 Now through Feb. 14 is the busy season for the online dating and matchmaking industry. Heavier traffic can present risks to these sites, demanding added precautions. Ronald Sarian, vice president and general counsel (and default risk manager) at
Now through Feb. 14 is the busy season for the online dating and matchmaking industry. Heavier traffic can present risks to these sites, demanding added precautions. Ronald Sarian, vice president and general counsel (and default risk manager) at eHarmony spoke to Risk Management Monitor about the types of risks he faces—particularly regarding data and cybersecurity—and how he protects the “#1 trusted dating site for like-minded singles,” where “Every day, an average of 438 singles marry a match they found on eHarmony.” (For those familiar with its commercials, the song now stuck in your head can be played in a new tab here—don’t fight it.)
eHarmony spoke to Risk Management Monitor about the types of risks he faces—particularly regarding data and cybersecurity—and how he protects the “#1 trusted dating site for like-minded singles,” where “Every day, an average of 438 singles marry a match they found on eHarmony.” (For those familiar with its commercials, the song now stuck in your head can be played in a new tab here—don’t fight it.)
Risk Management Monitor: You joined eHarmony following a data breach in 2012 in which 1.5 million users’ passwords were compromised. What steps did you take to prevent a recurrence?
Ronald Sarian: Following that breach, we put everything we did under a microscope and brought in Stroz Friedberg to aid our investigation and help improve our processes. We ultimately decided to migrate all credit card data off-site to CyberSource, a third-party vendor. When we need to charge a credit card we get the key from the vendor and then return it when we’re done. We wrote transmission gateways out of all of our internal apps so things aren’t communicating with each other so easily. This way, if there is an attack, it will be “quarantined.” We also employed extensive layering for the same purpose.
We put a much more sophisticated logging system in place, hired a full-time security engineer, and started performing more firewall audits and regular white hat hacks to try to detect vulnerabilities. And we improved our on-boarding and off-boarding for employees.
RMM: What are the prevalent risks you face leading up to Valentine’s Day and how do you mitigate them?
RS: We face risks all year long, but this time of year there are just more of them. There are always fraud issues we deal with and people try to launch bot attacks to take down our systems and cause us grief. We believe we utilize industry best practices for all these issues. For example, to try to prevent fraudsters from getting into the system we have sophisticated business rules that look at keywords or phrases used when filling out the intake questionnaire—certain words or phrases indicate the probability of a fraudster. Misuse of the English language can sometimes signal a problem. These raise red flags in our system.
Our questionnaire is quite elaborate and evaluates psychological factors in order to determine personality traits. We have essentially 29 different dimensions of compatibility we look at and try to glean all these dimensions so we can match you with someone who is typically 80% or higher in each. If you answer the questions in a certain manner for most of the questionnaire and we see a major inconsistency toward the end, for example, that can indicate something is fishy.
We also look at suspicious IP addresses. We utilize these practices all year round but scrutiny is heightened at this time of year and especially when we have free communication weekends. We’re pretty good at sorting these people out before they can communicate. Our system has been developed over 17 years and is constantly being improved as threats change and fraudsters become more sophisticated.
RMM: How else is risk management used in eHarmony’s strategies and operations?
RS: A goal of mine is to adapt the ISO 27001 ERM framework for eHarmony. I believe we have the best practices in place to achieve that when the time and finances are right. It’s quite a bit of work to get the certification and I don’t know if that would happen this year but it’s something I want to do because I think it would be great for us. It basically requires a holistic, top-down look at your entire operation.
This is not only from a tech standpoint but from a personnel standpoint as well.
Many breaches start internally, most of the time unintentionally, so people should, for example, know not to click on a link in an email from an unknown source. You also need to assure your vendors are utilizing the appropriate safeguards and you must have a security incident management plan in place. There are many other requirements, of course. I believe we essentially have the information security management system (ISMS) envisioned by ISO 27001 in operation right now. We just need to make it official.

 5. In fact, not only is failing to prepare for an attack or breach risky, it’s foolish, Kathleen McGee, internet & technology bureau chief for the Office of the Attorney General of the State of New York said in Monday’s opening address. She added that not reporting a breach in a timely fashion has its own set of legal and reputational risks, referring to
5. In fact, not only is failing to prepare for an attack or breach risky, it’s foolish, Kathleen McGee, internet & technology bureau chief for the Office of the Attorney General of the State of New York said in Monday’s opening address. She added that not reporting a breach in a timely fashion has its own set of legal and reputational risks, referring to  urity industry, noting that, “the defense trails the offense by about five years.” Comparing the newest waves of protection software to a strong rookie pitcher, he said, “A new pitcher may come along and strike everybody out as he goes through the league a few times. But eventually he gets figured out and [hackers] figure it out,” he said. “It needs at least a year of being attacked for real,” to find the gaps in efficiency, and leads to the “the kind of experimentation that will yield better results.”
urity industry, noting that, “the defense trails the offense by about five years.” Comparing the newest waves of protection software to a strong rookie pitcher, he said, “A new pitcher may come along and strike everybody out as he goes through the league a few times. But eventually he gets figured out and [hackers] figure it out,” he said. “It needs at least a year of being attacked for real,” to find the gaps in efficiency, and leads to the “the kind of experimentation that will yield better results.”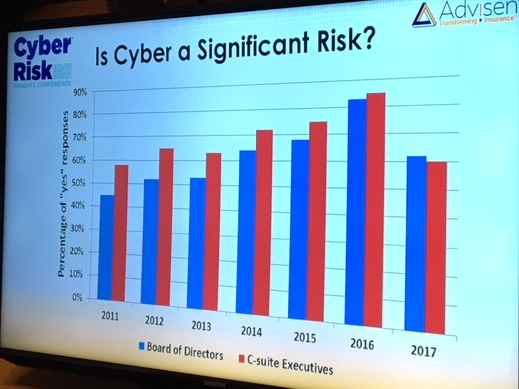 Advisen
Advisen