 National Critical Infrastructure Security and Resilience Month (CISRM) kicked off on Nov. 1. The month’s initiatives address risks such as extreme weather, aging infrastructure, cyber threats and acts of terrorism.
National Critical Infrastructure Security and Resilience Month (CISRM) kicked off on Nov. 1. The month’s initiatives address risks such as extreme weather, aging infrastructure, cyber threats and acts of terrorism.
Its timing is certainly appropriate, as the effects of recent hurricanes on infrastructures in southern states and Puerto Rico continue to be assessed, as well as Northern California’s devastating wildfires and the deadliest shooting massacre in modern U. S. history.
The month was created by the Obama administration and the Department of Homeland Security (DHS) hosts CISRM in an effort to promote education and awareness of the 16 critical infrastructure sectors that are vital to public safety and national security. Its page reads:
The evolving nature of the threat to critical infrastructure—as well as the maturation of our work and partnership with the private sector—has necessitated a shift from a focus on asset protection to an overarching system that builds resilience from all threats and hazards.
A CISRM toolkit provides companies with templates and drafts of newsletter articles, blogs, and other collateral material for use in outreach efforts. Activities geared toward business owners, public entities and private citizens focus on several key themes to enhance security and resilience, including:
- Highlighting interdependencies between cyber and physical infrastructure
- Pointing small and medium-sized businesses to the free tools and resources available to them to increase their security and resilience through Hometown Security and the four steps of “Connect, Plan, Train, and Report”
- Promoting public-private partnerships
- Fostering innovation and investments in infrastructure resilience
In his proclamation of CISRM earlier this week, President Trump further committed to helping businesses invest in “needed capital and research and development by reducing burdensome regulations and enacting comprehensive tax reform.” The proclamation states:
We will also renew our Nation’s focus on ensuring that the next generation has the education and training, particularly in science, technology, engineering, and math, required to meet the known and unknown threats of the future.
Overall the United States’ infrastructure is among the top 18 in the world, according to the 2017 FM Global Resilience Index, which aggregates data to help companies identify their key supply chain risks. The U.S. continued to hold high rankings among 130 countries based on drivers in three categories: economic, risk quality and supply chain factors. The U.S. is segmented into three regions to reflect disparate natural hazards exposure:
- Region 1, encompasses much of the East Coast, is ranked #10 in the index (a one-spot upgrade from last year)
- Region 2, primarily the Western U.S., is ranked #18 (a three-spot upgrade)
- Region 3, which includes most of the central portion of the country, is ranked #9 (down three places)
Although the federal government is less focused on asset protection, business owners can still get involved by safeguarding workplaces. In its October 2017 edition, CLM magazine noted that another path toward resilience involves reducing property damage caused by extreme weather and natural disasters. Literally looking to the sky is one suggestion; business and property owners should pay particular attention to their roofs in order to prevent degradation and enable them to withstand high winds.
“Property owners need to have maintenance personnel adopt and implement preventative maintenance and roof inspection programs that alert them to potential and active degradation,” wrote the authors of the article, “Time For Resilience.
” “Weak links such as roof detachment, corrosion, or other damage could tear off roofing during an enhanced wind event. Such risks need to be mitigated before an event occurs.”
Ready.gov provides resources on disaster planning and management, and also has this section on Business Continuity.

 urity industry, noting that, “the defense trails the offense by about five years.” Comparing the newest waves of protection software to a strong rookie pitcher, he said, “A new pitcher may come along and strike everybody out as he goes through the league a few times. But eventually he gets figured out and [hackers] figure it out,” he said. “It needs at least a year of being attacked for real,” to find the gaps in efficiency, and leads to the “the kind of experimentation that will yield better results.”
urity industry, noting that, “the defense trails the offense by about five years.” Comparing the newest waves of protection software to a strong rookie pitcher, he said, “A new pitcher may come along and strike everybody out as he goes through the league a few times. But eventually he gets figured out and [hackers] figure it out,” he said. “It needs at least a year of being attacked for real,” to find the gaps in efficiency, and leads to the “the kind of experimentation that will yield better results.”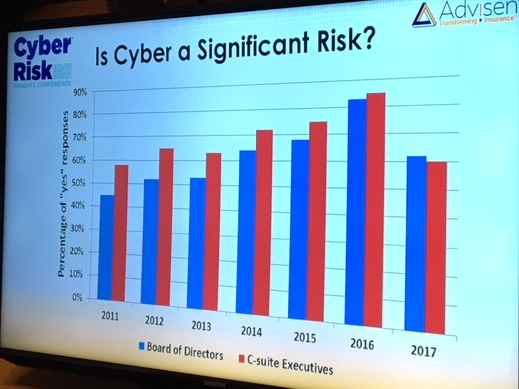 Advisen
Advisen 