We have seen it all around us lately — the financial industry’s inability to guard against major data breaches.
Just last month, Citibank, the third largest bank holding company in the U.
buy flagyl online https://royalcitydrugs.com/flagyl.html no prescription
S., experienced a data breach when hackers obtained information on more than 360,000 credit card accounts of North American customers. And just last week, Morgan Stanley announced that data of 34,000 clients was lost or stolen.
According to two letters sent to clients, and obtained by Credit.com, the information [of Morgan Stanley customers] includes clients’ names, addresses, account and tax identification numbers, the income earned on the investments in 2010, and—for some clients—Social Security numbers. The data was saved on two CD-ROMs that were protected by passwords, according to the letters, but the CDs were not encrypted. The company mailed the CDs containing information about investors in tax-exempt funds and bonds to the New York State Department of Taxation and Finance. It appears the package was intact when it reached the department, but by the time it arrived on the desk of its intended recipient the CDs were missing, Wiggins said.
The Citibank breach has been referred to as the largest direct attack on a major U.S. financial institution. Since the attack, the Federal Deposit Insurance Corporation has been preparing new measures on data security, which proves to be much needed.
The financial industry has become somewhat of a laggard when it comes to data security initiatives and the risks of data theft are rising.
According to a June report by IDC Financial Insights, “As financial institutions expose more capabilities to their clients through their digital channels, they must introduce more sophisticated mitigation and control techniques at a similar pace.” The report points to mobile applications as the next new target of cyberattacks.
(Check out the next issue of Risk Management for more on this topic — online August 1st).
To approach these inevitable risks, there needs to be a change in the role and focus of enterprise risk functions, according to the IDC Financial Insights report. “Cyber risk is an enterprise risk issue, not an IT issue, and as such needs to be addressed from a strategic, cross line-of-business, and economic perspective. The CFO, not the CIO or CTO, is the most logical person to set strategies and lead the efforts required to address the cyber risk challenge.”
The following is a chart that shows that cyber risk is an operational risk component, according to IDC Financial Insights.
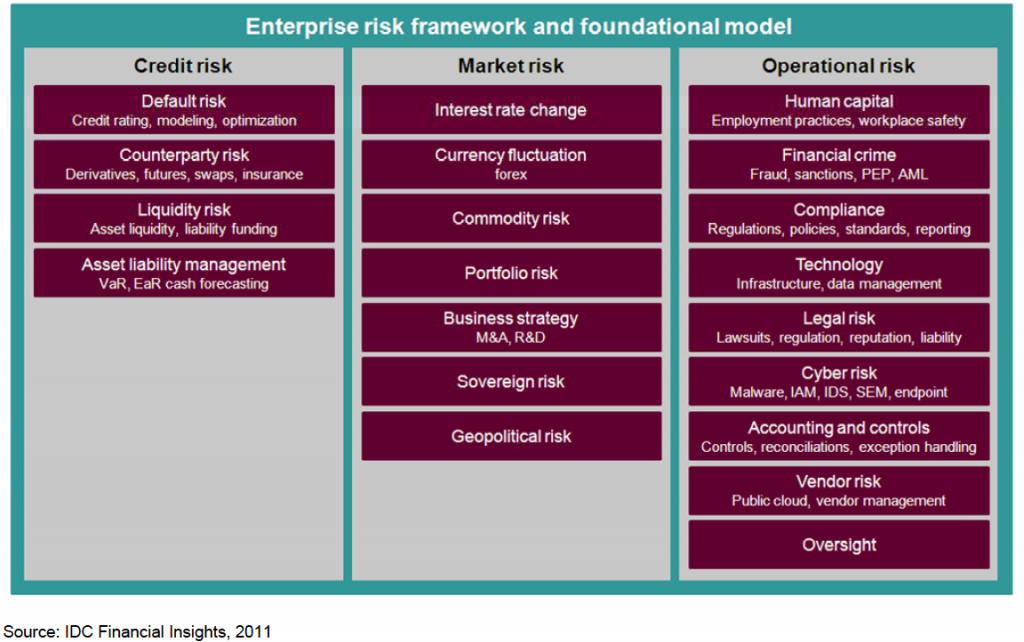
Do you agree with these findings? If not, how do you think the management of cyber risks fits within the realm of business’s risk management plan?
