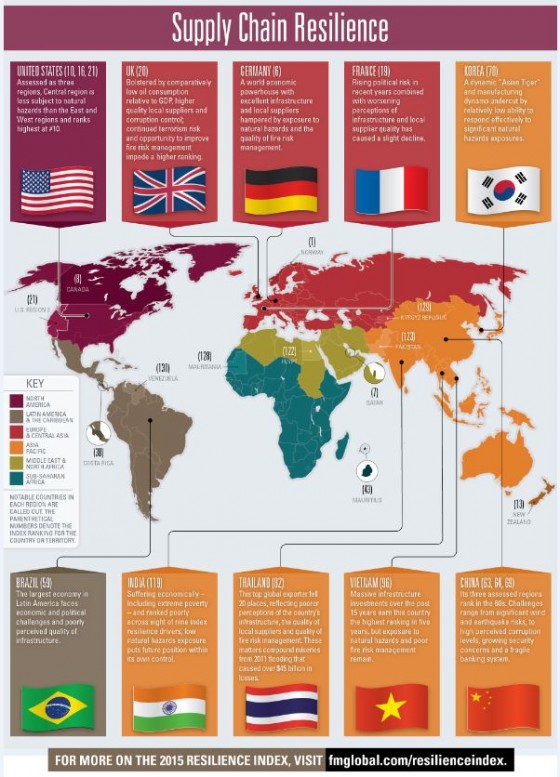
As we brace for another season of tornadoes, hurricanes, forest fires, earthquakes and floods, all businesses should be asking, “Is our data protected should disaster strike?” Or more simply, “What happens if we lose our data?”
Sadly, despite the fact that significant portions of the country are at risk for severe weather and other natural disasters, not all businesses are thinking pragmatically about catastrophic data loss and downtime, which can lead to staggering financial losses and impact productivity, reputation, regulatory compliance, and ultimately the bottom line.
According to a global data protection study released in December, enterprises are losing as much as .
7 trillion annually through data loss and unplanned downtime. Data loss is up 400% since 2012, and two-thirds of the 3,300 organizations surveyed had experienced data loss in the last 12 months. Researchers found that although a high percentage of organizations had disaster recovery plans in place, surprisingly few had implemented data protection practices and fewer than half employed remote, cloud-based data protection. Seventy-one percent of organizations were not fully confident in their ability to recover after a disruption.
If your business is unprepared for a disaster, then act now to improve your resilience and mitigate risk. Plan for natural catastrophes and man-made disasters alike (such as theft, hardware failure, human error, system failure, computer viruses, power failure and accidental deletion).
Disaster preparedness begins with a business continuity plan. This serves as your playbook for staying in business following a disaster and it enables you to restore operations and communications systematically while helping minimize risk. Ask your IT department to incorporate the steps needed to safeguard your IT infrastructure from disaster, including backup and recovery measures. In today’s highly-regulated environment, having a secure backup and recovery solution that meets the stringent requirements defined by Sarbanes-Oxley, Gramm-Leach-Bliley, HIPAA, FISMA, PCI, ISO and other regulatory standards is expected.
During this process, develop a clear understanding of where the cloud fits in and how it can help save time, money and resources.
Businesses are increasingly backing up their data and apps in a secure, off-site cloud environment (not in the physical office), because the cloud is faster than other options and typically offers the most protection at the lowest cost.
Recovery in the cloud requires no travel and no extra hardware, and it offers extreme levels of reliability.
Should disaster occur, a cloud solution allows the continuously backed up systems to be restored as virtual machines. All of the cloud’s benefits speak to why highly regulated businesses protecting sensitive data are finding that virtualization technologies make it simpler to comply with stringent security and compliance regulations governing electronic storage and access to data.
Here are seven steps to help businesses plan for data loss and downtime:
- Identify the risks. List and categorize all natural and man-made threats and their impact on various systems. Ask what would it take to knock out our entire network and how much unplanned downtime can our business sustain?
- Inventory IT assets. Which are most critical to maintaining business continuity? What’s our tolerance for loss of those assets? The cost of the response should be balanced against your tolerance for system downtime.
- Define goals. In a worst case scenario, how long can our business shut down? Does it need to recover off-site? Define goals in terms of RPO (Recovery Point Objective, “How much data can we lose?”) and RTO (Recovery Time Objective, “How long can we be down?”).
- Develop a plan. Include “IT Assets Inventory,” data protection procedures and contingency plans, notification/activation schedules, a list of roles and responsibilities, a list of resource requirements, and details about training provisions. Good plans include maintenance and backup/recovery testing schedules.
- Understand the cloud’s benefits. Virtualization technologies make backup and disaster recovery vastly faster, cheaper and easier. The combination of the cloud and the right backup and disaster recovery solution allows for continuous data protection (so the backups always run 24/7/365) as well as consistent compliance and security.
- Implement the plan. If executives understand clearly the consequences of system disruptions, you will win their support and funding for contingency policies.
- Test the plan. Continuous testing and plan updating helps ensure business survival.
 NEW ORLEANS—One of the most promising new technologies to hit the wider market in recent years, 3D printing is poised to revolutionize manufacturing as we know it. Otherwise known as additive manufacturing, 3D printing allows users to print almost anything they can dream up, including toys, machine parts, clothing, food, and prosthetic (as well as actual) body parts. There even companies that can print a lifesize, 3D model of your unborn fetus using ultrasound scans.
NEW ORLEANS—One of the most promising new technologies to hit the wider market in recent years, 3D printing is poised to revolutionize manufacturing as we know it. Otherwise known as additive manufacturing, 3D printing allows users to print almost anything they can dream up, including toys, machine parts, clothing, food, and prosthetic (as well as actual) body parts. There even companies that can print a lifesize, 3D model of your unborn fetus using ultrasound scans.