With the Atlantic hurricane season’s official start on June 1, the time to check your buildings and existing contingency plans—or start a new one—is now, during hurricane preparedness week.
For 2017, Colorado State University’s hurricane research team predicts slightly below-average activity of hurricanes making landfall, with a forecast of 11 named storms, four hurricanes, and two major hurricanes.
The 2016 season is seen as a wakeup call, as 15 named storms and seven hurricanes formed in the Atlantic Basin—the largest number since 2012. Among the hurricanes was Matthew, a Category 4, which devastated Haiti, leaving 546 dead and hundreds of thousands in need of assistance. After being downgraded to a Category 2, Matthew pummeled southeast coastal regions of the U.S., with 43 deaths reported and widespread flooding in several states.
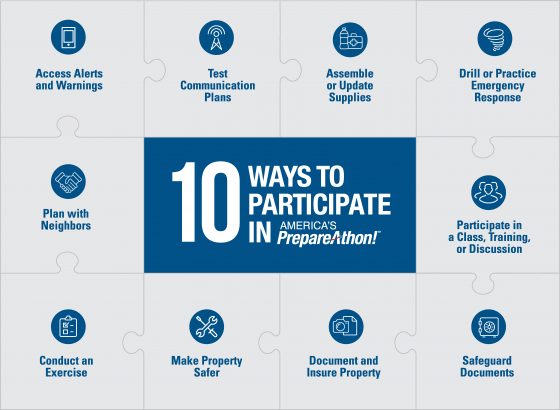
Here are 10 preparedness steps offered by FEMA:
The Insurance Institute for Business & Home Safety (IBHS) warns that small businesses are especially vulnerable. Of businesses closed because of a disaster, at least one in four never reopens.
IBHS offers these steps for preparing a business for hurricane season:
- Have your building(s) inspected and complete any maintenance needed to ensure your building can stand up to severe weather.
- Designate an employee to monitor weather reports and alert your team to the potential of severe weather.
- Review your business continuity plan and update as needed, including employee contact information. If you do not have a business continuity plan, consider IBHS’ free, easy-to-use business continuity plan toolkit for small businesses.
- Remind employees of key elements of the plan, including post-event communication procedures and work/payroll procedures. Make sure all employees have a paper copy of the plan. Review emergency shutdown and start-up procedures, such as electrical systems, with appropriate personnel, including alternates.
- If backup power such as a diesel generator is to be used, test your system and establish proper contracts with fuel suppliers for emergency fuel deliveries.
- Re-inspect and replenish emergency supplies inventory, since emergency supplies are often used during the offseason for non-emergency situations.
- Test all life safety equipment.
- Conduct training/simulation exercises for both your business continuity and emergency preparedness/response plans.
Interstate Restoration has a day-by-day list of steps for business storm preparation, based on NOAA recommendations. They include research, planning and documenting, gathering emergency supplies, checking insurance coverage and supply chain and finalizing your plan.