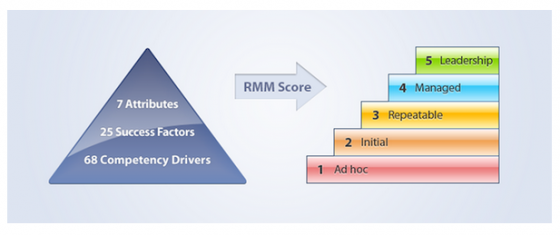
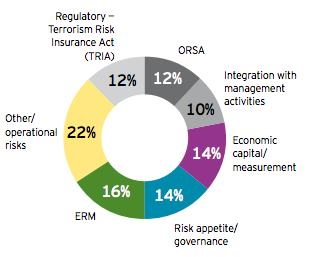
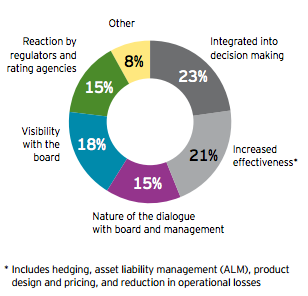
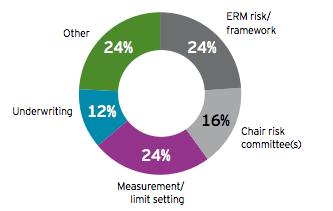
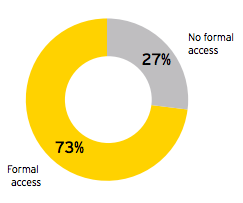
Last week, we introduced the latest findings from studies of the RIMS Risk Maturity Model. In an effort to explain the model and results of the study more fully, it’s beneficial to break the RMM into each of its attributes. Here we’ll examine the first two attributes of an effective ERM program, ERM Based Approach and ERM Process Management.
ERM Based Approach
The emphasis of this attribute is to move organizations from an old, obsolete style of governance to a more holistic, integrated approach. Old-style governance is focused on regulatory compliance and silo specific risk management. The problem with this approach is it leaves the organization exposed to risk that isn’t governed by regulatory mandates, as well as cross functional risk that may be systemic to the company.
We see examples of failures in this approach all the time. West Virginia’s water contamination crisis, for example, was caused by a series of risks with inadequate controls—the chemical tank was not adequately surveyed, the employees were not directed to immediately report the leak, even the water filtration organization wrongly estimated that it could filter the chemicals out. None of these entities were at fault from a regulatory perspective, but they were still on the hook for millions in remediation (the chemical plant filed for Chapter 11 bankruptcy in January).
An ERM approach moves organizations past regulatory concerns, which are only a subset of the overall risk universe. This requires a number of activities that the Risk Maturity Model identifies as drivers of ERM Maturity—tone from the top, assimilation into front line activities, risk ownership—which when combined result in a more risk-aware enterprise.
RIMS Risk Maturity Model: ERM Process Management
With a new governance mindset in place, organizations can move to applying a risk-based process framework of Identify, Assess, Evaluate, Mitigate and Monitor within each business process.
The RMM assesses the degree to which these activities are pervasive inside business processes. Many executives misinterpret these processes as unique to ERM, when in fact the steps are iterative, constantly reoccurring within organizations but without any defined process or standardizations.
The key to ERM process management is to create a common language and structure so areas can better transfer knowledge to each other where beneficial. This is done by integrating these framework steps into the business in a way that provides accountability, repeatability, and adequate reporting. A great example is the Vendor Management Governance function. Vendor management is frequently tasked with identifying critical vendors, assessing their risk (such as “due diligence”) and then managing through mitigation (contracts, insurance certificates) and monitoring (shipping times, order completion).
The problem is that vendor management, like other functions, is operating independently with too little information exchanged between vendor management and other governance functions.
Why is this important?
Strategic imperatives are by nature cross-functional, but are rarely linked to processes and activities on the front line. When not linked, risks to corporate objectives are either not addressed or treated differently by the business processes. This alignment is a critical driver of ERM maturity. Organizations that can effectively communicate goals—not just at the corporate level, but down to the front lines—are better equipped to achieve results and elevate concerns.
Interested in seeing how this approach differs from traditional governance? Watch our short video on Strategic Risk Management.