Jan. 28 marks the annual Data Privacy Day (DPD), which was adopted in North America to bring together businesses and private citizens in an effort to share strategies for protecting consumers’ private information. Richard Purcell, DPD advisory board member and CEO of the Corporate Privacy Group spoke to Risk Management Monitor about the current state of privacy.
member and CEO of the Corporate Privacy Group spoke to Risk Management Monitor about the current state of privacy.
Risk Management Monitor: How do you view privacy?
Richard Purcell: The concept of privacy is really complex and layered. I like to think of it as being grounded by two basic behaviors—respect and discretion.
The idea of privacy is not the same as secrecy. Secrets are not shared and are kept hidden as unknown ideas or thoughts, whereas privacy is the act of sharing information, trusting that the recipient will not share it any further.
RMM: How has technology redefined privacy?
RP: Over the last several years, we’ve heard from individuals who believe that their privacy has been assailed. Upon examination, we might find some reasons that are relevant to our emerging technology use:
There are many instances in which people have lacked respect for their own information, sharing personal information with others and commercial interests without restraint. A simple review of Twitter, Facebook, Instagram, Flicker, Tumblr and other social media sites confirms this. Just as often, commercial players have shown a lack of respect for the personal information entrusted to them by individuals. Examples include banks that have used customer information to open accounts without providing notice or asking for consent. This is a distinct showing of disrespect for the information.
Information has become the basis for commercial activity, so using and sharing personal information is quickly becoming how companies make money—Facebook is a social media site, but makes more than 90% of its revenues by selling users’ data to advertisers—credit bureaus make their money solely be collecting financial info, not from people, but from other companies, in order to calculate risk and sell reports (for example, credit reporting has a long history regarding privacy thru FICRA, FACTA, and OECD FIPs.).
RMM: In 2000 you were named Microsoft’s first corporate privacy officer. How has the privacy landscape changed since then?
RP: Privacy and data protection are beginning to be better and more closely integrated into security practices. It’s taken a long time to get them better integrated.
Security practices have strong levels of discipline without much of a human factor. Privacy practices have strong moral bases, which security is getting more in tune with, so they are sharing their traits in ways that are helpful.
We are not there yet, though, because security is a binary condition. You either have the security practices or you don’t. Privacy is harder to define because practices are more behaviorally based. We still find privacy issues are driven by human failings, errors or miscalculations as opposed to technologies.
Privacy professionals have gained more of a voice and authority over time in their organizations. They are not just advisers anymore, saying ‘Watch out for this,’ or ‘We can’t do that.’ They have become people with decision-making authority, which is only increasing. The position analyzes conditions and bases those recommendations on risk profiles and the challenges they present. Companies are then free to choose whether they take the risk or mitigate it.
RMM: What developments will impact your work in 2018?
RP: Regulatory changes matter a lot and apply to industrial sectors in the United States. External regulations are much more broadly applicable.
EU GDPR. Any company doing business in the EU has to adjust its governance program to comply with the GDPR by late May 2018. That means taking a broader definition of personal data; documenting its data processing activities; strengthening its user consent provisions; developing support for data erasure, portability and rectification; enhancing oversight and data breach responsiveness; and generally paying more attention to data protection.
EU ePrivacy. Broadband providers in the U.S. may celebrate the FCC dropping of the net neutrality/privacy rules, but they still have to deal with the EU ePrivacy Directive.
Australia, Korea, Japan and even China are strengthening their data protection programs. China announced its displeasure with the practices of Ant Financial (an Alibaba affiliate), Baidu (search organization) and Jinri Toutiao (newsfeed organization) for lacking adequate policies and practices in collecting, using and sharing personal information. You know something important is happening when China begins enforcing stronger privacy regulations.

 A quick look at recent headlines shows how quickly a cybersecurity incident can damage a corporate brand. Many companies that have recently experienced data breaches also have been exposed by the media because of ineffective or nonexistent integrated risk management strategies. This can be for a variety of reasons, from executives trying to hide the breach to the belief that they can resolve the issue before it grows into something larger or, possibly the worst of the options, they are not aware that the breach is even occurring.
A quick look at recent headlines shows how quickly a cybersecurity incident can damage a corporate brand. Many companies that have recently experienced data breaches also have been exposed by the media because of ineffective or nonexistent integrated risk management strategies. This can be for a variety of reasons, from executives trying to hide the breach to the belief that they can resolve the issue before it grows into something larger or, possibly the worst of the options, they are not aware that the breach is even occurring.
 On Jan. 25, LinkedIn will live-stream an event from its San Francisco office exploring the theme of “Respecting Privacy, Safeguarding Data and Enabling Trust.” The broadcast will feature TED-style talks and panel discussions with experts focusing on the pressing issues that affect businesses and consumers.
On Jan. 25, LinkedIn will live-stream an event from its San Francisco office exploring the theme of “Respecting Privacy, Safeguarding Data and Enabling Trust.” The broadcast will feature TED-style talks and panel discussions with experts focusing on the pressing issues that affect businesses and consumers. 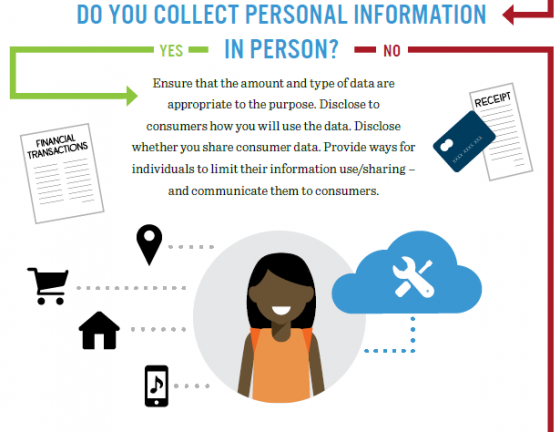 The relevance does not end on Jan. 29, noted Richard Purcell, DPD advisory board member and chief executive officer of Corporate Privacy Group. He has witnessed the event’s evolution and its impact on risk management and privacy professionals.
The relevance does not end on Jan. 29, noted Richard Purcell, DPD advisory board member and chief executive officer of Corporate Privacy Group. He has witnessed the event’s evolution and its impact on risk management and privacy professionals.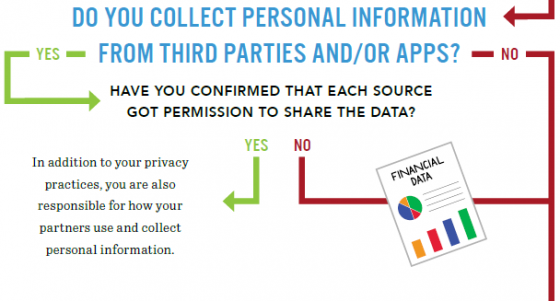 Newly released information from NCSA demonstrates how privacy is impacted in both personal and professional environments—from healthcare and retail to social media, home devices and parenting. Some statistics include:
Newly released information from NCSA demonstrates how privacy is impacted in both personal and professional environments—from healthcare and retail to social media, home devices and parenting. Some statistics include:
 Enterprise risk management (ERM) has emerged as a best practice in gaining an overview of strategic, financial and operational threats, and in determining how to mitigate and manage those risks.
Enterprise risk management (ERM) has emerged as a best practice in gaining an overview of strategic, financial and operational threats, and in determining how to mitigate and manage those risks.