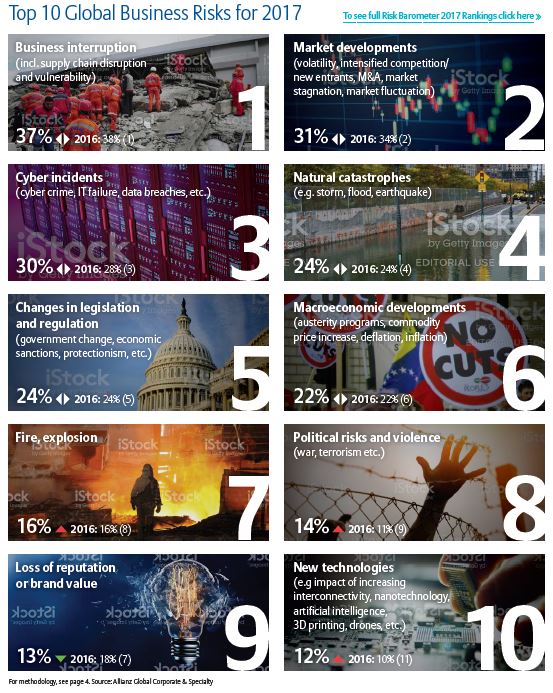
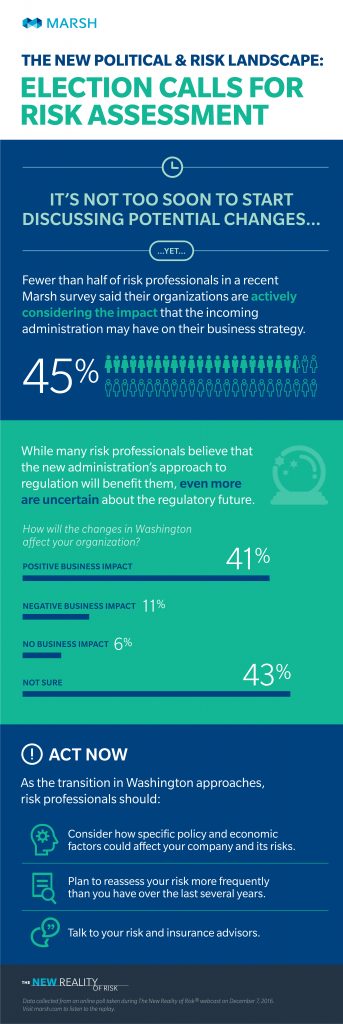
What do organizations really know about their relationships with their vendors?
It’s a question that most companies can’t answer, and for many, that lack of knowledge could represent increased risk of a security breach. This year, Bomgar conducted research into vendor security on a global scale, and the findings underscore that much work remains to be done to shore up third-party security.
The 2016 Vendor Vulnerability Index report produced eye-opening results that should be a wake-up call for business leaders, CIOs and senior IT managers. The survey of more than 600 IT and security professionals explores the visibility, control, and management that organizations in the U.S. and Europe have over external parties accessing their IT networks. Some of the most surprising statistics are summarized below:
- An average of 89 vendors are accessing a company’s network every week.
- 92% of respondents reported they trusted their vendors completely or most of the time.
- 69% said they definitely or possibly suffered a security breach resulting from vendor access in the past year.
- In the U.S., just 46% of companies said they know the number of log-ins that could be attributed to vendors.
- Only 51% enforce policies around third-party access.
It’s evident from these findings that third-party access is pervasive throughout most organizations. What’s more, this practice is likely to grow—75% of the respondents stated that more vendors access their systems today than did two years ago. An additional 71% believe this number will continue to increase for another two years.
Two-thirds of those polled admit they have a tendency to trust vendors too much—confidence that should be questioned based on the results of this report. The data revealed that, while most organizations place a high level of trust in their vendors, they still have a low level of visibility into how vendors are accessing their systems.
This contradiction is not something organizations should take lightly. As noted above, 69% of respondents admitted they had either definitely or possibly suffered a security breach resulting from vendor access. An additional 77% believe their company will experience a security issue within the next two years as a result of vendor activity on their networks.
As an organization’s network of vendors grows, so too does the risk of a potential breach. For most companies, it is essential that third-parties have access to sensitive systems as a course of doing business—the question centers on how to grant this access securely.
Historically, companies have used VPNs to provide network access to third-parties.
While appropriate for the intended end-user—remote and/or traveling employees—issues arise when the scope of VPN is trusted to manage connections from external groups. If a system connected via VPN is exploited and used as a point of persistence for leap-frogging into the broader network, hackers can persist for days or months and move stealthily about the network. Companies have also seen malicious (or well-intentioned) insiders choosing to abuse their access to steal or leak sensitive information, as this is all made fairly trivial when leveraging open-ended VPN connectivity.
To balance the dual demands of access and security, companies need a solution that allows them to control, monitor and manage how external parties are accessing their systems. Rather than providing “the keys to the kingdom,” a modern secure access solution enables organizations to grant vendors and other third-parties access only to the specific systems and applications needed to do their jobs.
To ensure security, organizations should also select a secure access solution that provides video and text logs of all session activity. This allows companies to monitor how remote access is being used and, perhaps more importantly, by whom. With this technology, any suspicious activity can be immediately flagged for further investigation. In addition, these session forensics can help companies meet internal and external compliance requirements.
Another secure access best practice is to employ a password/credential vaulting solution. This enables organizations to mitigate the risk of credentials shared between privileged users, which are often the target of a threat actor. It also reduces the risk of what system administrators often think of as “the stickynote nightmare,” where a sensitive credential is written on a stickynote and stuck on someone’s monitor for all who walk by to see. Password vaulting technologies also help with the dangers posed by embedded system service accounts that have administrative privileges and are rarely rotated for fear of bringing critical business services down. A small, yet strong initiative to protect network security would include requiring every privileged user to access credentials required for elevated work via checking out of a password vault. This removes most of the challenges associated with sharing credentials as, once they are checked back in, those credentials can be immediately rotated and thus become unknown to the employee or the bad actor who may have stolen them. Incorporating multi-factor technology in order to access the password vault and other sensitive systems takes it a step further.
In today’s heightened environment, following these steps should be essential security best practices for any company allowing vendors or other third-parties to access their network.
The Vendor Vulnerability Index report suggests that companies are aware of the threats posed by ineffective management and poor visibility into vendor access. Yet, as the data shows, just slightly over half of the respondents are enforcing any policies around third-party access. In light of these findings, companies should also ensure that they are properly screening any third-parties with whom they share network access. For example, does the vendor provide security awareness training as part of their employee on-boarding process?
Asking this and similar questions will give companies a clearer picture of the vendor’s security ethos, and help them to determine if the partnership is a good fit to begin with.
In order to combat this growing vulnerability, organizations need granular control over external access. Only with such a solution in place can companies feel confident that their vendors won’t unintentionally become their weakest security link.