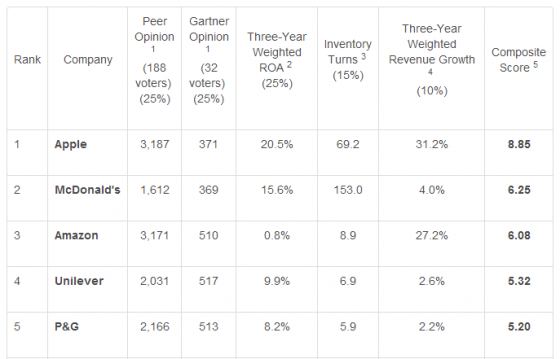
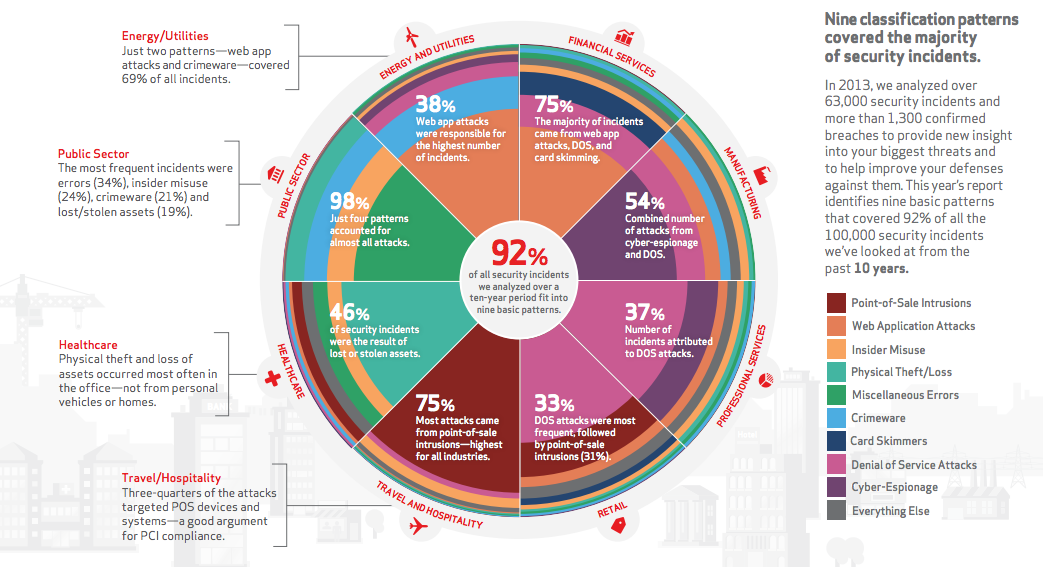
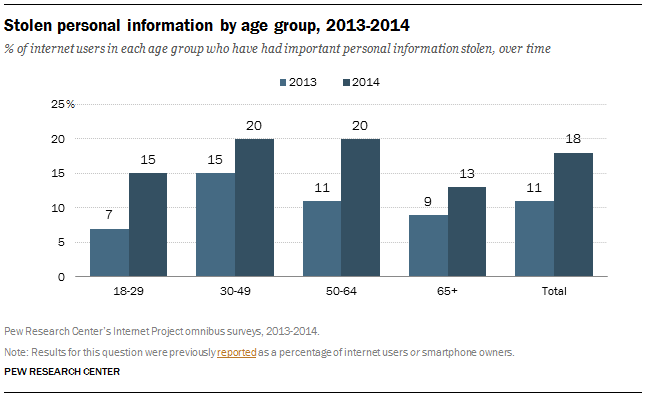
It’s bound to happen. At some point, nearly every risk manager is faced with the need to purchase or replace a risk management information system (RMIS).
The decision may be driven by the obsolescence of an existing RMIS, a need for different or more robust capabilities, organizational changes and general systems upgrades that facilitate wider application of data analytics.
The good news is that RMIS long ago transcended their traditional roles in claims tracking, analytics and benchmarking, and they continue to evolve. Today RMIS offer an array of sophisticated capabilities, including applications to support enterprise risk management and global strategic risk management initiatives.
To get the RMIS that best meets your current and emerging needs, thoughtful consideration is called for. In light of exciting RMIS developments, here are a few ideas that might help.
Rethink your RFP. A rigid RFP process with a defined set of parameters and limited detail might leave you with insufficient information and result in a choice that is less than optimal. With many risk managers now required to address more complex exposures, provide sophisticated analytics, and drive down costs, contemporary RMIS platforms offer the versatility to support a spectrum of risk management needs. So starting out with a broader conversation about needs analysis versus capabilities can equip RMIS buyers to make better decisions.
Remember, people are key. Sure, new technology is exciting. However, as highlighted in the 2014 Advisen/Bickmore RMIS Review, client service is a top reason for organizations to switch RMIS providers. Do the people on the other end of the phone have the experience to understand your complex business and needs? Can they advise or make the changes within your system? Do they have authority to do so without submitting tickets or routing your problem to another department?
While it is reasonable to assume any RMIS vendor will need to get up-to-speed on the specific needs and priorities of your organization and department, you don’t want to be training a less experienced RMIS vendor or employees at your expense.
Usability: How quickly can your team get up to speed? Unlike a decade earlier–or even just a few years ago–virtually all RMIS users are quite familiar with general website navigation based on their Internet use. Ideally, the RMIS you select will have a simple user experience with navigation that’s fairly intuitive and functions and unique features that are for the most part self-explanatory. Historically, RMIS systems were “siloed” in terms of how their capabilities were developed, so information had to be searched for and located. Today, the workflow of a RMIS should coincide with the user’s organic thought process–and not the other way around.
Scalability: What happens as needs evolve? Today, virtually every RMIS provider claims its system is scalable to handle growing organizations. While that may be true, the question for the buyer to ask is: “At what expense?” When interviewing potential RMIS providers, be sure to ask plenty of “what if” questions so you come away with a clear understanding of what might be involved in scaling, changing, or even reconfiguring a RMIS system.
Does each and every change come with a price tag, or is the system’s architecture built to accommodate on-the-fly configuration changes?
There is no doubt these are challenging times for risk professionals and their organizations. In this environment, choosing the RMIS that is right for you can go a long way toward making your job a lot easier and your team more successful. Happy shopping!