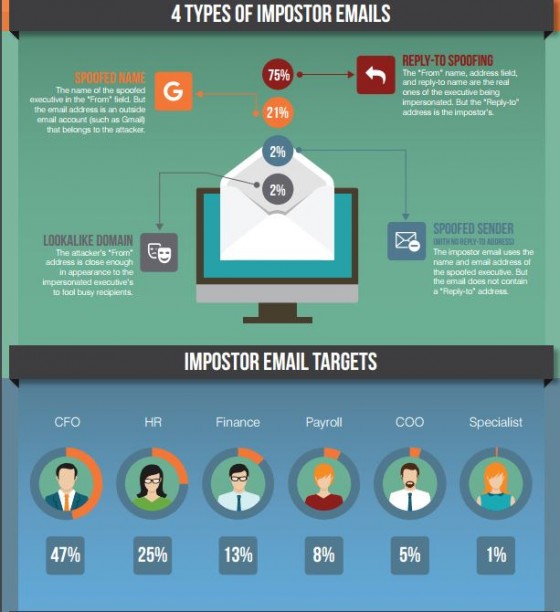
Social engineering is the latest cyberrisk giving companies fits and large financial losses. A social engineering loss is accomplished by tricking an employee of a company into transferring funds to a fraudster. The fraudster sends an email impersonating a vendor, client, or supervisor of the company and advises that banking information for the vendor/client has changed or company funds immediately need to be wired at the “supervisor’s” direction.
The email looks authentic because it has the right logos and company information and only careful study of the email will reveal that the funds are being sent to the fraudster’s account. Unsuspecting and trusting employees unwittingly have cost their companies millions of dollars in connection with social engineering claims.
But when companies look to their traditional insurance program, they are usually met with the unhappy surprise that they do not have coverage for such a loss.
Most assume that the loss will be covered by the crime/fidelity policy that nearly all companies have. Insurers, however, have denied coverage for social engineering claims under those policies, claiming that the loss did not result from “direct” fraud. Insurers contend that the crime policy applies only if a hacker penetrates the company’s computer system and illegally takes money out of company coffers. In the case of a social engineering claim, company funds have been released with the knowledge and “consent” of an employee, albeit the employee has been induced by fraud to release the funds. Policyholders and insurers are currently litigating the scope of coverage under traditional crime policies nationally with mixed results.
Some crime policies also contain exclusions that may pose specific barriers to social engineering claims. For example, many traditional crime policies contain a “voluntary parting” exclusion that bars coverage for losses that arise out of anyone acting with authority who voluntarily gives up title to, or possession of, company property. In addition, some insurers have put overly broad exclusions on crime policies that are directed toward eliminating coverage for many cyber risks, including social engineering claims.
Given the prevalence of social engineering claims and the clear market for companies looking to insure against such risks, some insurers have begun to offer an endorsement that provides coverage for social engineering claims.
buy flagyl online https://galenapharm.com/pharmacy/flagyl.html no prescription
The coverage may be subject to a sublimit and may include coverage for some, but not all, social engineering risks. The coverage also might be subject to additional exclusions.
Like all insurance policies, the precise words of the endorsement matter and, therefore, should be carefully reviewed.
Finally, and most important of all, social engineering coverage will not automatically be added to a company’s policy and not all insurers will provide such coverage. Therefore, companies should review their current insurance program with their insurance professionals and experienced coverage counsel to determine whether they have appropriate coverage that is in line with the market for social engineering claims.
Check out “6 Tips to Minimize the Risks of Social Engineering Fraud” from Risk Management.