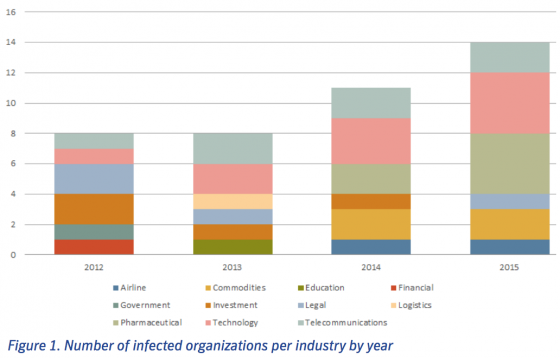
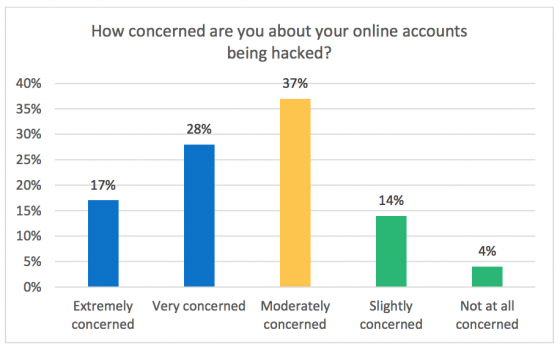
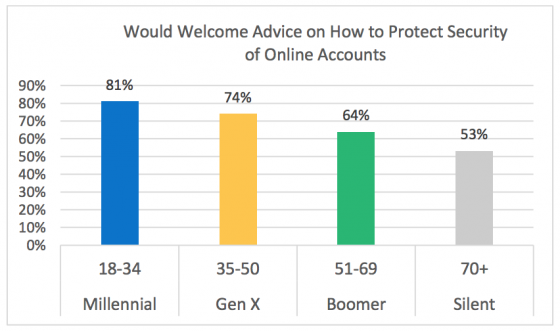
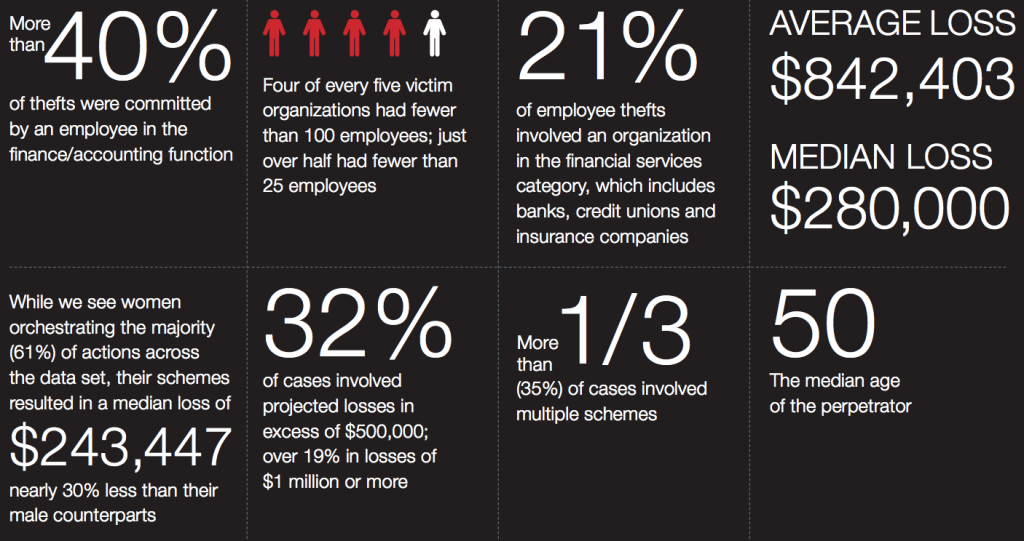
Is your company guarding against the threat of insider attack? If you responded with, “well, we do background checks when they are hired,” that’s a good start, but what about risk assessment during the course of an individual’s employment?
The 2015 Insider Threat Spotlight Report from Infosec Buddy found that less than half of companies have the proper tools to fight insider threats. And, according to 62% of security professionals, that threat has increased in the past year. The average company faces four insider attacks every year, with an estimated price tag of $500,000 each, in addition to the astronomical impact a breach can have on an organization’s reputation.
So where is the disconnect? It starts with how we assess individual risk.
The limitations of the current employee screening model
The majority of companies conduct a one-time background check on new employees before they are hired. This is a necessary part of the risk assessment process, and the majority of background screening companies are great at what they do, but this model is built on a flawed assumption: that employee risk remains constant over time.
While an employee may not have posed a risk when hired, that can change quickly. Stressful life events such as a bankruptcy, a DUI, a divorce or a negative performance review can change an individual’s risk profile in an instant. It is also important to note that traditional background checks typically focus exclusively on criminal records, failing to analyze other important information sources like human resource documents, financial records, and social media activities.
And it’s not just employees. Insider threats can come in the form of third-party contractors, vendors, suppliers, and partners – in other words, any parties with the ability to access sensitive corporate information.
A recent Accenture survey found that 76% of companies believe supply chain risk management is “very important.” The reality is that people are dynamic, and so are their motivations, which is why companies need comprehensive tools for managing personnel risk as it evolves over time.
The future of background checks: continuous identity screening
Getting proactive about managing the risks of insider threats starts with finding ways to continuously monitor personnel risk after they are brought into the organization. Advances in software offer one way to approach this challenge. Programs now exist that allow companies to actively monitor changes in personnel risk as it evolves, throughout an individual’s tenure with the company.
Continuous identity screening software automatically gathers and analyzes risk data from all relevant information sources, such as public records and HR documents, and proactively alerts risk and security managers to the most pressing threats. This allows risk managers to be continuously updated in real time, instead of traditional methods of pre-hire or periodic screening, which can uncover risk after it’s too late.
Take the example of a city bus driver who has received a recent DUI charge. Many employers would not be notified of that until a regularly-scheduled periodic background screening, if at all. Most employers rely on their employees to self-report incidents, but that does not always happen for obvious reasons. By implementing continuous screening, companies can immediately learn about that bus driver’s DUI charge, which prompts an investigation that could lead to further action.
Today’s continuous screening tools can also be customized by industry. For instance, the financial services industry may attribute more risk to an employee filing for bankruptcy than a transportation company would, whereas the healthcare industry may view odd activity on the network as a greater indicator of potential IP theft. Every industry has its own unique challenges and obstacles in meeting the mandates and regulations necessary. Tailoring the screening process accordingly can help proactively address those issues.
What does this mean for you?
By bringing together identity data from external sources like criminal and financial records with internal sources like network activity and personnel reviews, organizations can reduce the risk of insider threats. It also allows organizations to maintain compliance through a legally defensible audit trail designed to meet critical regulations such as FCRA, FTC, and EEOC.