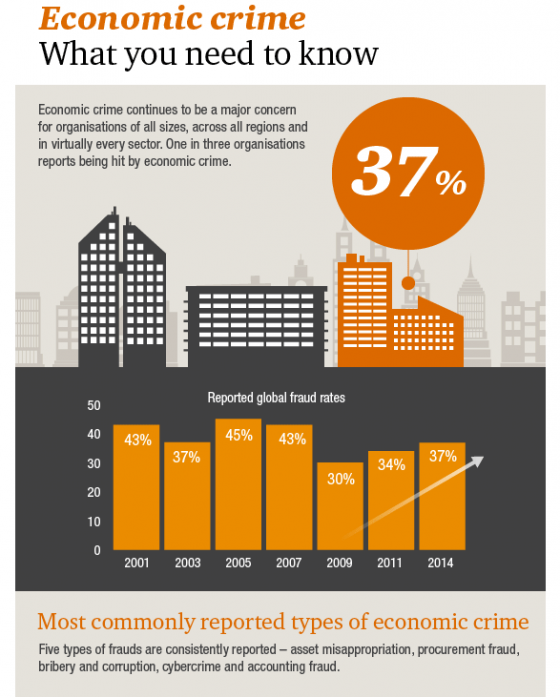
Although fraud has increased for U.S. organizations in the past two years—45% of U.S. organizations experienced fraud, compared to a global average of 37%—companies are doing less to prevent fraud than in 2011, according to a survey by PricewaterhouseCoopers.
The Global Economic Crime Survey 2014 found that the less proactive approach was consistent with the upward trend in economic crime in most fraud categories since 2011. Slightly more than half (53%) of organizations performed fraud risk assessments annually or more often, a significant drop from 70% of organizations that performed fraud risk assessments annually or more in 2011.
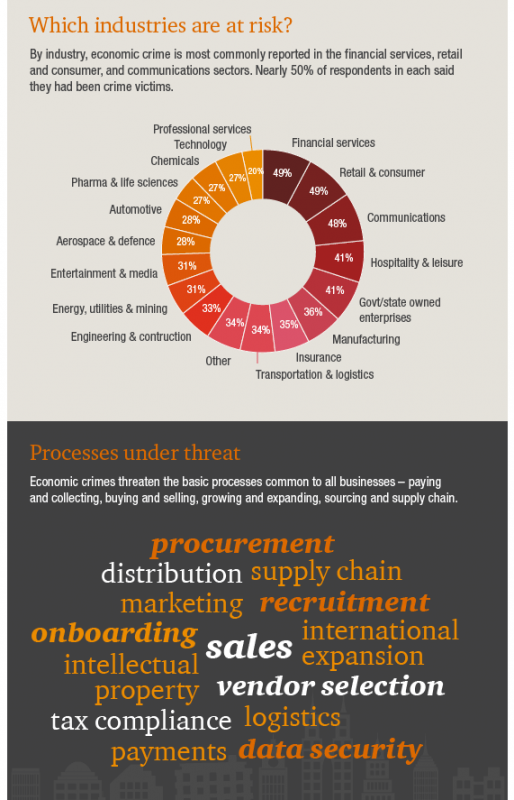
The report also found that the most serious economic crime experienced by U.S. respondents within the past 24 months was more likely committed internally (50%) than externally, (44%), but that external fraudsters are closing the gap. This trend is consistent with more organizations engaging in business opportunities in high-risk markets.
“The United States has proved to be fertile ground for domestic economic crime in recent years. Catastrophic coastal events on the Eastern and Gulf coasts have generated rampant insurance fraud that squanders taxpayer dollars and undermines community relief and reconstruction efforts. Farther inland, natural gas exploration and fracking have led to boom towns sprouting overnight in places like North Dakota, Wyoming, Utah, and Texas. Many of these towns do not have the infrastructure or governance capability to handle the influx of people, and crime, that inevitably accompany boom-town dynamics.
buy ocuflox online https://hunterdonradiology.com/wp-content/uploads/2023/10/jpg/ocuflox.html no prescription pharmacyLand lease and mineral rights agreements, zoning ordinances, permits, and licenses have become particularly vulnerable to exploitation.” PwC Global Economic Crime Survey 2014
According to the report:
• More than half of U.S. organizations that experienced fraud in the past two years reported increased occurrences.
• 67% of U.S. respondents said their organizations now have, or plan to have operations in high-risk markets, compared to only 58% of global respondents.
• 57% of U.S. respondents said their organizations pursued opportunities in markets with high-levels of corruption risk within the past 24 months, versus 38% of global respondents.
Fraud levels are climbing:
• 24% of U.S. organizations that reported economic crime experienced accounting fraud in 2009. While this dropped to 16% in 2011, accounting fraud increased to 23% in 2014.
• In 2014, bribery and corruption doubled from 2011 levels of 7%, after dropping by more than a half, to 16% since 2009 PwC said.