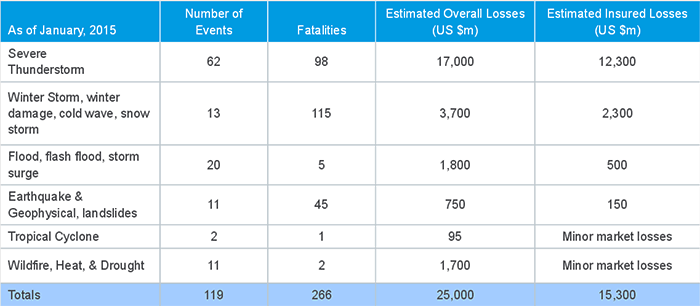
Despite predictions of a “historic” snowstorm this week, the Northeast – and the insurance industry – largely dodged the blizzard bullet. Over the past 20 years, winter storms have caused an average of $1.2 billion in insurable losses every year, the Insurance Information Institute reported. Last year’s polar vortex and significant snow accumulations came with a price tag between $15 and $50 billion, and winter weather caused $3.7 billion in overall losses, of which an estimated $2.3 billion was insured, according to MunichRe.
Ahead of what could have been record snow, seven states preemptively declared a state of emergency for what some dubbed Winter Storm Juno. Authorities shut down many major cities, canceling thousands of flights and closing major roads and mass transit systems.
Though Boston was pummeled by about two feet of snow, New York City and most of the region emerged relatively unscathed.
“We think the economic impact of the storm is going to be relatively small,” said Evan Gold, senior vice president at weather advisory firm Planalytics. “We’re estimating at about 0 million, and that’s simply based on the duration of the storm, the timing of the storm and the population centers that are impacted.”
Others estimate the cost may be closer to $1 billion, considering the lost business, wages and taxes, and snow removal costs. According to a new report from City Comptroller Scott Stringer, in the past 12 years, every inch of snow cost New York City an average of $1.8 million to remove. From 2003 through 2014, the city spent $663.2 million just to clear the snow. Lighter snowfall actually takes a greater toll per-inch. “It’s a lot more expensive on a per-inch basis when we get a little snow because we have startup costs and we have fixed costs. We have to have plows and salt,” Stringer said. As a result, the city saw 55.5 inches of snow in 2003 and paid $740,000 per inch in cleanup costs, while the city had 6.8 inches of snow in 2012 and paid $4 million per inch.
In a press conference on Tuesday, New York Governor Andrew Cuomo shrugged off the financial implications of preparations for and recovery from Juno, calling it one of the “costs of doing business.” He explained, “We factor that in—things like snow removal, salt purchases, overtime for crew to handle storms, these are factored in the budget and this was not exceptional to that process.”
The cost of overpreparation is hefty, however, and it primarily falls upon the public. A one-day storm in Massachusetts costs the state economy about $265 million, while the total cost in New York is around $700 million, according to the Boston Globe. A significant portion of that is due to lost wages for hourly workers, who tend to be hit the worst by snow-related shutdowns.
Travel cancellations have a similar impact.
According to research firm masFlight, it costs an airline about ,000 to cancel a typical domestic flight on a full-size jet, but the total tab for all the passengers who were supposed to be on board is about ,000, due to the additional costs of lodging and meals.
More than 4,700 flights were cancelled Tuesday after about 2,800 on Monday ahead of the storm, CNN reported. Amtrak also suspended service between New York and Boston because of the weather.