 The National Cyber Security Alliance (NCSA) announced that its new executive director is Kelvin Coleman, who has held high-level positions in the United States Department of Homeland Security, and the National Security Council.
The National Cyber Security Alliance (NCSA) announced that its new executive director is Kelvin Coleman, who has held high-level positions in the United States Department of Homeland Security, and the National Security Council.
Coleman’s appointment puts him in charge of the country’s leading cybersecurity and privacy protection education and awareness organization, responsible for leading organizational growth; facilitating strategic partnerships and alliances with government, industry and non-profits; and acting as NCSA’s primary spokesperson.
He discussed with Risk Management Monitor the types of cyberrisks he follows, preventative measures and upcoming NCSA events and services.
What are the biggest cyberrisks facing businesses today? How do you plan to advise or collaborate with business leaders to combat them?
Some of the biggest cyberrisks facing businesses today include email threats, employee activity and vendor security. When it comes down to addressing cyberrisks targeting businesses of varying sizes, everyone needs to start with the basics. It is imperative to get leadership on board with recognizing that cyber resilience is more than just taking technology-focused measures, but also modifying processes and behaviors at all levels in the organization.
What are the attacks that are easiest or most difficult to prevent?
The answer to both is phishing. Attacks come in through three different ways – people, products, and processes. A great product can hold attackers at bay. Similarly, great processes can mitigate a threat. Human beings are the wild cards. People are both the easiest to control and the most difficult, especially when it comes to phishing attacks. One of the NCSA’s tips is “when in doubt, throw it out.” We try to make sure folks understand that if they are not familiar with a link or a website, they need to delete it or ignore it.
At NCSA, our focus is on the human side of cyberattacks, and we work to get people to change their behaviors as well as understand the processes for keeping their devices and online accounts safe, particularly as phishing attacks become more sophisticated.
Speaking of the human side, which professionals are most exposed to cyberrisk?
All of them. Cybersecurity needs to be embedded into the company culture from the most entry-level positions to the most senior, because hackers can access information at any level. We’re all vulnerable, from the break room to the boardroom. We often tell small business owners that they must also train their employees to recognize malicious links and emails, as employees can often be the weakest link when it comes to cybersecurity at the office.
What is your reaction when you learn that the information of 500 million Marriott guests may have been exposed?
Marriott is a great example of a company doing as much as it can to prevent an attack but still being targeted. They were not laissez-faire about their security. So, I see it as a warning for everyone to remain extremely vigilant in the face of increasing numbers of cyber attacks. If it happens to Marriott, we’re all vulnerable to an attack of this nature.
Small businesses seem just as susceptible to cyberrisk as large ones. How would you advise small businesses to protect themselves?
Small businesses are more at risk and they often have information, such as customer data, that’s just as valuable to hackers as that of the customer data from large corporations. Small businesses often don’t have the resources to invest in a prevention plan, nor do they have the capital or leadership or knowledge about cybersecurity. This is why they’re often targets for hackers.
Our advice for small businesses doesn’t vary much from what we advise to all people: Keep a clean machine by keeping software updated, use stronger authentication and passwords, recognize and avoid phishing links, etc. If [a small business] decides to hire a third-party vendor for cybersecurity, we advise them to do their research and hire a reputable vendor. We also encourage them to attend our regional CyberSecure My Business events in their local community, or take part in a CyberSecure My Business webinar.
What new initiatives or campaigns will you be overseeing for in 2019?
In 2019, our overarching goal is to empower individuals and – at the same time– focus on educating businesses to respect privacy, safeguard data and enable trust. This means that consumers need to know how organizations collect and use personal information and companies of all sizes need to be transparent and communicate in an accurate and consumer-friendly language to their customer base.
We will share key messaging and provide actionable tips to help protect privacy. NCSA and our highly engaged partners will host numerous events that will shine a spotlight on the rapidly changing technology landscape and forging ahead toward the future of privacy. We plan to engage industry leaders with diverse perspectives to address opportunities and challenges. In addition, we will soon be launching our Champions program which is a way for both individuals and businesses to officially show support. We expect to launch the Champions portal – along with additional Data Privacy Day information – in mid-December 2018.
What changes or improvements are in store for National Cyber Security Awareness Month (NCSAM)?
I don’t believe NCSAM needs a shiny new toy each year. Our plan is to engage a much larger audience. NCSAM continues to reach more and more people every year, but there are still significant numbers of Americans who need to hear our message – not just during October but throughout the year. We want to connect these folks more with our proven tips for staying safe and secure online. Our goal at NCSA is reinforcing our cybersecurity best practices among a broader audience to better impact online behavior.
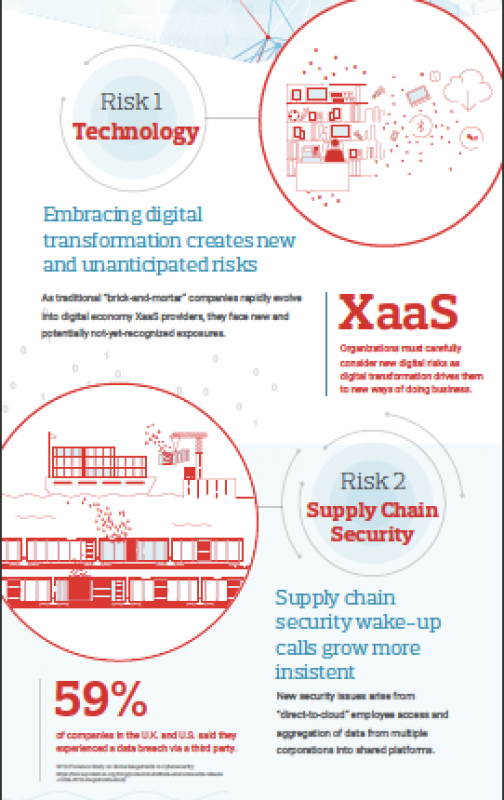
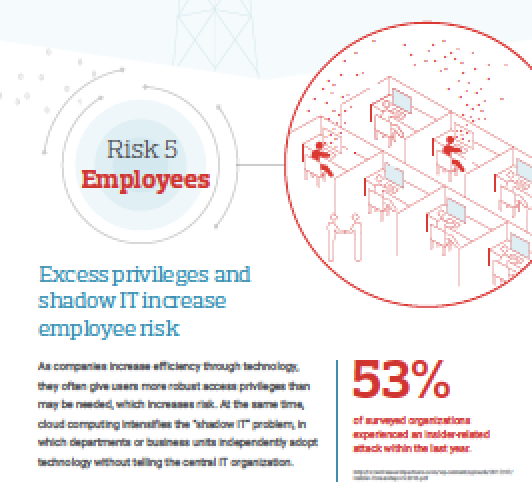


 The National Cyber Security Alliance (NCSA) announced that its new executive director is Kelvin Coleman, who has held high-level positions in the United States Department of Homeland Security, and the National Security Council.
The National Cyber Security Alliance (NCSA) announced that its new executive director is Kelvin Coleman, who has held high-level positions in the United States Department of Homeland Security, and the National Security Council.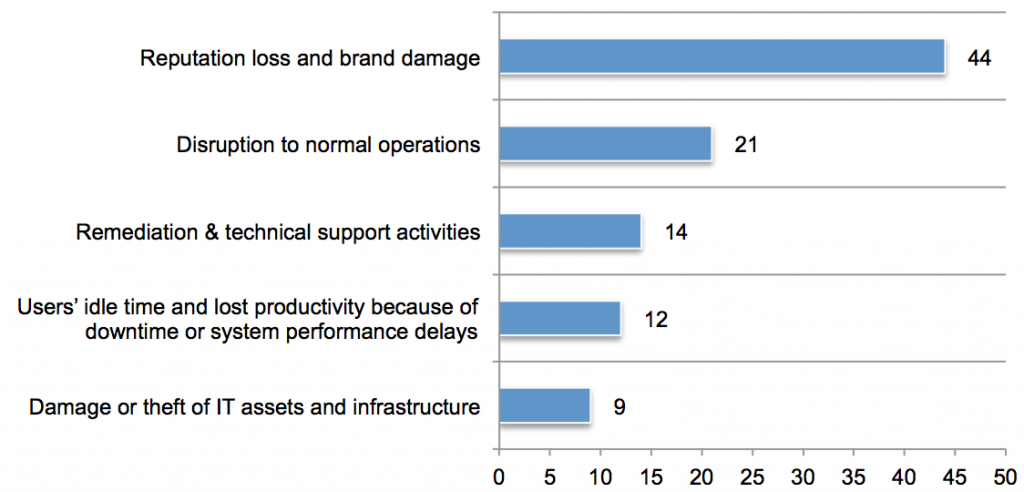
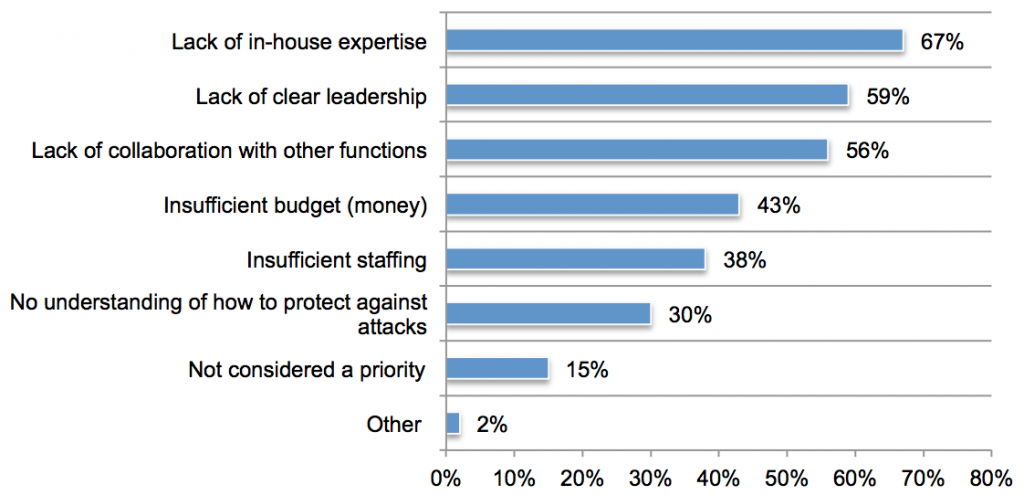
 file a new invention—not the first to invent it—gets the rights to the patent. If one of your inventors has a patentable idea and you don’t find out about it, you risk having a competitor file ahead of you.
file a new invention—not the first to invent it—gets the rights to the patent. If one of your inventors has a patentable idea and you don’t find out about it, you risk having a competitor file ahead of you.