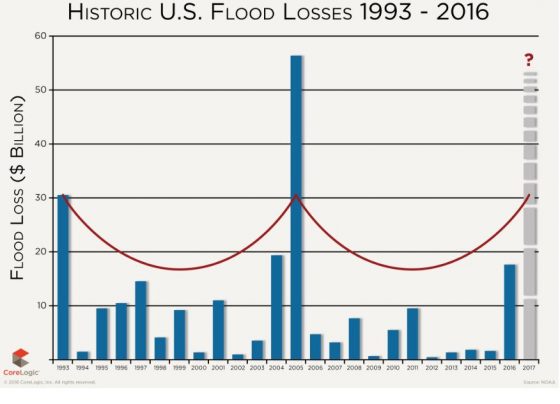
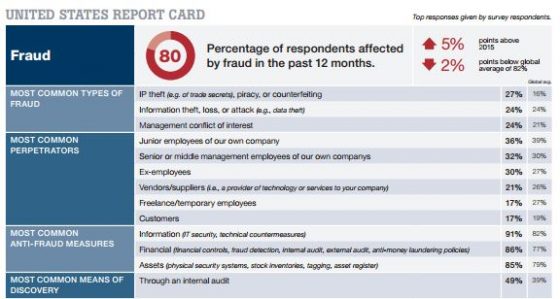
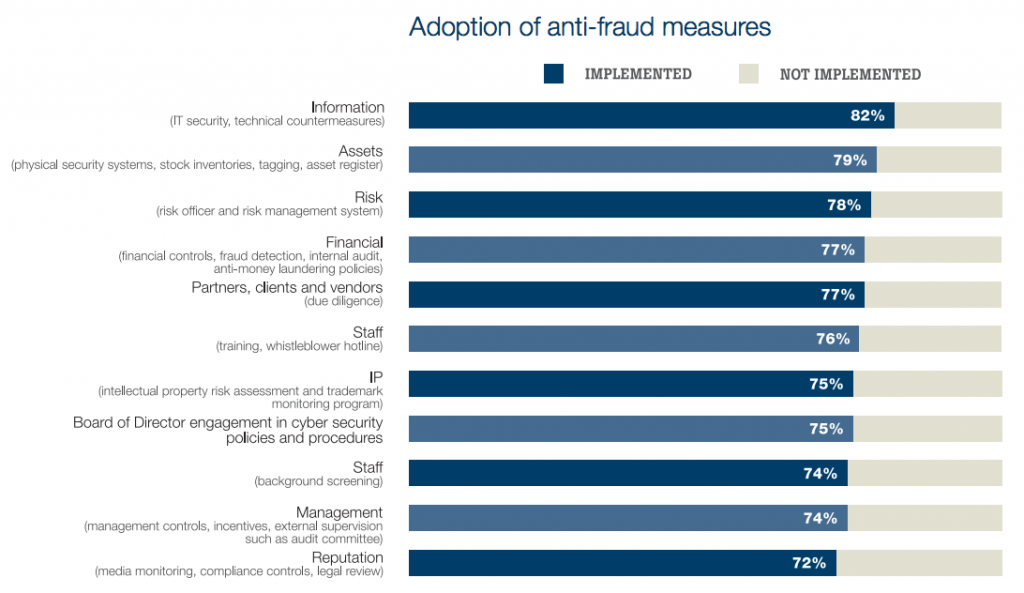
In addition to impacting the way countless organizations conduct business, the 2008 financial crisis was an awakening for regulators charged with reviewing and setting the rules that shape the way organizations assume risk. Insurance, perhaps the riskiest business of them all, did not go unscathed.
Not only are insurers responsible for managing their own internal risks, but careful calculations and guidelines are built into their business models to ensure that the risks fall within set parameters.
Regulators will argue, however, that this wasn’t  always the case.
always the case.
Own Risk Solvency Assessment (ORSA) was adopted and now serves as an internal process for insurers to assess their risk management processes and make sure that, under severe scenarios, they remains solvent.
U.S. insurers required to perform an ORSA must file a confidential summary report with their lead state’s department of insurance. The assessment aims to demonstrate and document the insurer’s ability to:
- Withstand financial and economic stress with a quantitative and qualitative assessment of exposures
- Effectively apply enterprise risk management (ERM) to support decisions
- Provide insights and assurance to external stakeholders
While ORSA is requirement for insurers, a new study by RIMS and the Property Casualty Insurers Association, Communicating the Value of Enterprise Risk Management: The Benefits of Developing an Own Risk and Solvency Assessment Report, maintains that ORSA can be used for all organizations looking to strengthen their ERM function.
According to the report:
Whether or not required by regulation or standard-setting bodies, documenting the following internal practices is a worthwhile endeavor for any company in any sector to utilize in their goal to preserve and create value:
-
Enterprise risk management capabilities
-
A solid understanding of the risks that can occur at catastrophic levels related to the chosen strategy
-
Validation that the entity has adequately considered such risks and has plans in place to address those risks and remain viable.
The connection between the ORSA regulation imposed on insurers and the development of an ERM program within an organization outside of the insurance industry is apparent.
ORSA and ERM both require the organization to strengthen communication between business functions. Breaking down those silos are key to uncovering business risk, but perhaps more importantly, is the interconnectedness of those risks.
Secondly, similar to ERM in non-insurance companies, ORSA requires risk management to document its findings, processes and strategies. Such documentation allows for the process of managing risks to be effectively communicated to operations, senior leadership, regulators and stakeholders. Additionally, documentation enhances monitoring efforts, the ability to make changes to the program and is a benefit that allows ERM to reach a “repeatable” maturity level as defined by the RIMS Risk Maturity Model.
Developing an ERM program has become a priority for many organizations as senior leaders recognize the value of having their entire organization thinking, talking and incorporating risk management into their work. Examining and implementing ORSA strategies can be an effective way for risk professionals to get their ERM program off the ground and operational.