 Is your audience changing? Are your products still relevant and addressing customers’ needs? Are there opportunities for organization to predict—or least make an informed guess—about the future of the market or other trends? Answers to these difficult questions are often buried in the overwhelming amount of data organizations are already collecting and storing.
Is your audience changing? Are your products still relevant and addressing customers’ needs? Are there opportunities for organization to predict—or least make an informed guess—about the future of the market or other trends? Answers to these difficult questions are often buried in the overwhelming amount of data organizations are already collecting and storing.
In this digital age, data analytics is a hot topic for businesses and their risk professionals. In fact, nearly half of the survey respondents (46%) from the RIMS MARSH Excellence in Risk Management XV survey agreed that to successfully become digital, using data and analytics to unlock value and make decisions faster was critical.
Where to begin?
Gathering, organizing and understanding data can be such a daunting task that many often choose to put it off for “another day.
”
Paul Koziatek, Enterprise Risk Manager for Coca-Cola Beverages Florida, LLC and an upcoming presenter for the RIMS’ Aug. 2 webinar titled “Mother Lode—Driving Results from Your Data Analytics” offered strategies for risk professionals to get their hands dirty and embark on this data-crunching adventure.
Before getting started, risk professionals must realize that data analytics is an ongoing process, not a project. “One of the biggest misconceptions is that it is a one-off deal,” he said. “It’s the complete opposite. Data analytics is a living, breathing adventure. If you go in with a project-like mindset, you’ll be doomed from the start.”
A great advantage risk professionals have today is the software available to them. “There are a lot of risk professionals who are under the impression that data analytics software is expensive. That might have been the case several years ago, but now RMIS systems can be tailored to meet specific needs and purchased in pieces.”
Additionally, he notes that data analytics programs must constantly be reevaluated. As information begins to trickle in, risk professionals might have to take a closer look at what they are requesting. “Risk professionals should examine and maintain the program frequently because the original variables used to obtain the data might not always produce the same outcomes.”
Engaging co-workers
A data analytics program requires information and clarification from various subject matter experts from a range of business units. To build these relationships, risk professionals need support from leadership to ensure others in the organization are committed to the process and aware of leadership’s expectations.
With that support, risk professionals can overcome a lack of urgency from others in the organization. “There is a potential to hear feedback such as ‘There is not enough time,’ or ‘We’ll get to that later.’ It is the risk professional’s job to help department leaders see that risk management can create value and is not just a cost-center,” Koziatek said. “Consider those experts as tools and resources. They are going to be the ones who pull the data and provide what it is you need.
The ability to explain to those experts exactly what you need to get the job done is important. If that’s not accomplished, you can wind up with a bunch of usable or corrupt data.”
He added, “Sales, marketing and planning teams are a great place to start. In some organizations already have the tools, packages and software risk professionals need to analyze data.”
Quick Wins
Quick wins will be a bit different for every organization. Many data analytic adventures get started because of a legacy of bad workers’ compensation cases or a rash of claims against the organization. “For some, a quick win might be focusing the program on a hot, troublesome and expensive activity to quickly reduce the cost of the risk. Key to determining what might constitute a quick-win is understanding the business’s strategy. “Listen to the board of directors, to the CEO and CFO. Then tailor your analytics to that communication and help drive the company’s strategy,” Koziatek said.
Realizing the Value
Data analytics is like a treasure hunt. With the right information, guidance and support, organizations and their risk professional can discover hidden potential, revenue streams, cost-saving measures and new opportunities.
More than figuring out where the weak points are for the organization, data analytics uncovers connections. “Data analytics is all about the correlation between different variables and outcomes.
It offers great value by allowing risk professionals to identify those variables before it’s too late,” Koziatek said.
He points to workers compensation and employee-related injuries as an example of data analytics at its best. His organization found that the frequency of injuries and claims were highest among short-term employees (two years or less). Thus, the correlation between claims, length of employment and training were quickly realized. “Without data analytics it might take an organization much longer to really identify the root cause of the activity and, as time goes by, more money can be lost.”
Data analytics’ greatest value for the risk professional is its ability to justify and gain even more support for risk management initiatives. “There is nothing more important than having the data to back up my solutions, my ideas and my needs. That is what the board, senior executives and business leaders want to see. Without these analytics, their outcomes and the reports we produce as a result, it would be extremely difficult to ‘sell’ my ideas to leadership,” Koziatek concluded.

 Ten years ago, many companies didn’t even ask about using encryption to protect data. Over the years, that has changed. More security and privacy professionals began to see it as an option in their cybersecurity defense.
Ten years ago, many companies didn’t even ask about using encryption to protect data. Over the years, that has changed. More security and privacy professionals began to see it as an option in their cybersecurity defense.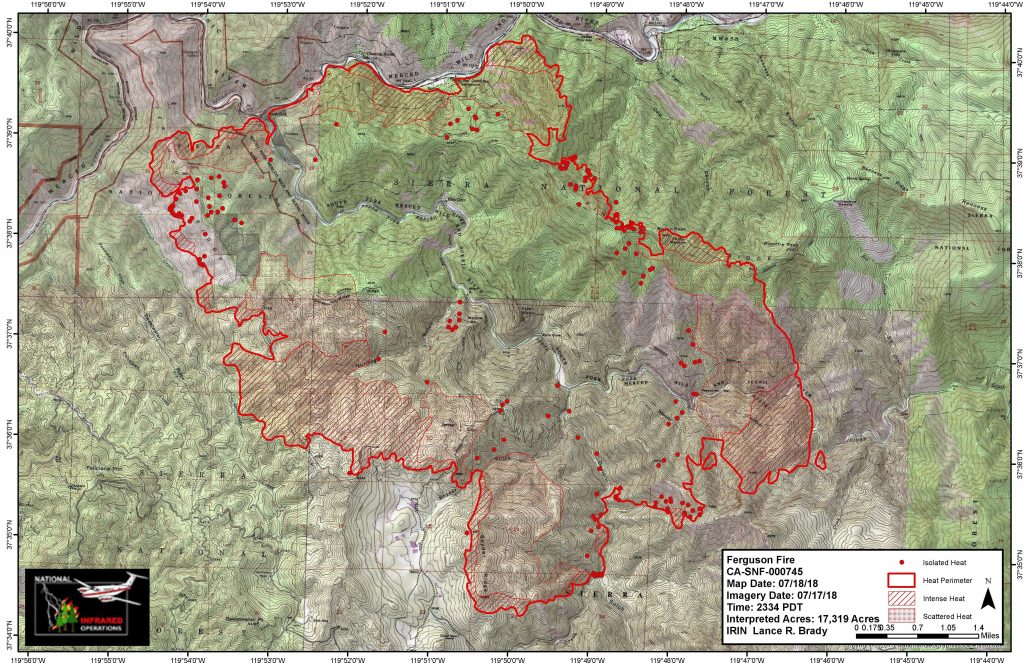 The Ferguson wildfires have been spreading in Mariposa County, California on the western edge of Yosemite National Park for days, burning 27 square miles and taking the life of one firefighter.
The Ferguson wildfires have been spreading in Mariposa County, California on the western edge of Yosemite National Park for days, burning 27 square miles and taking the life of one firefighter. Is your audience changing? Are your products still relevant and addressing customers’ needs? Are there opportunities for organization to predict—or least make an informed guess—about the future of the market or other trends? Answers to these difficult questions are often buried in the overwhelming amount of data organizations are already collecting and storing.
Is your audience changing? Are your products still relevant and addressing customers’ needs? Are there opportunities for organization to predict—or least make an informed guess—about the future of the market or other trends? Answers to these difficult questions are often buried in the overwhelming amount of data organizations are already collecting and storing.