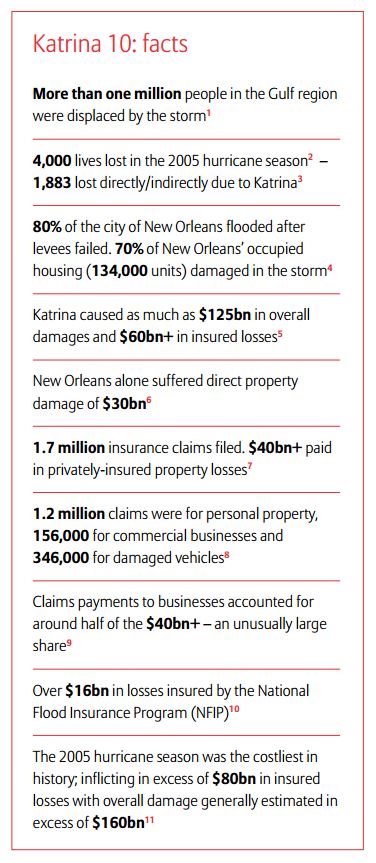
Hurricane Katrina, which pummeled the Gulf Coast of the United States 10 years ago on Aug. 29, has proven to be the deadliest and costliest disaster on record. The 2005 Atlantic hurricane season was the most active in recorded history with more than 30 tropical and subtropical storms, including 15 hurricanes.
According to the study, Hurricane Katrina 10: Catastrophe Management and Global Windstorm Peril Review by Allianz Global Corporate & Specialty, it was predicted that hurricanes would become more frequent and intense after 2005, however, “In reality, the exact opposite has occurred,” Andrew Higgins, technical manager, Americas at Allianz Risk Consulting explained in the report. Instead, there has been a reduction in Atlantic hurricane activity during the last 10 years, with 2013 seeing the fewest Atlantic basin hurricanes since 1983. “These results illustrate the fact that we do not fully understand the complex climate variables that affect hurricane activity,” he said.
Because Katrina’s impact was so devastating and widespread, many changes have since been made. New Orleans has built a new system of levees, for example. Flooding caused by Katrina revealed the state of the levee systems in the U.S. to be substandard and in need of repairs estimated at $100 billion,the National Committee on Levee Safety found. “There are many levee systems throughout the U.S. that would reveal similar deficiencies if subjected to the same level of scrutiny as those in New Orleans,” according to the study.
“Katrina will always be remembered as an extraordinary natural disaster that affected millions of individuals and businesses and left an indelible impact on the global insurance industry,” Hugh Burgess, head of corporate lines at AGCS, said in a statement. “Even without considering the influence of climate change, the prospect of increasing losses due to storms is more of a result of continued economic development in hazard-prone developed coastal areas. Preparedness limits windstorm exposure and Katrina has taught us many lessons on this front.”
Top lessons from Hurricane Katrina:
1. Storm surge impact and risk modeling
“Storm surge modeling prior to Katrina essentially assumed that the height of the storm surge was a function of the maximum sustained winds,” Higgins said. “Katrina clearly showed that there are other factors that affect storm surge height… We have learned that in addition to wind speed, the physical size of the hurricane can affect the storm surge. Camille’s hurricane-force winds extended 60 miles from the storm center, while Katrina’s extended 120 miles. The larger size of Katrina was a major factor in pushing more water onto the shore.”
2. Flooding threat
The flooding caused by Katrina showed that the conditions of the levee systems in the U.S. are very poor. “The 2013 Report Card for America’s infrastructure developed by the American Society of Civil Engineers rates the levees in the U.S. as a D-,” Higgins said.
3. Wind damage prevention
Substantial wind damage occurred to structures that experienced hurricane force winds from Katrina, despite the fact that the recorded wind speeds were less than the wind design speeds. So what happened? “Most of the wind damage occurred to the building envelope,” Higgins explained. “That includes the roof covering, walls and windows. If the building codes had been strictly followed, the wind damage would have been greatly reduced. Poor workmanship and a lack of knowledge were the primary culprits.” He added, “Today, the Gulf Coast is in a better position to withstand the effects of a hurricane due to better education, improved construction guidelines and increased third party inspection.”
4. The importance of business continuity
After widespread catastrophes businesses typically relocate, meaning the client base can diminish until recovery progresses. The key to recovery is to establish a plan in advance that identifies clear priorities for attention to crucial operations, so the business can get back up-and-running as quickly as possible.
5. Insurance coverage issues
While insurance claims settlement levels from Katrina were high, it’s imperative to know what’s protected ahead of time. Many insureds were surprised to find out they were not covered for storm surge losses, the main coverage issue resulting from the storm. Whether damage was caused by wind or water became a key focus of post-Katrina litigation.
6. Unexpected impact of demand surge
Demand surge is a post-catastrophe complication which can have not only catastrophe-related consequences in terms of rising prices due to a shortage of available goods, but other loss consequences as well. For example, a shortage of American-made drywall because of the demands of rebuilding led to a significant increase in imports of defective drywall manufactured in China. This resulted in a number of environmental issues and eventual litigation, particularly in the storm-affected states of Florida and Louisiana.
Allianz concluded that businesses need to start early to prepare for the worst-case scenario. “Businesses need to be sure to have tested business continuity plans and especially communications cascades in place and have insurance policies at a safe location,” advised Andreas Shell, Head of short-tail claims at AGCS. “Creating a separate booking account to which businesses can record hurricane-related damages to easily identify the loss incurred can also help.”
Terry Campbell, regional claims head, Americas at AGCS noted that every company should take these steps to ensure the claims settlement process runs as smoothly as possible after a windstorm event: “Follow the protocol outlined in the catastrophe response plan. If there isn’t one in place, one should be immediately developed for that event. Ensure there is adequate staff to respond and that there is ongoing communication to include scheduled meetings to discuss progress as well as issues, problems etc. These can be done as frequently as necessary,” he said.