The following article is part of a new blog series that will explore ideas, concepts, discussions, arguments and applications associated with the field of enterprise and strategic risk management.
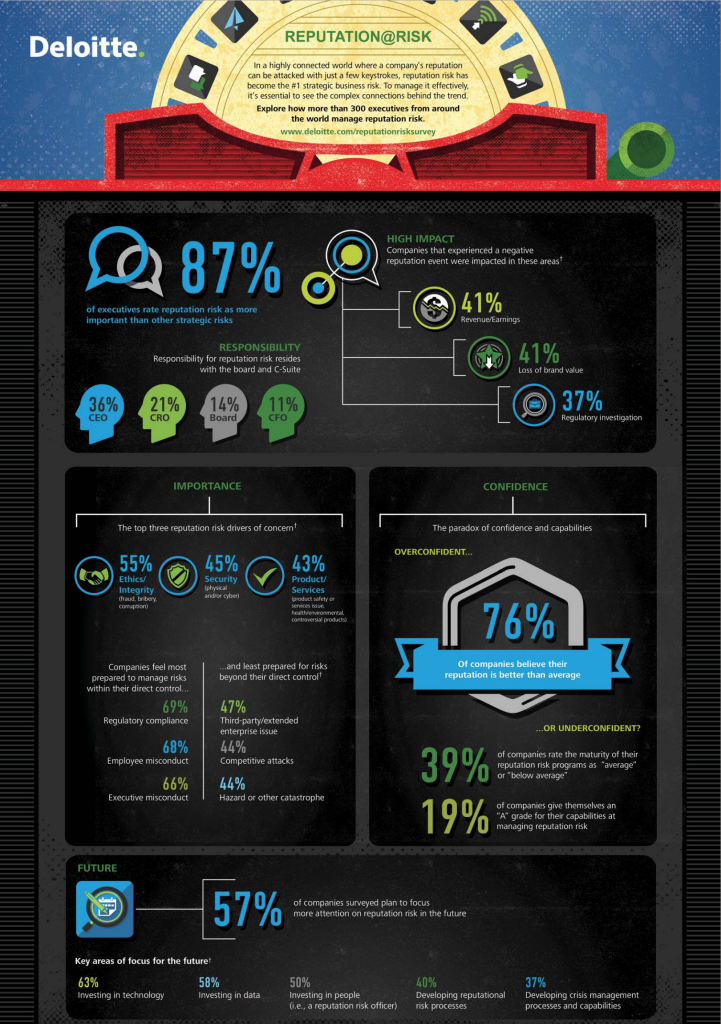
One of the more striking conclusions contained in Aon’s 2015 Global Risk Management Survey is that damage to reputation and/or brand was considered by the survey cohort to be the most significant risk to the enterprise. The survey was conducted in Q4 of 2014 and received input from over 1,400 respondents coming from both the private and public business on a worldwide basis.
The “Top Ten” most identified risks included:
- Damage to reputation/brand
- Economic slowdown/slow recovery
- Regulatory/legislative changes
- Increasing competition
- Failure to act or retain top talent
- Failure to innovate/meet customer needs
- Business interruption
- Third-party liability
- Computer crime/hacking/viruses/malicious codes
- Property damage.
The survey results should not come as any real surprise given the number of sensational news stories coming from around the world that highlight potential or real reputational or brand problems. We have witnessed data breaches ranging from credit card identity theft in consumer retail, to serious product recall notifications in the food and beverage industry, to product performance/ warranty failures in the automotive arena, as well as “hints of reputational quality,” defined as “trust” in the early stage politics of the presidential selection process involving private vs. public use of email servers. There is little doubt that news, sensational or not, impacting reputational or brand, will continue for some to come. The real question is: Should anyone care?
Defining reputational/brand risk is hard to accomplish:
Based on some additional research done by my colleague Sylvesto Lorello, reputational risk is not a new concept, but it arguably has no established or universally agreed upon definition. Academic and business thinking about this subject continues to evolve. Within the insurance underwriting community that I have been in touch with, reputational or brand risk is being compared in scope to contingent liability risks, but with a serious caveat: the basis of the risk is highly variable and the duration of the risk event/loss event is difficult to pin down economically.
The concept of reputation and brand for example, are notably absent from the 2004 framework for enterprise risk management proposed by the Committee of Sponsoring Organizations of the Treadway Commission (COSO). It is also overlooked in the Basel II international accord for regulating bank capital, which was also issued in 2004.
A lack of common standards or definitions of reputational risk mean that companies perceive it in different ways.
Some risk practioners are beginning to view reputation as a “risk of risks” similar to the dialogue surrounding the “internet of things/objects.” Interestingly, an emerging dialogue is developing around whether reputation or brand is actually a risk or a residual event stemming from other extenuating risk domains or actions.
The ISO 31000 (2009)/ISO Guide 73:2002 definition of risk is the “effect of uncertainty on objectives.” In this definition, uncertainties include events (which may or may not happen) and uncertainties caused by ambiguity or a lack of information.
The U.S. Federal Reserve in 1995 defined reputational risk as “…the potential that negative publicity regarding an institution’s business practices, whether true or not, will cause a decline in the customer base, costly litigation or revenue reductions.
In this case, the definition points to the potential for hard data from which basis and duration can be calculated.
Definitional issues aside, eventually societies will develop benchmarks with which to measure reputational or brand acceptability. One way of thinking about this approach is shown in the following exhibit.
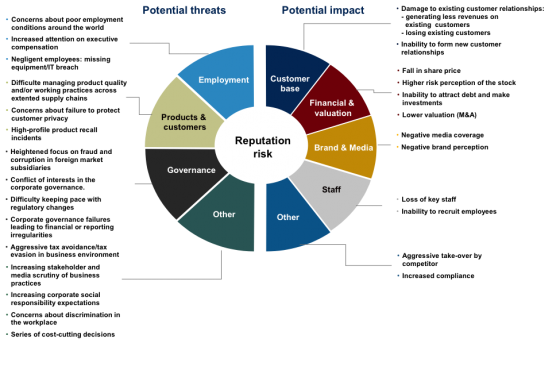 Here we ignore some of the more difficult definitional discussion around a combined reputation/brand perspective, and limit our view to reputation alone.
Here we ignore some of the more difficult definitional discussion around a combined reputation/brand perspective, and limit our view to reputation alone.
From a practical early stage standpoint, an entities reputation could be view from potential threat and potential impact perspective. On the threat side, it may be possible to segregate threats into four categories:
- Risk to reputation stemming from employment activities;
- Risk to reputation coming from product or customer issues;
- Risk to reputation derived from governance; and,
- Other less easily classified risks to reputation.
These categories appear for graphical purposes as if they are mutually exclusive, but in reality, there are good examples of causal overlap that increased risk volatility and severity. Recent oil spills and automobile product failure/recalls are enduring situations where more than one causal category created a economically catastrophic reputational problem.
On the other side of the graphic we outline the potential impacts to reputation coming from the threat categories. Again, while not mutually exclusive or exhaustive, the impact areas include:
- Customer base
- Financial valuation
- Brand and media
- Staf
- Other less easily defined impacts.
Coming next, who are the stakeholders and how might one approach measuring reputational risk.