LAS VEGAS—One of the hottest topics in cyberthreat detection right now is the rise of malvertising, online advertising with hidden malware that is distributed through legitimate ad networks and websites. On Monday, Yahoo! acknowledged that one of these attacks had been abusing their ad network since July 28—potentially the biggest single attacks, given the site’s 6.9 billion monthly visits, security software firm Malwarebytes reported.
In the first half of this year the number of malvertisements has jumped 260% compared to the same period in 2014, according a new study released at the Black Hat USA conference here today by enterprise digital footprint security company RiskIQ. The sheer number of unique malvertisements has climbed 60% year over year.
“The major increase we have seen in the number of malvertisements over the past 48 months confirms that digital ads have become the preferred method for distributing malware,” said James Pleger, RiskIQ’s director of research. “There are a number of reasons for this development, including the fact that malvertisements are difficult to detect and take down since they are delivered through ad networks and are not resident on websites. They also allow attackers to exploit the powerful profiling capabilities of these networks to precisely target specific populations of users.”
How does malvertising work—and why is it taking off right now? “The rise of programmatic advertising, which relies on software instead of humans to purchase digital ads, has generated unprecedented growth and introduced sophisticated targeting into digital ad networks,” the company explained. “This machine-to-machine ecosystem has also created opportunities for cyber criminals to exploit display advertising to distribute malware. For example, malicious code can be hidden within an ad, executables can be embedded on a webpage, or bundled within software downloads.”
The study also noted that, in 2014, there was significantly more exploit kit activity (which silently installs malware without end user intervention) than fake software updates that require user consent. In 2015, however, fake software updates have surpassed exploit kits as the most common technique for installing malware. Fake Flash updates have replaced fake antivirus and fake Java updates as the most common method used to lure victims into installing various forms of malware including ransomware, spyware and adware.
Last week, enterprise security firm Bromium also released a new study focused on the rising threat of malvertising, finding that these Flash exploits have increased 60% in the past six months and the growth of ransomware families has doubled every year since 2013.
“For the last couple of years, Internet Explorer was the source of the most exploits, but before that it was Java, and now it is Flash; what we are witnessing is that security risk is a constant, but it is only the name that changes,” said Rahul Kashyup, senior vice president and chief security architect at Bromium. “Hackers continue to innovate new exploits, new evasion techniques and even new forms of malware—recently ransomware—preying on the most popular websites and commonly used software.”
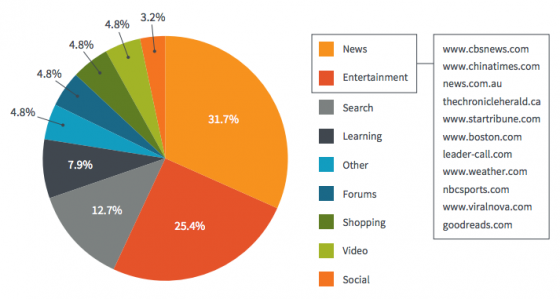
One of the riskiest aspects of these exploits is that users do not have to be accessing sites that seem remotely suspect to be exposed. According to Bromium’s research, more than 58% of malvertisments were delivered through news websites (32%) and entertainment websites (26%). Notable websites unknowingly hosting malvertising included cbsnews.com, nbcsports.com, weather.com, boston.com and viralnova.com, the firm reported.
With that in mind, IT and cybersecurity teams have to adapt to meet these new threats, which are evolving far faster than detection tools, including antivirus, behavioral analysis, network intrusion detection, and the basic safe browsing guidelines issued to employees regarding their use of work devices.
“The key takeaway from this report is that, at large, the Internet is increasingly becoming ‘untrustworthy.’ Attackers are now using popular websites to launch malware via online ads, which makes things difficult for IT security teams,” explained Rahul Kashyup, SVP and chief security architect at Bromium. “This risk should be well understood and factored in for any organization while building a ‘defense-in-depth’ security stack. Regular patching and updates definitely help to limit the exposure to potential attacks, but that might not be feasible for large organizations.
It is advisable to evaluate non-signature based technologies that can thwart such attacks in a reliable way and prevent infections on end-user devices.
”
According to Bromium, the websites that most frequently serve as malvertising attack sources are: