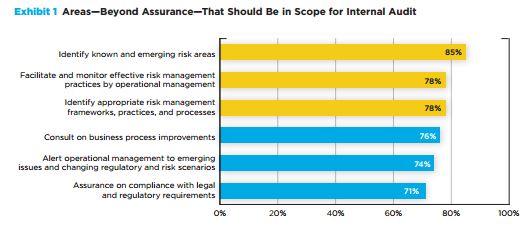
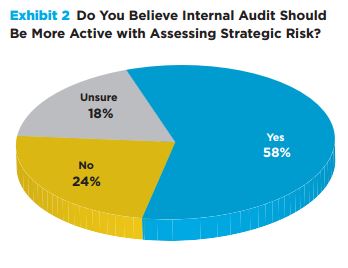
In recent years, more and more cybersecurity incidents have taken place as a result of insecure third-party vendors, business associates and contractors. For example, the repercussions of the notorious Target breach from a vulnerable HVAC vendor continue to plague the company today. With sensitive data, trade secrets and intellectual property at risk, hackers can easily leverage a third party’s direct access into a company’s network to break in.
While such incidents may cause significant financial and reputational harm to the first-party business, there is hope.
Regulators are instating a growing number of legal requirements that an organization must meet with respect to third-party vendor risk management. As liability and regulations take shape, it is important to assess whether your company currently employs a vendor risk management policy, and, if not, understand how a lack of due diligence poses significant risk on your organization’s overall cybersecurity preparedness.
management. As liability and regulations take shape, it is important to assess whether your company currently employs a vendor risk management policy, and, if not, understand how a lack of due diligence poses significant risk on your organization’s overall cybersecurity preparedness.
A vendor management policy is put in place so an organization can tier its vendors based on risk. A policy like this identifies which vendors put the organization most at risk and then expresses which controls the company will implement to lessen this risk. These controls might include rewriting all contracts to ensure vendors meet a certain level of security or implementing an annual inspection.
All this probably sounds pretty good, but you may still be wondering why you really need a vendor management policy—and why it’s urgent.
Here are four explanations to give you a better idea:
- Legal Liability
There are a growing number of legal requirements in a variety of sectors—from finance, to retail, to health care, to energy—on how companies should manage their third-party risk. Regulators have recognized that data breaches through third parties can present significant and sometimes catastrophic consequences to an organization. To deal with this risk, they have created various legal requirements in an effort to have organizations manage their third-party cyber risks more carefully. If you are in a regulated industry and do not currently have a vendor management policy, you could be out of compliance (and in a lot of trouble).
- Well-Known Risks
An organization should be concerned about third parties that have either access to their most sensitive data or direct access into their corporate network. So if you work with a lot of third parties, you are naturally creating more targets that hackers and criminals can exploit. This is becoming more common, as organizations are outsourcing to vendors more frequently in an effort to either save costs or capitalize on vendor expertise. While that is all well and good, the more vendors you have, the larger risk landscape you create. This is a well-known risk—but all too many companies don’t give it enough thought.
- Unknown Risks
Not all risks are easily understandable. Many organizations today have entered into business relationships with third parties, not fully understanding the risk to their data. What’s more, the first party may not have set requirements for how their vendors should secure their data.
A number of organizations struggle to even know who has access to their sensitive data, how much access they have, where it resides, and more. These unknowns give plenty of companies a valid reason for concern.
- Significant Consequences
To see how very real the consequences of not managing vendor policy are, simply read some of the latest cybersecurity headlines. An example that demonstrates the significant impact of a third-party breach is the recent Experian breach, which exposed the personally identifiable information of over 15 million consumers. In this case, Experian was holding loads of sensitive T-Mobile customer data, which hackers were able to access. The T-Mobile CEO John Legere expressed how furious he was at Experian for being the source of this compromise. Nothing has been stated yet, but we’re certain that this business partnership will be reevaluated after this experience.
The truth is that if you don’t have a vendor management policy in place today, your company is falling behind the times. Unfortunately, not having such a policy in place also means there is a good chance that your organization’s sensitive data is being handled by someone who shouldn’t have access to it. This puts the health of your entire company on the line.