field Communication (NFC) or Radio-Frequency Identification (RFID) via smartcard or smartphone. If a merchant chooses to use contactless payment without PIN, they can put a limit to the amount spent on each contactless transaction to further minimize risk.
Beware Uncommon Transactions
Transactions that involve unusually large purchases could be a sign of potential fraud. Businesses should examine such transactions closely and confirm the identity of the customer. Similarly, if several purchases are made with a card in a short timeframe, it could indicate that the card was stolen and being used by someone other than the owner.
Maintain Online Security
As merchants and consumers shift to contactless and EMV-enabled point of sale terminals, risk has shifted towards online transactions. To mitigate this risk, it is important for online businesses to use the Address Verification Service (AVS), which verifies that the billing information matches the one registered with the card issuer. Vendors should also ask for Card Verification Value 2 (CVV2) to verify that the user has the card in hand when placing the order. Another important check is to put a limit on an IP address for the number of cards it can use for online transactions.
Prevent Employee Fraud
Employee fraud is always a major concern for risk management professionals. Businesses should remember to keep an eye on credit card activity, particularly returns, as employee theft often shows up in fake discounts or returns. Companies should create alerts that set limits on returns at stores and notify management any time those limits are exceeded.