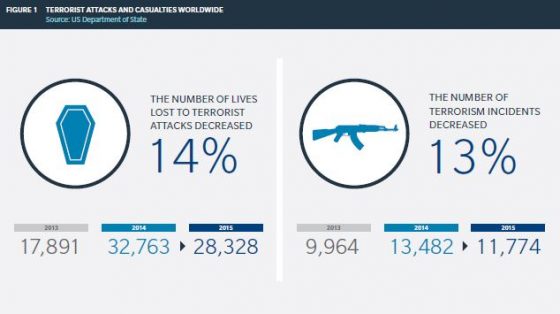
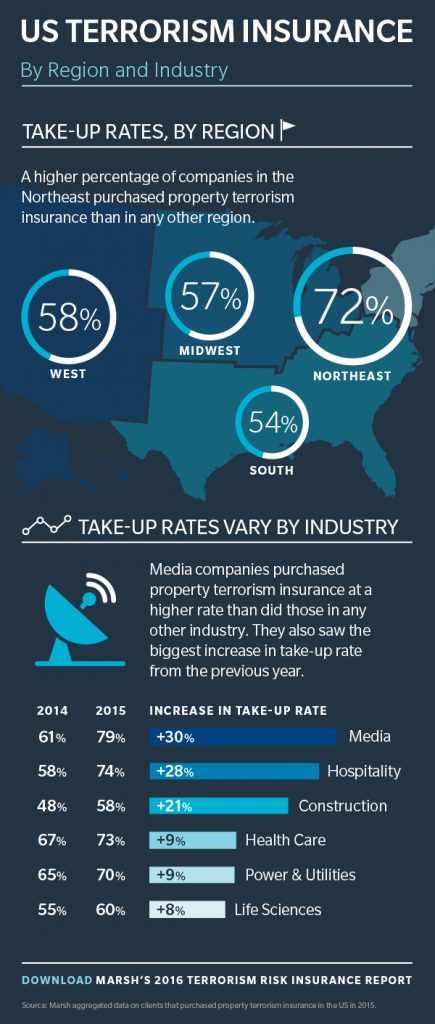
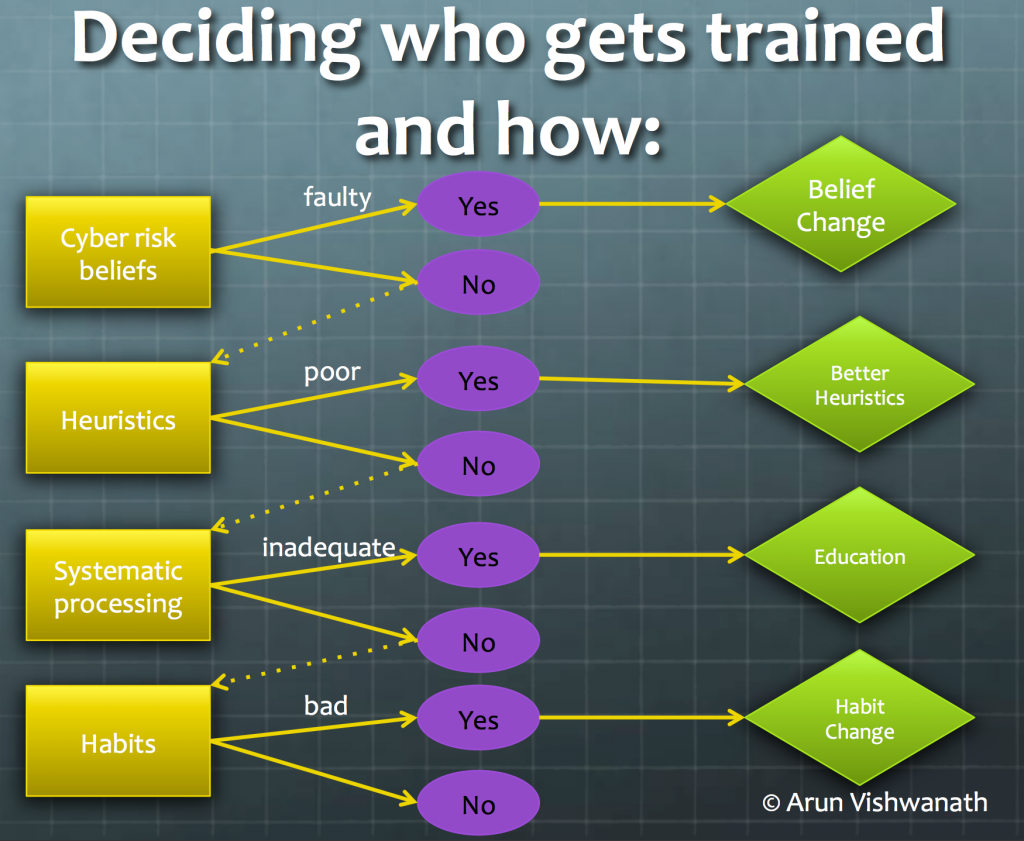
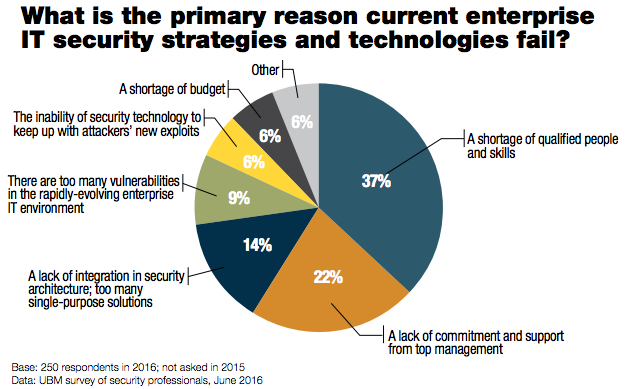
The commercial use of drones, or unmanned aircraft systems (UAS), has been widely discussed in the insurance industry. There is much to speculate upon as the technology is still emerging, with any number of possible applications and concerning reports of injuries. While drones bring the promise of efficiency, there is also the uncertain risk profile that comes with this most exciting technology.
With new Federal Aviation Administration (FAA) rules ready to take off (pun intended) in August, there will be improved visibility into the procedures and practices used by drone operators. The FAA recently finalized the first operational rules for routine commercial use of drones and, while the total risk picture is still unknown, we can now evaluate the strength and appropriateness of safety controls employed by UAS operators.
Drones are being used in many industries, from construction to utilities to agriculture, and these industries will need to prioritize compliance and risk mitigation. Some of the new operational limitations from the FAA include:
- At all times the drone must remain close enough to its remote pilot in command and the person manipulating the flight controls must be capable of seeing the aircraft with vision unaided by any device other than corrective lenses.
- Drones may not operate over any person not directly participating in the operation, or under a covered structure, or inside a covered stationary vehicle.
- Drones may only operate during daylight hours or 30 minutes before sunrise or 30 minutes after sunset with appropriate anti-collision lighting.
- Drones cannot operate from a moving vehicle unless it is over a sparsely populated area.
These rules appear to provide sound guidelines, but most regulations are only as good as the ability for them to be enforced. For example, under the rules’ operational limitations section, it is stated that most of the new restrictions are waivable if the applicant demonstrates that his or her operation can be safely conducted under the terms of a certificate of waiver. How often will these waivers be allowed and how will the FAA conduct investigations? Insurers will be watching to see how the rules are implemented and enforced.
Clearly, we should take note of this important moment for drones, as implementation of federal safety standards for emerging risk drivers has spawned or grown new insurance business lines that are now viewed as essential coverages. For example, environmental regulation in the late 1970’s and 80’s created the need for environmental coverage.
State and more recent federal cyber laws are the backbone of cyber policies as insureds must comply with standards to prepare for and respond to breaches. Most recently, the FDA’s Food Safety Modernization Act is driving insureds to take a fresh look at product recall insurance.
Risk managers should expect operating rules to drive new coverages that support the insured’s risk evaluation process.
This will allow for a spectrum of outcomes from exclusionary wording for UAS operations to distinct coverage grants for safe and compliant operators. Loss control and consulting services from insurers could be helpful to guide the risk management surrounding drones. The federal rules also enable additional objective underwriting questions tied to compliance. Expect to see these questions incorporated into specific UAS underwriting application questions.
The risk manager can readily imagine the Coverage A risks that can arise from UAS operations. Those could include but are not limited to third party bodily injury resulting from aircraft failure, a wildfire resulting from a crash and potential catastrophic terrorism uses. Privacy risk under Coverage B is also a risk easy to imagine and well-documented even in the early stages of this new commercial risk driver.
Insurance brokers or consultants can also offer guidance on the various ISO endorsements in circulation seeking to clarify the commercial general liability aircraft exclusions to include unmanned aircraft. ISO endorsements provide options to include Coverage A and/or schedule-specific aircraft for coverage. I do not believe that ISO has plans to amend the currently available endorsement in response to the aforementioned FAA operating rules.
There is no question the use of drones is only going to expand in its application and, with that, operational safety will improve as exposures grow. The industry should expect increased regulations, including flight worthiness certification as well as possible insurance requirements. According to a Goldman Sachs analysis, total global spending on drones in the commercial market is estimated to be around 0 billion over the next five years.
Of that, about $11.2 billion will be generated by the construction industry.
Risk managers should anticipate liability exposure for those that fail to comply with the new regulations. The uses are vast, and given the diversity of users the levels of knowledge and awareness of compliance obligations will vary. Education will be key to ensure users understand their responsibilities and the consequences for not meeting regulatory standards.
As the technology and uses continue to advance, catastrophic loss examples will likely arise in the future. I am hopeful that the new FAA regulation will be a useful tool to mitigate the unknown risks to both drone operators and third party premises owners that might be exposed to drone-related accidents.