While employee malfeasance rarely takes down entire companies, it can result in serious fines, sanctions, court judgments, settlements and reputational damage. Big data analytics is one way leading companies are able to mitigate risk, by proactively detecting threatening or illegal behavior.
Traditional ERM Approaches Won’t Do
Compliance officers do their best. They generally work within enterprise risk management (ERM) frameworks to introduce corporate policies and procedures, conduct risk avoidance training and audits, and create inter-disciplinary committees. They work with IT to run compliance auditing software on critical structured data, including financial databases and transactional applications.
By targeting only well-behaved structured data, however, compliance officers can lose sight of one key fact—structured data is a small percentage of organizational data. Data storage analysts report that most organizational data are only 15% to 20% structured data and 80% to 85% unstructured.
This leaves a huge volume of data that presents serious compliance risk to IP, especially electronic communications.
While e-mail, instant messaging, texting and social media are ingrained in our culture, traditional auditing software does not focus on communications. These threats often evade notice until the damage is done.
Here are some ways threats can escape the radar of employers that have traditional ERM approaches:
- Limited ability to analyze unstructured data. The inability to monitor unstructured data leaves the company open to regulatory consequences and other risk.
- Keyword searching to winnow down data sets often delivers a high volume of false positive results. Filtering techniques such as keyword searches may not be highly accurate and require intensive manual review.
buy ciprodex online www.urologicalcare.com/wp-content/uploads/2023/10/jpg/ciprodex.html no prescription pharmacy
The result is higher cost and longer timeframes for manual-review projects.
buy paxil online www.urologicalcare.com/wp-content/uploads/2023/10/jpg/paxil.html no prescription pharmacy - Potential security issues. Communication platforms are rapidly proliferating. Employees might be sharing inappropriate corporate information on social media, yet these mentions often go unmonitored by the company, potentially missing evidence of employee misconduct.
- Complex regulatory changes. Many governmental and industry regulations are already complicated, and their revisions only intensify complexity. For example, since introducing Dodd-Frank, regulators have written 224 of 400 expected rules and continue to modify existing rules.
- Case-by-case approaches. Case-centric approaches to litigation, investigations and regulatory compliance matters impede applying learning and attorney work product on these cases to other matters. This inability lengthens legal reviews and investigations and multiplies costs. Case-based discovery also makes it difficult to discover widespread risky communications between employee groups and outside organizations.
- Geographic and organizational silos. Relevant data is spread across different storage locations and eDiscovery platforms, creating distinct data silos.
A Cautionary Tale
Here is an example of risk that can go undetected until it’s too late, as it did at Wells Fargo. Banker 1 is responsible for reaching high quarterly sales goals. His manager increases his sales goals for the next quarter. Banker 1 emails a colleague complaining about how his goals are impossible to meet. Banker 2 suggests he try a creative process called “pinning,” which consists of a banker enrolling an actual customer in online banking to create a “sale.” The banker fills in the customer’s name and address but puts in a fake email address so the customer never receives banking communications. The banker meets his sales goals—and hopes the customer never finds out.
How Big Data Analytics Can Help
Analytics tools are already omnipresent in eDiscovery and compliance reviews. They include predictive coding, email threading and concept searching. They are highly useful for culling large data volumes to more manageable sizes. They also locate meaningful text and concept patterns so that reviewers can strategically work with high priority documents.
The catch is that these analytics can only filter to a point, and only work on a single-case basis. No matter how the case management software learns from tagging and work product, that learning cannot be applied across multiple matters if it resides on different review platforms or with different vendors. Each time a new case begins, reviewers and their software must start over. This leads to very long and repetitive document review processes, already the single most expensive activity in eDiscovery. Clients and attorneys also risk exposing sensitive information as the matter makes its way between document review platforms and multiple stakeholders.
A big data approach, versus specific analytics tools can continuously consolidate billions of documents into a central repository. It can also apply machine and human learning to enable the reporting of trends, new data relationships, and fresh insights into data across all cases—not just a single matter—for greater efficiency, cost control and risk mitigation.

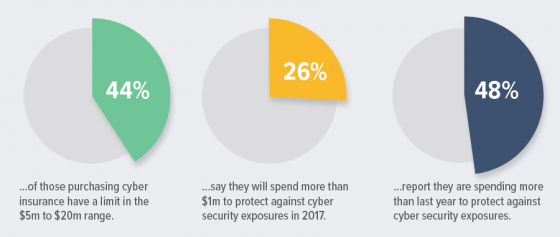 Key findings from this year’s RIMS Cyber Survey include:
Key findings from this year’s RIMS Cyber Survey include: