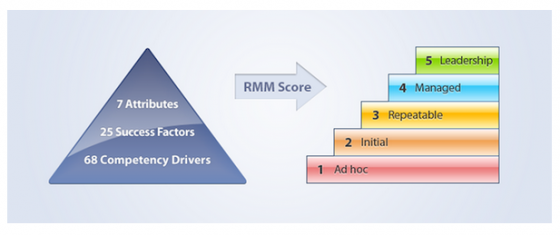
After the last article, which discussed the first two attributes of the RIMS Risk Maturity Model (RMM), ERM Based Approach and ERM Process Management; our focus here is on the third attribute, Root Cause Discipline.
Root Cause Approach
In Washington, D.C., officials tried, but were nearly helpless in stopping the deterioration of the Lincoln Memorial. Rather than address the damage with costly repairs, they instead traced the concern back to a root cause. Deterioration was caused by the high powered hoses needed to clean the building—which were necessary because the building was an attractive home for birds.
Birds were drawn to a very dense population of insects, which were attracted to the bright lights of the memorial.
So how do you stop the Lincoln Memorial from deteriorating? You dim the lights.
The root cause methodology provides clarity by identifying and evaluating the origin of the risk rather than the symptoms. Unveiling the triggers behind high level risk and loss events point to the foundation of where an organization is vulnerable.
buy eriacta online https://galenapharm.com/pharmacy/eriacta.html no prescription
Uncovering, identifying and linking risk back to the root causes from which they stem allows organizations to gather meaningful feedback, and move forward with accurate, targeted mitigation plans.
To illustrate an example in a business environment, consider the risk of inadequate training. Within an organization, there may be multiple departments experiencing risk regarding their training policies, procedures and documentation, yet each area is likely to be recording and recognizing this risk in its own way. The result is an extensive amount of information recorded in spreadsheets that requires time and energy to sort and sift through. By identifying the root cause, a risk manager can expose the underlying commonality between departments and their concerns, allowing more effective identification and mitigation of systemic risk.
Applying root cause to your current approach
To integrate this type of approach to an enterprise risk management (ERM) program, you must first identify the root cause foundation of your organization. The RMM is built on five root cause categories which cover all enterprise risks:
- External – risk caused by third-party, outside entities or people that cannot be controlled by the organization
- People – risks involving employees, executives, board members and all those who work for the organization
- Process – risks that stem from the organizations business operations including transactions, policies and procedures
- Relationships – risks caused by the organization’s connections and interactions with customers, vendors, stakeholders, regulators or third parties
- Systems – risks due to theft, piracy, failure, breakdown, or other disruption in technology, plant, equipment, facility, data or information assets
Understanding which core area of the organization a risk stems from provides the ability to effectively understand and mitigate the risk. For instance, theft from an external third party is very different than theft from an internal employee, and will thus have a very different response and mitigation strategy.
One strategy would require an investment in IT or infrastructure, while the latter would need an HR policy change or new ethics program.
Looking for an example of root cause? Download our complimentary Risk Assessment Template.