 The massive Thomas Fire in Ventura County has claimed another victim. CalFire Engineer Cory Iverson was killed while battling the blaze, which has so far burned 252,500 acres and destroyed about 1,000 homes and businesses, according to the federal InciWeb fire information website. One other death connected to the fire was a woman killed in a car crash while evacuating.
The massive Thomas Fire in Ventura County has claimed another victim. CalFire Engineer Cory Iverson was killed while battling the blaze, which has so far burned 252,500 acres and destroyed about 1,000 homes and businesses, according to the federal InciWeb fire information website. One other death connected to the fire was a woman killed in a car crash while evacuating.
Iverson had been with the agency since 2009 and was assigned to the Thomas Fire as part of a fire-engine strike team from CalFire’s San Diego unit.
“I know I speak for us all in saying our hearts go out to our CalFire colleagues during this difficult time.
This is a tragic reminder of the dangerous work that our firefighters do every day,” Teresa Benson forest supervisor, Los Padres National Forest said in a statement. “The Thomas Fire has many unprecedented conditions and complexities that challenge the already demanding job of fire suppression.”
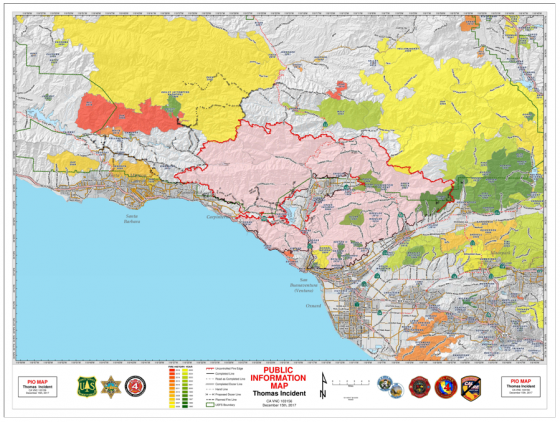
The Thomas fire broke out Dec. 4 in Ojai, northwest of Los Angeles. Strong Santa Ana winds helped it to quickly spread to the city of Ventura, according to InciWeb.
Up to 85,000 people were impacted by power outages and surges in the Santa Barbara area, according to the Southern California Edison utility company. Santa Ana winds are expected to continue on Friday and through the weekend, and could reach up to 30 miles per hour in some areas. Ventura County, northwest of Los Angeles, has ordered mandatory evacuation of a portion of the county.
The Thomas fire has also taken a toll on agriculture, which is a billion industry in California employing more than 400,000 people in the state.
The wildfire struck the largest avocado- and lemon-producing region in the United States. A 200-acre farm lost 80% of its avocado crop, according to the New York Times. Avocado orchards are more vulnerable because of their location near hillsides in the path of the fire.
Consumers are unlikely to see a surge in the price of avocados from the fire because most avocados bought in the United States are grown in Mexico. A spike in lemon prices is unlikely to occur even though Ventura County produces more than 40% of the national output, because any lost crop can be made up by increasing imports, John Krist, chief executive of the Ventura County Farm Bureau told the Times.

 Earlier this month, we reviewed how
Earlier this month, we reviewed how  5. In fact, not only is failing to prepare for an attack or breach risky, it’s foolish, Kathleen McGee, internet & technology bureau chief for the Office of the Attorney General of the State of New York said in Monday’s opening address. She added that not reporting a breach in a timely fashion has its own set of legal and reputational risks, referring to
5. In fact, not only is failing to prepare for an attack or breach risky, it’s foolish, Kathleen McGee, internet & technology bureau chief for the Office of the Attorney General of the State of New York said in Monday’s opening address. She added that not reporting a breach in a timely fashion has its own set of legal and reputational risks, referring to