During my time at the Gartner Security & Risk Management Conference last week, I had the chance to sit down with Dwayne Melancon, chief technology officer at Tripwire, an IT security software firm. I was introduced to the term risk-based security management (RBSM) and presented with a report issued by Tripwire with research conducted by the highly regarded Ponemon Institute titled “The State of Risk-Based Security Management.” Here, Melancon answers a few questions regarding the report and the state of security risk management in general.
First of all, what motivated you and your team to dig deeper into this issue and publish this report?
DM: For the past five or six years, a lot of our focus has been on trying to translate security information to compliance auditors. About a year or a year-and-a-half ago, we started to notice an influx of people talking about risk and risk management. So we commissioned the Ponemon Institute to do an independent study to find out what’s going on with risk: Where are the people, what are the challenges, what are the concerns about it? They surveyed a little over 2,000 people worldwide. The idea was to establish sort of a baseline: What’s the current state of practice in thinking and where are there gaps? When you dig into the demographics, it’s a good cross-section not just of companies, but of industries, job titles and so on.
Who is this report geared towards?
DM: I would say it would appeal to a couple of audiences. One are the CIO, CISO-level people who understand their side of technology but need to relate to other business executives outside of their world. And then the other to me is really when you get to the IT mid-management person who has to kind of focus their resources, make sure their staff’s focused on the right thing, but then communicate value up, to either their boss or their boss’ boss. I think those are the two audiences who would probably get the most out of this.
What was the most interesting aspect of the report?
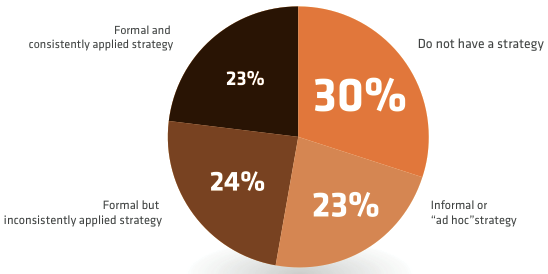
DM: A couple of things. One is that there is a lot talk and not a lot of walk yet. So, somewhere around 77 or 80% of the organizations said that risk management was important, but less than half are actually doing anything about it.
We see that a lot — people saying we need a risk management program and understand its value, but fail to implement it.
DM: Definitely. And another piece that seemed to be related to that was that there was a lot of inconsistency in who really owns the risk management program. So it was all over the map. You would think that, typically, it would be somebody senior in the organization, because most of the time, unless somebody really endorses it, it’s the “tone at the top” thing. Unless somebody at the top says, ‘this is important,’ then it becomes sort of a David and Goliath thing — some superhero in IT who decides they’re going to take this on and they get frustrated.
The term “risk-based security management.” Have you heard it used before or is this a new term in the world of risk management?
DM: We’ve heard it mentioned and when we heard it we decided that it sounds a lot like what we’re focused on. Where this came together, and I think it’s a linkage to our compliance roots, is that when we dealt with a lot of audits, scoping was really important and they always talk about the importance of a top-down risk-based assessment to figure out what’s in scope and what’s not, what’s relevant and what’s not. And one of our audit clients started describing it as risk-based security. And we said, ‘OK, that makes a lot of sense.’ Because if you have a good understanding of where the risks are, then you can align your budget, your resources, and what you report on based on risk and it makes it easier. Especially when you deal with non-technical executives. A lot of them tend to have financial backgrounds. They understand risk and they understand controls. So if you can kind of frame it in that, it’s a better starting point than trying to explain what patching is, for instance.
Was there anything in the report you found shocking?
DM: One other thing I thought was surprising is that when we asked people about data — there seems to be a dearth of metrics, a lot of people are trying a bunch of things to see what works — one thing that bothered me was that so many organizations had cost as their primary measure. I think cost is a good indicator, but it’s not a metric because you can’t drive costs and risk gets better. It just doesn’t work that way. We’ve been trying to help people understand that. It’s kind of a two-way street: What metrics are working for you, here are some things we’ve seen work.
Here is a shocking chart presented in the report: